Recently, Portswigger researchers discovered new techniques for framing a website without using the iframe element when researching XSS vectors.
To include these, PortSwigger has updated the XSS cheat sheet. Researchers at Portswigger found that Google Chrome permits changing the URL of an object element using param tags, much like an iframe.
Additionally, Chrome & WebKit permits referencing an external URL in an embed tag using the “code” attribute:
<embed code=https://portswigger-labs.net width=500 height=500 type=text/html>
Although URLs with the data: protocol work and JavaScript URLs do, they all run from a null origin, making them useless for XSS, which is what the PortSwigger attempted to do. New framing techniques can still be helpful to chain attacks together or even to go around CSP.
Firefox and tabindex
In unrelated XSS news, it was claimed that Firefox now behaves similarly to Chrome with regard to the tabindex characteristics. As a result, Firefox now automatically fires events like onfocus when it didn’t before. Hooray for the growth of the attack surface! This change has now been reflected in the cheat sheet.
Search interface
A search interface for the XSS help sheet was also requested; this would make it simpler to locate vectors when a WAF is filtering particular characteristics or tags. Therefore, PortSwigger incorporated one that enables regular expression-based tag, event, and code searching.
Just read this if you don’t know what cross-site scripting (XSS) is:
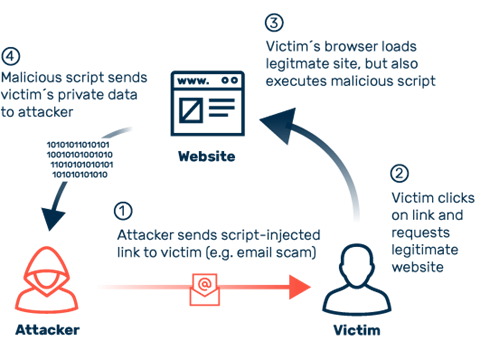
An online security flaw called cross-site scripting, or XSS, enables an attacker to tamper with how users interact with a susceptible application. It enables an attacker to get around the same original policy, which is intended to keep various websites separate from one another. Cross-site scripting flaws typically give an attacker the ability to pretend to be a victim user, execute any operations they are capable of performing, and access any of the user’s data. The attacker may be able to fully manage all of the functionality and data of the application if the target user has privileged access to it.
What is an XXS Cheat Sheet?
This cross-site scripting (XSS) cheat sheet contains many vectors that can help you bypass WAFs and filters. You can select vectors by the event, tag, or browser, and a proof of concept is included for every vector.
CSP stands for content security policy
A browser security feature called CSP seeks to reduce the impact of XSS and other types of attacks. It functions by limiting the resources (such as graphics and scripts) that a page can load as well as the ability of that page to be framed by other pages.
A response must have an HTTP response header called Content-Security-Policy with a value specifying the policy in order to enable CSP. One or more directives, separated by semicolons, make up the policy itself.