The CISA and the FBI have delivered a joint CSA (joint Cybersecurity Advisory) on the ransomware known as “Cuba ransomware” as a component of the latest #StopRansomware mission to scatter ransomware data for network safeguards. Despite being designated “Cuba,” the ransomware and its makers are unrelated to that country. As per reports, the latest warning is an update to an FBI Streak notice from December 2021. Accordingly, this warning incorporates refreshed strategies, methods, and methodology (TTP) and marks of give and take (IOCs).
CISA and the FBI have noticed that the quantity of US-based associations impacted by ransomware has multiplied since the previously mentioned FBI Streak notice. There might be a connection between the culprits of the Cuba ransomware, the RomCom Rodent (remote access Trojan). And the Modern Government operative ransomware, as indicated by free and open-source reports.
Cuba ransomware 101
Regardless of the moniker, the dangerous entertainers who made the Cuba ransomware haven’t shown any affiliations or affiliations with the Cuban Republic.
Windows infection called Cuba ransomware was found in late 2019. It was made in C++. Like other ransomware associations, it targets associations in the US in the accompanying five basic framework areas: basic assembling, monetary administrations, government offices, medical care, general well-being, and data innovation. Its alarming statement entertainers additionally utilize twofold blackmail strategies. The broken website, which approaches Pinnacle, an internet-based program that empowers mysterious web perusing, contains the entirety of the taken individual information.
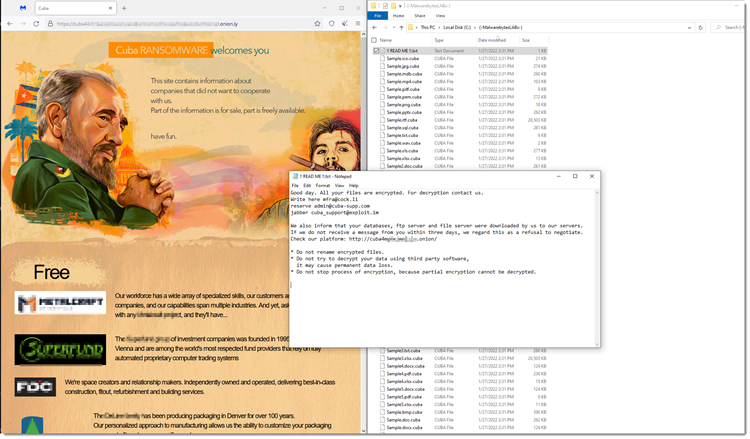
(Source: Malwarebytes Threat Intelligence Team)
Spam crusades — messages conveyed to organizations without a particular point — are how this malware contaminates target organizations. The malware downloader Hancitor has been identified as dropping the Cuba ransomware in later assaults (Chancitor).
A Word report with risky macros can be downloaded and opened through the spam email’s download connect. This report extricates and dispatches Hancitor if clients desire to empower the large scale when mentioned. This malware collaborates with its order and control (C2) server to download various apparatuses, empower horizontal development, and concentrate information.
The Cuba ransomware is then dropped and installed using PowerShell or PsExec.
The Cuba ransomware has previously been utilized in various eminent episodes. It occurred in February 2021 and affected Washington and Californian urban communities and associations. It likewise impacted the usually utilized installment processor AFTS. In a phishing effort in Oct’2022, Cuba ransomware danger entertainers professed to be the press office of the General Staff of the Ukrainian Military. The danger entertainers communicate in Russian, as per Profero, an organization within a fast occurrence reaction. And are engaged in talks between Cuba ransomware casualties and assailants.
Mitigating Cuba ransomware attacks
- To reduce the probability of an assault from the Cuba ransomware, CISA, and the FBI distributed alleviations for network protectors to stick to. The following are a couple of models:
- If you still need to get one, create and carry out a recuperation methodology to keep duplicates of important and secret information.
- In any event, the Public Organization for Rules and Innovation (NIST) norms must be trailed apparently that utilize passwords.
- On all records, particularly those that approach indispensable frameworks, empower multifaceted validation (MFA).
- Ensure your product is totally fixed and refreshed to the latest forms.
- Review accounts, considering those with executive freedoms closely, and change control settings as required.
You might peruse the thorough and broad rundown of proposed alleviations on this page. On that page, you can likewise track down an assortment of IOCs (partnered documents, email addresses, a Babble address, IP addresses, Bitcoin wallets, and payment notes), as well as Miter ATT&CK techniques.





