
Joint Alert About Attacks Supported by North Korea Issued by CISA, FBI, and the Treasury Department
The public and healthcare sectors are on high alert as a result of North Korean state-sponsored “Maui” ransomware attacks, according to federal authorities.
According to a federal directive, Pyongyang is using ransomware to target various healthcare and public health groups, and it is advising impacted organisations to take precautions to lessen the likelihood of a compromise.
According to the advice, hackers utilise Maui ransomware to encrypt systems hosting healthcare services such as electronic health records, diagnostic tests, medical imaging, and intranet services for medical centres.
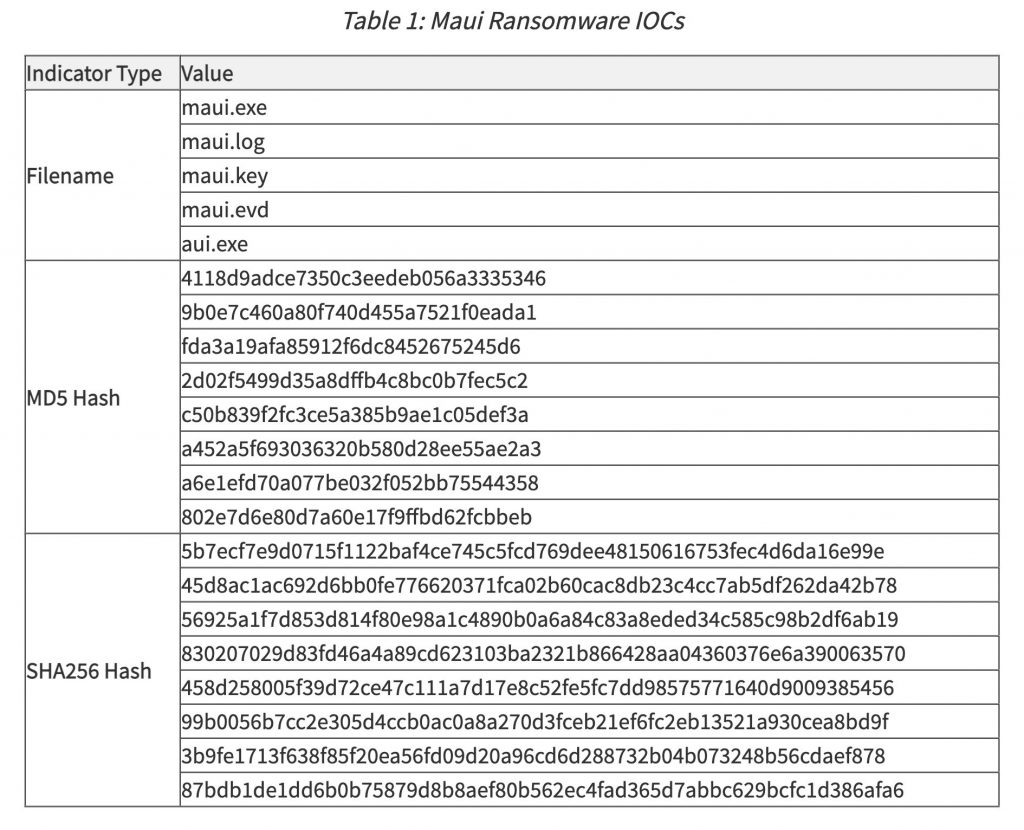
The executable file that the ransomware uses to maliciously encrypt victims’ files bears the name Maui.
Ransomware is a well-known hobby for North Korea, which uses it to collect money intended for funding the production of WMDs. According to a 2019 United Nations panel, cybercrime in North Korea brought approximately $2 billion for the hereditary communist government; this figure has since increased.
The federal government says in the advice, which was written by the FBI, Cybersecurity and Infrastructure Security Agency, and the Department of the Treasury, that the healthcare industry is a desirable target for ransomware attackers aiming for a quick payday.
The alert states that North Korean state-sponsored cybercriminals “likely believe healthcare organisations are prepared to pay ransom because these organisations provide services that are essential to human life and health.”
The executable file appears to be intended for manual execution by a remote actor, according to the industry analysis of Maui included in the alert. The remote actor communicates with the virus using a command-line interface and chooses which files to encrypt.
Risk of Sanctions
The federal government strongly advises against paying ransom. Not only does paying the extortionists not guarantee that the affected data and documents would be recovered, but it may also be against Treasury’s Office of Foreign Assets Control sanctions.
Healthcare organisations should exercise extreme caution and seek guidance before choosing to pay the Maui operators a ransom, according to Brett Callow, a threat analyst at the security company Emsisoft.
When ransomware attacks impair patient services, some organisations in the healthcare sector experience increased pressure to pay extortionists in the hopes that the compromised IT systems and data can be recovered more rapidly.
“Any payment, as the warning notes, has the serious risk of going against OFAC penalties. Even while it makes sense to contact law enforcement in instances, this is particularly crucial in these situations.”
Healthcare Sector Threats
The Health Information Sharing and Analysis Center’s chief security officer, Errol Weiss, told Information Security Media Group that CISA approached the H-ISAC in mid-June to request feedback on the draught Maui ransomware advisory.
“To determine any effects on the health sector, Health-ISAC collaborated with our Threat Intelligence Committee, a working group of cyberthreat intelligence analysts from member organisations. No members affected by the Maui ransomware could be found, “He claims.
However, he asserts that it is evident from the government’s recommendation that law enforcement authorities have located victims in the health industry.
To assist better secure the worldwide healthcare community, the information sharing organisation urges members to disclose any occurrences or information linked to the Maui ransomware as well as to follow the advisory’s advice.
According to Erick Galinkin, senior artificial intelligence researcher at security company Rapid7, Maui ransomware assaults are outdated. They resemble “good old-fashioned ransomware” assaults more closely since they encrypt files and demand payment in exchange for the key.
He claims that Maui “seems much more manual” in comparison to other sophisticated ransomware attacks like hack-and-leak strategies or ransomware with several extortion activities. Attackers choose the files to encrypt on their own and retrieve the encryption keys only before execution.
Unlike ransomware-as-a-service organisations with prominent web presences, Maui also doesn’t make a point of bragging about its accomplishments. Galinkin claims that a significant part of the reason the Maui ransomware hasn’t received as much news as the double extortion and leak gangs is that they don’t make their victims public.
It is challenging to determine how widespread the threat is because victims, naturally, are reluctant to provide information about their status as victims. The ransomware gang has reportedly been active for more than a year and has compromised a respectable number of victims, according to credible evidence.
Security company Mandiant’s Jeremy Kennelly, senior manager of cybercrime analysis, tells ISMG that his organisation has long tracked financially motivated campaigns carried out by North Korean cyberoperators on behalf of the state, and that not just organisations in the healthcare sector are at risk.
He claims that the operations show how adaptable and persistent these actors are in their efforts to earn money for the Kim government. “These activities have spanned a range of schemes, including direct bank heists, targeting cryptocurrency, and deploying ransomware,” he says.
Taking Action
The federal alert offers a long list of recommended mitigations to help healthcare and public health sector entities prevent falling victim to Maui, as well as other ransomware threats.
They include:
- Implementing public key infrastructure and digital certificates to authenticate connections with the network, including those made by medical devices and EHRs, to restrict access to data;
- Using least privileged user accounts instead of administrative ones on internal systems;
- For wide area networks, disabling network device management interfaces like Telnet, SSH, Winbox, and HTTP and, when enabled, securing with strong passwords and encryption;
- Employing technologies like Transport Layer Security to secure personally identifiable information and protected health information at the moment of collection and encrypt the data both in transit and at rest;
- Only keeping patient data on internally run, firewall-protected systems, and making sure there are plenty of backups available;
The Maui ransomware advice is the most recent warning from federal authorities regarding ransomware organisations and other malware used to target the healthcare sector.
A warning about the “return” of Emotet malware as an infrastructure-as-a-service tool used by cybercriminal groups to exfiltrate data, drop ransomware, and launch related attacks on healthcare sector entities was released in June by the Health Sector Cyber Coordination Center, or HC3, of the Department of Health and Human Services.
Reference: https://www.bankinfosecurity.com/feds-warn-healthcare-sector-maui-ransomware-threats-a-19517




