According to recent research from VMware, emotet delivery and evasion techniques used in recent attacks revealed, threat actors linked to the infamous Emotet virus are constantly changing their strategies. And command-and-control (C2) infrastructure to avoid detection.
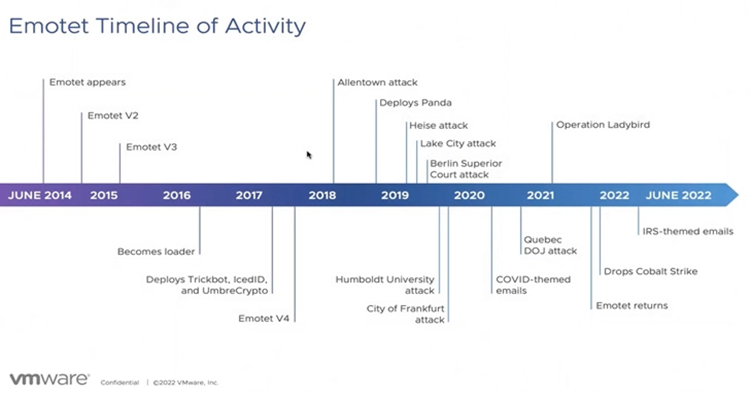
The threat actor known as Mummy Spider (also known as TA542) is responsible for Emotet, which first appeared in June 2014 as a banking trojan. Before it evolved into an all-purpose loader in 2016 that can deliver second-stage payloads like ransomware.
The Vulnerability
While the botnet’s physical infrastructure was destroyed in January 2021 as part of a coordinated law enforcement effort. Emotet reemerged in November 2021 via additional malware known as TrickBot.
The now-defunct Conti team’s deliberate resuscitation of Emotet opened the path for Cobalt Strike infections. And more recently, Quantum and BlackCat ransomware attacks.
Researchers from VMware’s Threat Analysis Unit (TAU) noted in a report published with The Hacker News. One reason the virus has been successful for so long is that its execution chain is constantly being modified.
The employment of several attack routes in an effort to remain undetected for extended periods of time is another characteristic of emoticon attack pathways.
These attacks often rely on spam message waves that transmit documents or embedded URLs that are laden with malware. Which, when opened or clicked, causes the malware to be deployed.
The Emotet payload was distributed using an Excel 4.0 (XL4) macro, and an XL4 macro with PowerShell. And a Visual Basic Application (VBA) macro with PowerShell in just three different attack sets in January 2022, according to VMware.
The Workaround
Another noteworthy aspect of several of these infection lifecycles was the misuse of the legitimate executable mshta.exe to start a malicious HTA file and then drop the Emotet virus.
Because they are signed by Microsoft and trusted by Windows, threat actors frequently use living-off-the-land binaries (LOLBINs). Including mshta and PowerShell, according to the researchers.
This enables the perpetrator to carry out a confused deputy attack, in which trustworthy tools are deceived into carrying out malevolent deeds.
A more thorough examination of almost 25,000 distinct Emotet DLL artefacts reveals that 26.7% of them were discarded by Excel documents. There have been as many as 139 unique programme chains found.
The threat actor managing two new botnet clusters called Epochs 4 and 5 has changed the C2 infrastructure, which has contributed to Emotet’s resurgence. The Emotet operation operated on three different botnets known as Epochs 1, 2, and 3 prior to the takedown.
Additionally, 10,235 Emotet payloads discovered in the wild between March 15, 2022, and June 18, 2022, utilized Epoch 5 C2 servers.
The Recommendations
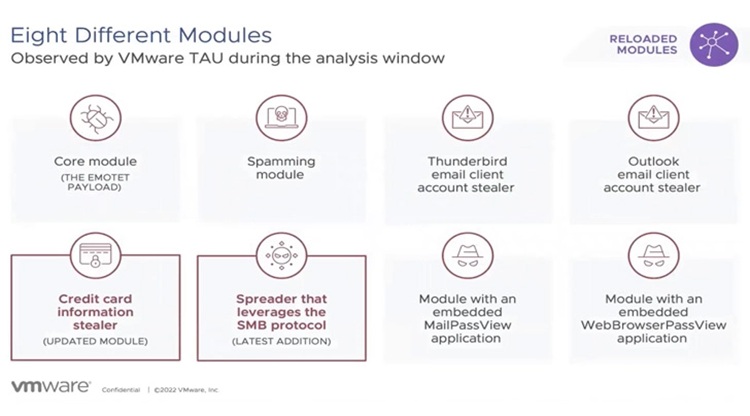
Aside from the modifications to the C2 IP addresses and execution chains. Emotet has also been observed disseminating two new plugins: one is intended to collect credit card information from the Google Chrome browser. And the other is a spreader module that moves laterally using the SMB protocol.
A spamming module and account thieves for the Microsoft Outlook and Thunderbird email clients are further noteworthy components.
The majority of the servers’ IP addresses were located in the United States, Germany, and France. In contrast, the majority of the Emotet modules were hosted in France, Singapore, Ghana, Korea, Thailand, and India.
It is advised to create network segmentation, and impose a Zero Trust model. And swap out the default authentication mechanisms with stronger ones in order to defend against attacks like Emotet.





