Researchers from cybersecurity firm Abnormal Security observed threat actors spreading the BazarLoader/BazarBackdoor malware via website contact forms rather than typical phishing emails to evade detection by security software. The backdoor malware is developed by the TrickBot group and has been under active development for some time. The BazarBackdoor malware is usually spread through phishing emails that include malicious documents that download and install the malware. However, as secure email gateways have become better at detecting these malware droppers, distributors are moving to new ways of spreading the malware.
According to Abnormal Security, the recent distribution campaign was active between December 2021 and January 2022, targeting corporate victims with BazarBackdoor. The aim was to deploy ransomware or Cobalt Strike. In one of the cases, the attackers used a corporate contact form on the website, where they posed as employees of a Canadian construction firm requesting a product supply quote.
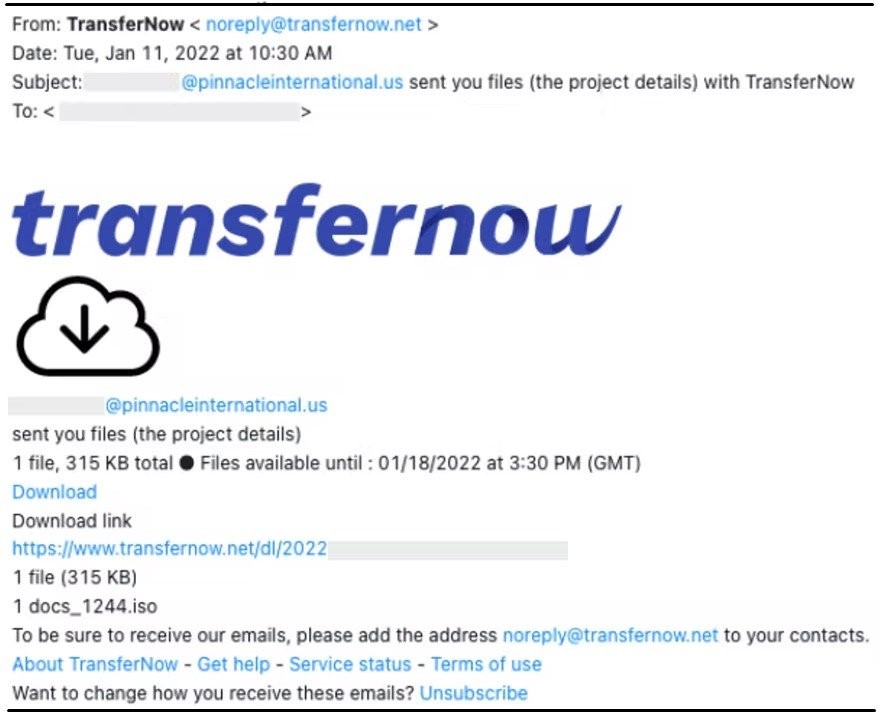
After a company representative responds with the quotation, the attackers send back a malicious ISO file attachment in an email, meant to be relevant for the negotiation. To avoid any possible security alerts, the attackers used file-sharing services TransferNow and WeTransfer to send these malicious files.
The ISO archive attachment has a .lnk file and a .log file to avoid anti-malware detection by adding the payloads into an archive and the user may manually extract them after being downloaded. The .lnk file has a command instruction that opens a terminal window using the existing Windows binaries. It subsequently loads the .log file, which is a BazarBackdoor DLL. After being loaded, it is injected inside the svchost[.]exe process and contacts the C2 server to receive commands for execution.
Conclusion
The attackers behind BazarBackdoor are using contact forms to improve the credibility and legitimacy of their attacks. Website admins are suggested to stay alert whenever receiving suspicious emails from unknown sources.





