A new vulnerability called ParseThru has been identified by security experts that affects Golang-based applications and might be used to get unauthorised access to cloud-based applications.
According to a study published with The Hacker News by Israeli cybersecurity company Oxeye, “the newly identified vulnerability allows a threat actor to overcome validations under specific scenarios, as a result of the use of dangerous URL parsing mechanisms built into the language.”
Inconsistencies generated by modifications to the URL parsing logic used by Golang and implemented in the “net/url” library are the root of the problem. Before version 1.17 of the programming language, semicolons were accepted as a query delimiter (example.com?a=1;b=2&c=3). This behaviour has subsequently been changed to throw an error when a query string is discovered that contains a semicolon.
According to the release notes for version 1.17 released in August of last year, “The net/url and net/http packages used to support “;” (semicolon) as a setting separator in URL queries, in addition to “&” (ampersand).
Now, settings including non-percent-encoded semicolons are ignored, and net/http servers will record a warning to the “Server.ErrorLog” file whenever they do so. When a Golang-based public API running version 1.17 or later interacts with a backend service running an earlier version, there is a risk that a malicious actor could sneak requests with query parameters that would otherwise be denied.
Simply said, the concept is to send specially designed queries with a semicolon in the query string, which are processed by the internal service but disregarded by the user-facing Golang API.
This is also made possible by one of the ways used to obtain the parsed query string silently discarding the returned error notice.
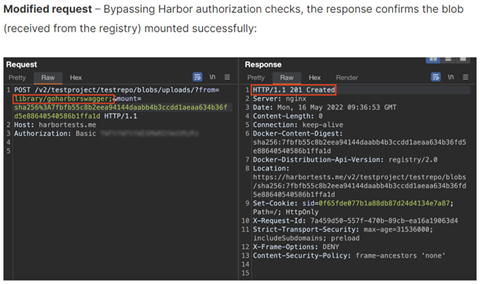
According to Oxeye, it found multiple instances of ParseThru in open-source applications including Harbor, Traefik, and Skipper that allowed users to go around security measures and take unauthorised actions. Issues were resolved after being responsibly disclosed to the relevant vendors.
The security risk associated with URL parsing is not new. As many as eight problems that resulted from confusion in URL parsing were revealed by Claroty and Snyk in third-party libraries built in the C, JavaScript, PHP, Python, and Ruby languages earlier this month.





