The Vulnerability
According to recent data from ThreatFabric, malicious actors are using voice phishing (vishing) techniques to trick victims into installing Android banking malware on their handsets.
The Dutch mobile security firm claimed to have discovered a network of phishing websites. These websites prey on Italians using online banking in order to gather their contact information.
The social engineering approach known as telephone-oriented attack delivery (TOAD) includes phoning the victim’s using information that has already been obtained from fraudulent websites.
In contrast, the caller who claims to be a bank support representative instructs the person to install a security programme. And provide it a lot of permissions when, in fact, it’s malicious software designed to acquire remote access or commit financial fraud.
The Issues
In this instance, it results in the installation of Copybara, an Android virus that was originally identified in November 2021. It is mostly used to carry out on-device fraud by targeting Italian consumers. Another virus family called BRATA has been mistaken for Copybara.
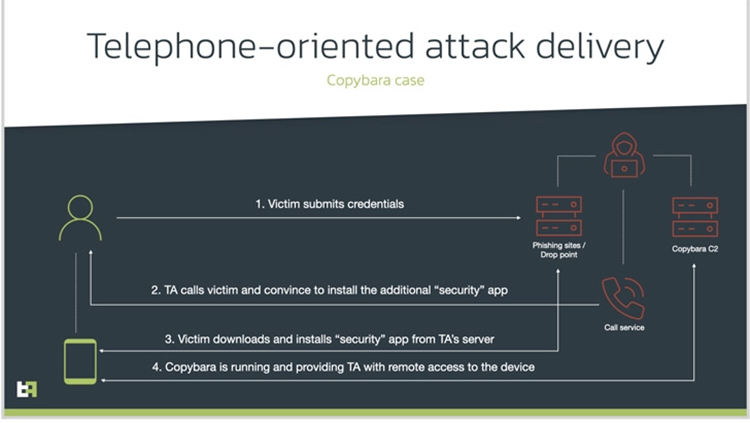
The TOAD-based efforts were determined by ThreatFabric to have started around the same time. It indicates that the activity has been going on for about a year.
Copybara’s RAT capabilities, like those of other Android-based malware, are supported by exploiting the accessibility services API of the operating system to capture private data. And even remove the downloader app to lessen its forensic trace.
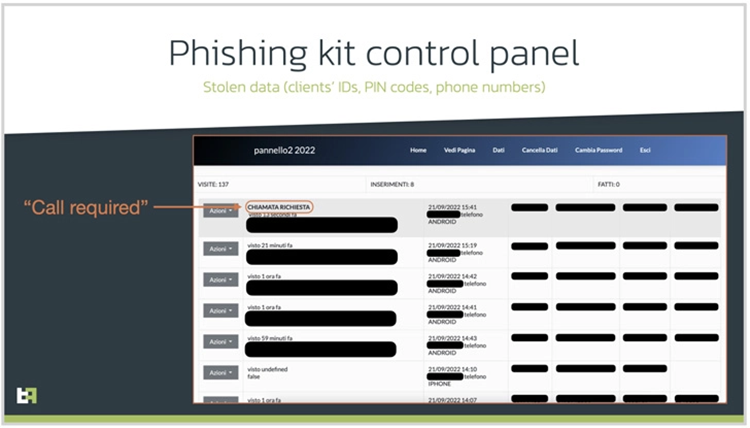
Additionally, the threat actor uses his infrastructure to distribute the second piece of malware called SMS Spy. The malware gives the adversary access to all incoming SMS messages and lets intercepts one-time passwords (OTPs) supplied by banks.
Scammers can now construct convincing Android malware campaigns without relying on time-tested techniques. These include Google Play Store droppers, fake advertisements, and smishing thanks to the recent surge of hybrid fraud assaults.
The Mobile Threat Intelligence (MTI) team at ThreatFabric said that such attacks are more sophisticated to carry out. And manage and necessitate more resources on the part of [threat actors].
The Conclusion
We would also like to emphasize that targeted attacks, at least in this particular campaign, are regrettably more successful from the perspective of fraud success.
This is not the first time usage of TOAD tactics for direct campaigns of banking malware. MalwareHunterTeam described a similar attempt last month that sought to install a data-stealer that looked like a credit card rewards programme on subscribers of the Indian bank Axis Bank.
The MTI team said, “Financial businesses should inform their consumers about active campaigns. And upgrade the client apps with features to detect suspicious behavior. Adding to it any unusual call should be verified by phoning your financial firm.”




