According to Indian cybersecurity company CloudSEK, a threat actor used passwords for one of its staff’ Jira accounts to access its Confluence server.
While some internal data from its Confluence wiki was stolen, comprising images of the product dashboard and the identities. And purchase orders of three customers, CloudSEK claims the intruders didn’t compromise company databases.
“We are looking into a deliberate cyberattack on CloudSEK. Our confluence pages were accessed by someone who had access to an owner’s Jira password, “Rahul Sasi, the CEO, and creator of the business said on Tuesday.
Instead, the threat actor might access internal and training papers, and Confluence pages. Also Jira-attached open-source automation scripts and use the stolen Jira credentials.
Threat actor claims to have access to CloudSEK’s network
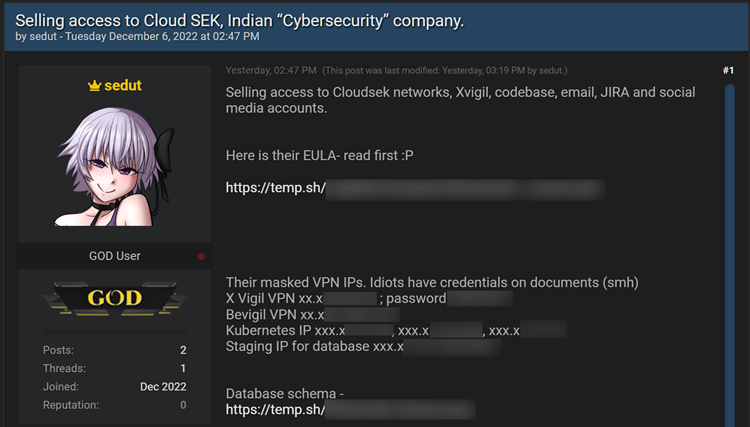
On various hacker sites, a threat actor going by the handle “sedut” is currently offering accessibility to CloudSek’s “network systems, Xvigil, codebase, email, JIRA, and social media accounts.”
They also published screenshots of CloudSEK’s dashboard, purchase orders, and screenshots of the database structure and credentials for users used to scrape the Breached and Cross-site scripting hacking forums, as well as guidelines on how to access various internet crawlers.
The threat actor is offering to sell the codebase, employee/engineering product manuals, and the purported database for CloudSEK for $10,000 apiece.
Sasi noted on Wednesday that “all the screenshots and alleged access to the malicious attacker linked back to JIRA Tickets and private Confluence pages.”
The statement reads that even the images of Elastic DB, the MySQL SQL database, and XVigil/PX came from training materials kept in JIRA or Confluence.
The unnamed cybersecurity outfit is the main suspect
Sasi alleges in an updated blog article that another cybersecurity firm well-known for monitoring dark web developments may be responsible for the intrusion. CloudSEK has already narrowed its circle of possibilities.
The CEO of CloudSEK claims, “We assume a renowned Cyber Security organization involved in Dark web monitoring is responsible for the attack.”
The attack, indicators point to a perpetrator with a well-known history of employing strategies similar to those previously noticed.
A corporate spokeswoman declined to disclose any information on the security company responsible for the CloudSEK hack.
We made the information public as soon as we learned that CloudSEK had been the subject of a targeted attack. Now, in the spirit of full disclosure, we are revising our blog post to reflect our new information.




