More than 60,000 Microsoft Exchange servers that have been publicly exposed online have yet to be fixed against the CVE-2022-41082 remote code execution (RCE) vulnerability, which is one of two security flaws targeted by ProxyNotShell exploits. These Exchange servers are vulnerable to ProxyNotShell attacks.
According to a recent tweet from the Shadowserver Foundation, a nonprofit group that works to enhance internet security, nearly 70,000 Microsoft Exchange servers were discovered to be susceptible to ProxyNotShell attacks based on version information (the servers’ x owa version header).
However, according to new data released on Monday, the quantity of vulnerable Exchange servers has reduced from 83,946 in mid-December to 60,865 on January 2nd.
These two security flaws, CVE-2022-41082 and CVE-2022-41040, are known as ProxyNotShell and affect Exchange Server 2013, 2016, and 2019.
If exploited successfully, attackers can gain arbitrarily defined or remote code execution on vulnerable servers.
Also, read A new 0-day RCE vulnerability on Microsoft Exchange Server was used in a new attack campaign.
Despite the fact that ProxyNotShell attacks have already been discovered in the wild since then at least September 2022, Microsoft has released security patches to confront the faults during the November 2022 Patch Tuesday.
GreyNoise, a threat intelligence firm, has been trying to track ongoing ProxyNotShell utilization since September 30th and gives details on ProxyNotShell monitoring activity as well as a list of IP addresses associated with the attacks.
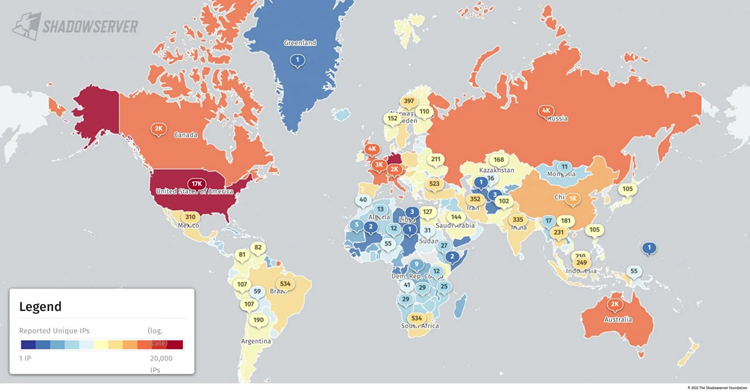
Thousands were also vulnerable to ProxyShell and ProxyLogon attacks.
To safeguard your Swap servers from attacks coming, pertain to the ProxyNotShell spots that Microsoft released in November.
While the company provided measures to mitigate, these can be circumvented by attackers, implying that it only fully patched web servers are safe from compromise.
As disclosed last month, Play malware threat actors are now employing a new exploit chain to circumvent ProxyNotShell URL rewrite mitigation strategies and gain remote code execution on susceptible servers via Outlook Web Access (OWA).
To make matters worse, a Shodan search reveals a large number of Exchange servers revealed online, with 1000s left unpatched against ProxyShell and ProxyLogon security flaws that rank among the top most exploited vulnerabilities in the world.
Exchange servers are valuable targets, as proved by the financially motivated FIN7 cybercrime group, which has developed a custom auto-attack known location as Checkmarks that is designed to breach Exchange servers.
According to advanced threat firm Prodaft, which found the platform, it scans for and tries to exploit various Microsoft Exchange remote code execution and privilege altitude vulnerabilities, including CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207.
After inspecting over 1.8 million targets, FIN7’s new framework has already been utilized to infiltrate 8,147 companies, the majority of which are based in the United States (16.7%).




