Hackers are making artificial websites for famous open-source and free apps to encourage malicious downloads through google search engine advertisements.
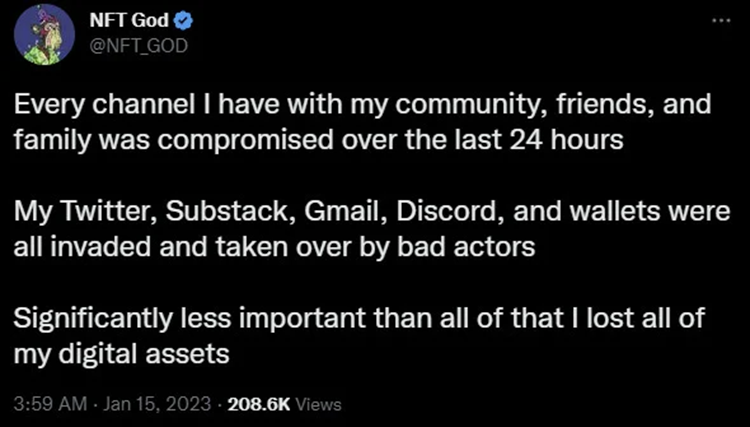
At least one prominent cryptocurrency user has claimed that the campaign allowed hacker hackers to steal all of one’s digital crypto assets and regulate their personal and professional accounts.
Over the weekend, crypto influencer Alex, also known as NFT God on social media, was hacked after launching a bogus compiled code for the Open Broadcaster Software (OBS) video recording and streaming live apps they had downloaded from a Google ad in search results.
“Nothing did happen when I clicked the EXE,” Alex authored in a Twitter thread about their weekend experience. However, friends informed them that their Twitter account had been compromised a few hours later.
Unbeknownst to Alex, this was probably an information-stealing ransomware that managed to steal their saved internet explorer passwords, cookies, Discord tokens, and cryptocurrency wallets and sent them to a remote attacker.
Soon after, Alex discovered that their OpenSea NFT marketplace account had also been compromised and that a different wallet was mentioned as the holder of one of their digital contents.
“I knew it was all over at that point. “All of my crypto and NFTs have been stolen from me,” NFT God said in a thread.
Alex quickly realized hackers compromised and controlled their Substack, Gmail, Discord, and cryptocurrency wallets.
It was reported on a massive October campaign that used over 200 typosquatting domains. Since over two dozen brand names mislead users.
Also, read malware apps Google Play.
The method of distribution was unknown at the time. Still, in December, reports from cybersecurity firms Trend Micro and Guardio disclosed that attackers were abusing the Google Ads platform to promote malicious downloads in search results.
A flurry of malicious ads in Google search results
Following the thread by NFT God, the investigation discovered that OBS is one of a lengthy list of apps that threaten actors to impersonate to promote malevolent downloads in Google Ads search results.
One example is a Google Ad search result for Rufus, a free power generator for creating bootable USB flash drives.
The risk actor registered domains that looked similar to the official ones. And copied the central role of the legitimate site up to the download section.
In one case, they used the cliched top-level domain “pro,” most likely to thrill victim interest. And entice them with the promise of a more extensive set of program features.
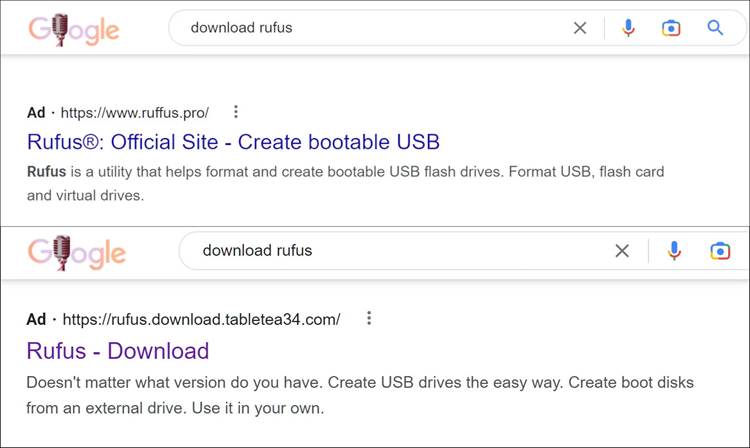
It should be noted that Rufus has no advanced variant. There is just one edition available on GitHub as a mountable or portable variant.
The malicious version’s download is routed through a data transfer service. Numerous antivirus engines do not recognize it as a threat because it is an archive bomb.
Another popular programme pranked is the message and source code editor Notepad++. The malicious actors used typosquatting to create a domain that looked similar to the official developer’s.
Security analyst Will Dormann found that counterfeit Notepad++ downloads in the sponsored section of Google search have been available from extra URLs, all files being labeled as malevolent by numerous antivirus (AV) engines on the Virus Total scanning platform.
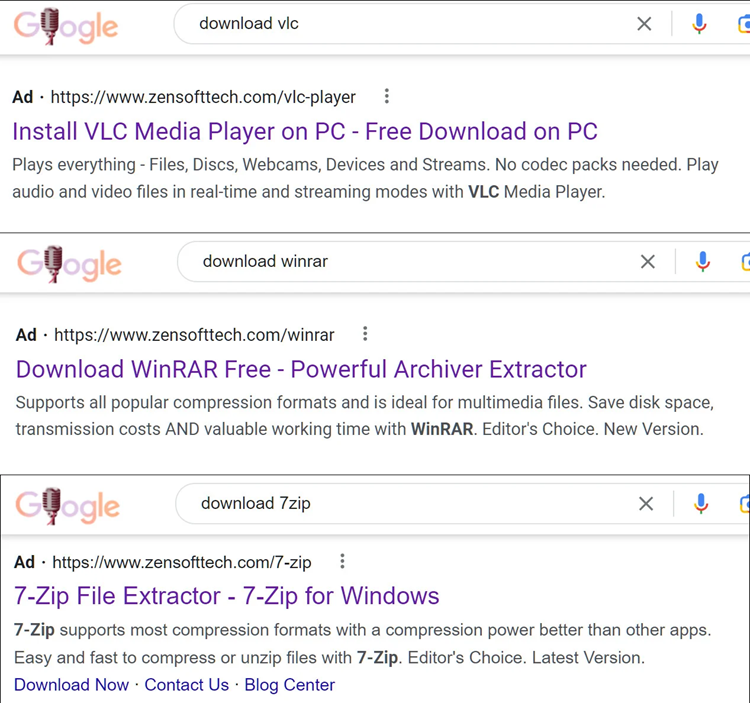
A website containing bogus application downloads distributed solely through Google Ads search results. The website impersonates Zensoft Tech, the right website design company in India.
The Malicious Downloads
Unfortunately, nothing confirmed whether the downloads were malicious; however, given that the domain is a typosquatted URL, the site prevents search engines from indexing content, and the downloads are promoted solely thru the ads in search engine results, there is a strong indication of illicit behavior.
The file compression utility companies 7-ZIP and WinRAR, as well as the widely used media player VLC, were among the apps we discovered on the website.
Several security researchers (mdmck10, MalwareHunterTeam, Will Dormann, Germán Fernández) have tool for analyzing URLs hosting malicious downloads impersonating free and open-source software, confirming that cybercriminals are increasingly luring users through sponsored Google search results.
Germán Fernández of cybersecurity firm CronUp has compiled a list of 70 realms that distribute malware via Google Adwords search results by imitating legitimate software.
The websites are clones of the standard ones and either offers fake apps or redirect to a different download location. Many include Audacity, while others include VLC and the image editor GIMP.
When looking for the open-source 3D created suite Blender 3D, one consumer almost fell for the trick. According to MalwareHunterTeam, three malicious advertisements for this product preceded the link from the official developer.
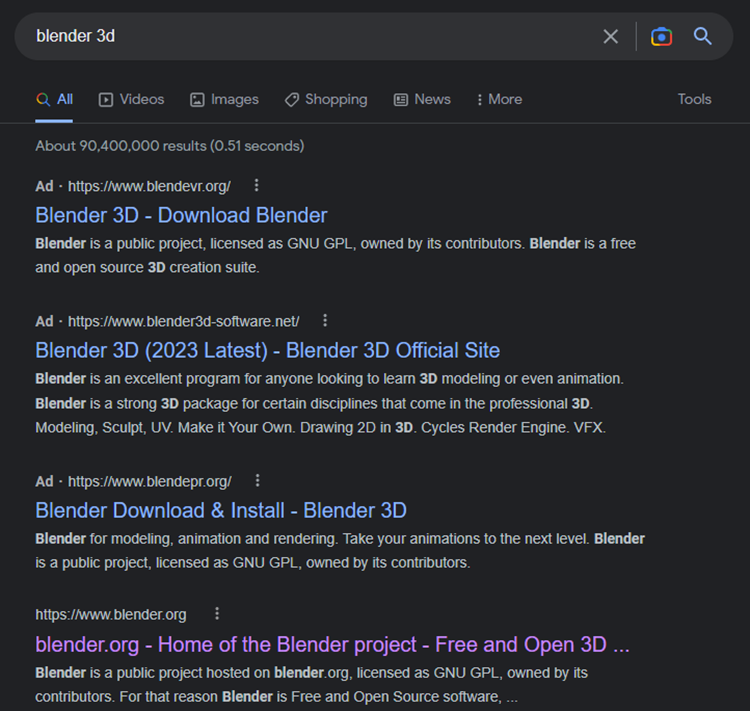
source: Nox Scimitar
When security researcher Will Dormann examined, one of the specimens was flagged as malevolent by some AV products. Then he noticed that it contained a null and void signature from the cybersecurity firm Bitdefender.
Although it was unable to verify the malware delivered in all cases. The payload, in some instances, was indeed the RedLine Stealer designers saw on the fake CCleaner site.
This malware gathers sensitive information from web browsers (credentials, credit card information, autocomplete information), system information (username, location, hardware, available security software), and cryptocurrency.
The Discoveries
Fernández discovered that one threat actor disseminated the. NET-based remote management trojan SectoRAT, also known as Arechclient2, through bogus downloads for the Audacity digital audio editor.
The researcher also discovered the Vidar info-stealer supplied via malicious Blender 3D downloads advertised in Google Search. Vidar is primarily interested in stealing sensitive information from browsers but may also steal cryptocurrency wallets.
Some of these findings were shared with Google. A corporation representative said that the platform’s policies are created and imposed to prevent brand impersonation.
“We have strict policies prohibiting ads that attempt to avoid our policing by disguising the advertiser’s individuality. They trying to impersonate other brands, and we strictly enforce them. We investigated the ads in question and removed them.” Google –
Google said it would investigate whether additional adverts and sites violate their laws. It will take the necessary steps if necessary.
Ad-blockers could increase protection.
The FBI issued an alert last year before Christmas warning about the use of sponsored ads in search engine results as a spyware delivery channel.
According to the agency, “these ads appear at the top of search results with minimal differentiation between an advert and an actual search result”. They link to a website that “looks identical to the impersonated business’s official webpage.”
As a result, cyber-criminals have a good chance of disseminating their ransomware to a larger number of unwitting users.
It’s a good idea to check the URL of an install source. When combined with the use of an ad-blocker, the level of security against this kind of threat should be dramatically reduced.
Ad-blockers are extensions available in most web browsers that, as the name implies, prevent advertisements from becoming packed and showcased on a web page, such as search results.
Aside from making the internet more comfortable to use. Ad-blockers improve privacy by preventing tracking cookies in adverts from gathering data regarding browsing habits.
However, in this case, such extensions could mean the difference between losing access to sensitive data or online accounts and obtaining online technologies from legitimate vendors.





