Executive Summary
This document examines a recent Emotet infiltration and describes the system installation of the Emotet payload. The main findings are:
- Excel macros that have been encrypted that download and run the Emotet loader.
- Regsvr32.exe was used to run the Emotet loader.
- Emotet payload with encryption included in the loader’s.rsrc section.
- The Windows service is used to maintain the Emotet payload.
- Emotet keeps improving its obfuscation and delivery methods to lessen detection.
Background
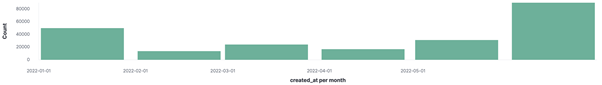
Emotet is a malware loader for Windows that is run by the cybercriminal organization TA542 (1), also known as Mummy Spider (2). Emotet was first identified in the middle of 2014 and was initially created as a banking trojan but eventually evolved into a modular malware platform with the ability to load other malware, steal information, and have spambot capabilities (1). The main method of disseminating Emotet is through phishing attempts (1). The infrastructure of Emotet was interrupted by North American and European law enforcement organizations in early 2021, which caused a pause in Emotet activities (3). However, Emotet operations restarted in the middle of November 2021. (4). Qakbot (5) and CobaltStrike are two malware families that Emotet has seen drop (6). Since emotet infections have in the past led to the deployment of ransomware, they pose a high risk (7). Analysts at EclecticIQ have tracked the distribution of Emotets in 2022. The Emotet files and network indicators that were found in EclecticIQ’s internal dataset during the first half of 2022 are highlighted in the bar graph below.
First Stage: Initial Delivery
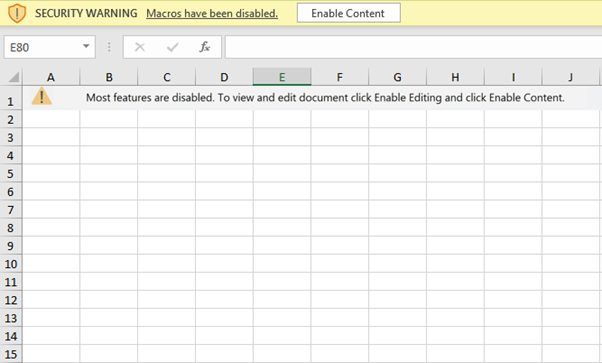
When enabled, the Microsoft Office XLS document executes an Excel 4.0 macro. Most typically, an assault starts with a spam email that contains an attachment of a Microsoft Office XLS document. The Excel macros in the XLS file are hidden. When the document is opened, the user is prompted to “Enable Content,” and once done, the macro will run.
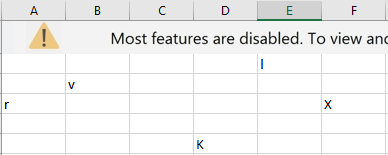
The Excel macro is obscured by the actor using a variety of techniques, making static file analysis more difficult. The publication makes use of numerous worksheets that are password-protected and have ‘CHAR’ formulas that yield text characters. The characters are printed in white font to make the sheets appear empty and are dispersed throughout the sheets in various cells (as seen in the figure).
Macro Downloads and Executes Emotet Loader
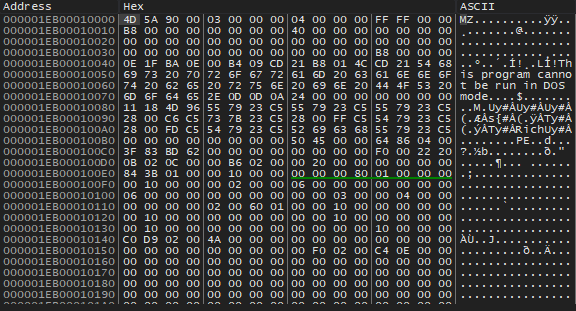
The document uses the ‘Auto Open’ method to perform the formula in the figure when macros are enabled. The macro’s functionality is revealed by this formula, which reveals four CALL and EXEC functions. The macro will then attempt to download the Emotet Loader using the URLDownloadToFileA function and save it with the “.ocx” (Active control) file extension in the current parent directory. Then it tries to use regsvr32.exe with the /S parameter to run the downloaded Emotet loader. Even if the first attempts are successful, the software makes four attempts to download and run the loader before the macro ends.
Second Stage: Emotet Loader
Decrypting and loading Emotet Payload is done by Emotet Loader. The encrypted Emotet payload is stored as an embedded resource with the name “7732” in the 64-bit DLL that serves as the Emotet loader.

The VirtualAlloc function will be used by the Emotet loader to allocate memory as it loads the encrypted payload into memory. The second parameter to the LoadResource function is the value 0x1E34 (decimal 7732), which represents the name of the encrypted payload resource. The designated memory space is filled with the decoded Emotet payload. There is a 64-bit DLL payload. The file is transferred from soci2.ocx in the HOMEPATH variable to cdiwaui.dll in the SYSTEM32 variable. Windows service is used to create persistence, and the newly created service uses regsvr32.exe to run the Emotet payload.
Conclusion
The Emotet payload enables remote access to the victim’s PC once it has been fully installed. Additional Emotet modules or malware families can be installed on the machine thanks to this remote access. Security teams may track, monitor, and find Emotet infections with the aid of the MITRE ATT&CK categorization, indicators, and YARA rule, which are all provided below.





