In order to steal victims’ personal information and login credentials, a new variant of the Drinik Android malware targets users of 18 Indian banks while disguising itself as the nation’s official tax management app. Drinik Android virus targets users of Indian banks.
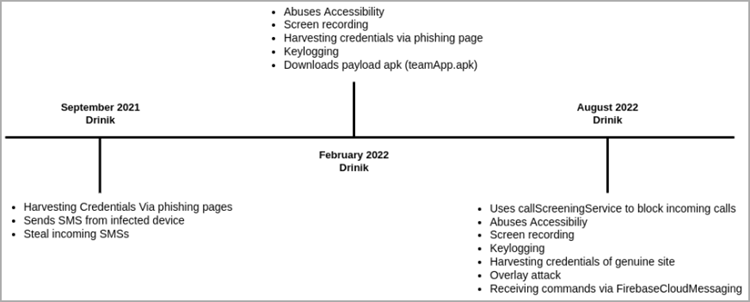
In September 2021, Drinik, an SMS thief that has been circulating in India since 2016, gained banking trojan characteristics that target 27 financial institutions by sending victims to phishing URLs.
The malware’s makers have transformed it into a full Android banking trojan with screen recording, keylogging, exploitation of accessibility services, and the capacity to conduct overlay attacks, according to analysts at Cyble who have been monitoring the situation.
Identity theft on legitimate websites
The iAssist, an APK file that is an official tax administration tool of India’s Income Tax Department that contains the most recent iteration of the malware. Drinik Android virus targets users of Indian banks.
Upon installation, it demands access to read the user’s call history, read and write to external storage, and receive, read, and send SMS.
The user then gets a prompt to grant permission for the app to (ab)use the Accessibility Service. If allowed, it turns off Google Play Protect and makes advantage of it to record the screen, record keystrokes, and execute navigational motions.
Instead of loading phishing sites as previous iterations did, the programme eventually opens the real Indian income tax website via WebView and then steals user credentials by recording the user’s screen and employing a keylogger.
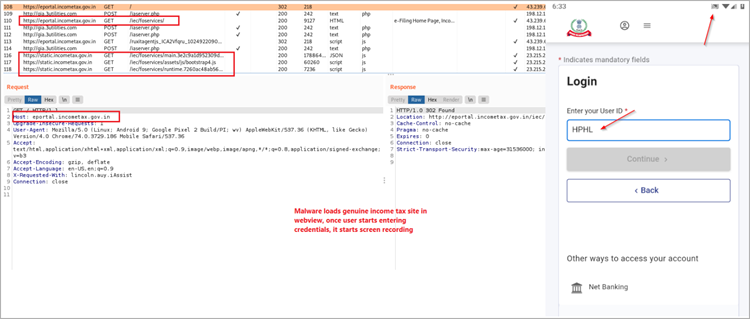
In order to confirm the validity of the exfiltrated information (user ID, PAN, and AADHAR), Drinik will additionally examine whether the victim arrived at a URL that signals a successful login.
At this point, the victim is presented with a phoney dialogue box claiming that the tax authority has determined they are entitled to a refund of Rs 57,100 ($700) as a result of prior tax calculations errors and invites them to click the “Apply” button to do so.
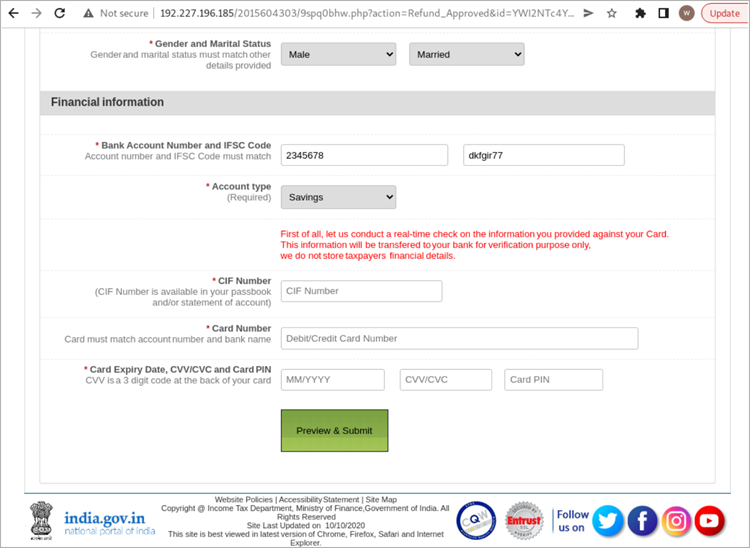
The victims are then directed to submit financial information, such as account numbers, credit card numbers, CVVs, and card PINs, on a phishing page that is a copy of the legitimate Income Tax Department website.
Focusing on banks
Drinik continuously scans the Accessibility Service for events pertaining to the targeted financial apps, such as their apps, in order to target the eighteen banks.
One of the biggest banks in the world, SBI (State Bank of India), which has 22,000 branches and serves 450,000,000 customers, is among the targeted banks.
In the event of a match, the malware seizes user credentials from keylogging data and sends them to the C2 server.
Drinik takes advantage of the “CallScreeningService” during this assault to prevent incoming calls that can interfere with the login process and, consequently, the data-stealing procedure.
Drinik progressing
Even though Drinik isn’t as clever or advanced as other banking trojans, its developers regularly add elements that make it more difficult to detect in an apparent effort to make it more potent.
Drinik has a huge target audience because it targets Indian taxpayers and banking consumers, therefore any new successful feature could result in significant financial profits for the malware’s creators.
Always avoid downloading APKs from sources other than the Play Store and use biometric authentication, such as 2FA, when connecting into e-banking portals to prevent this threat.




