
Organizations across all industries have noticed a dramatic shift in the threat landscape in recent years. All types of intrusions have expanded in quantity and frequency, but ransomware has evolved especially quickly. Ransomware was a relatively remote concern for most businesses less than five years ago. A ransomware attack occurs right now numerous times each minute. Few business leaders now downplay the danger this infection poses to their company. But it seems that few are knowledgeable about ransomware prevention.
The main economic drivers behind the recent surge in ransomware include the simpler monetization of network access through cryptocurrencies. But the rise of ransomware as a criminal enterprise has also sparked a significant technological revolution.
The evolution of third-generation ransomware into a multi-level threat that combines access denial and extortion is one prominent feature of this change. Another is the ongoing capacity of knowledgeable malware developers to improve ransomware deployment and distribution techniques. Ransomware is consequently becoming more hazardous and frequently evading security measures entirely.
The transition away from ransomware deployment via files may be the most concerning recent development.
Now, a payload delivery attack chain frequently begins and ends in device memory during runtime—a highly exposed attack vector for the majority of businesses. It is necessary to reevaluate whether an organization’s defenses are effective in order to adapt to this significant change in assault deployment.
How to Prevent Ransomware: Block In-Memory Attacks
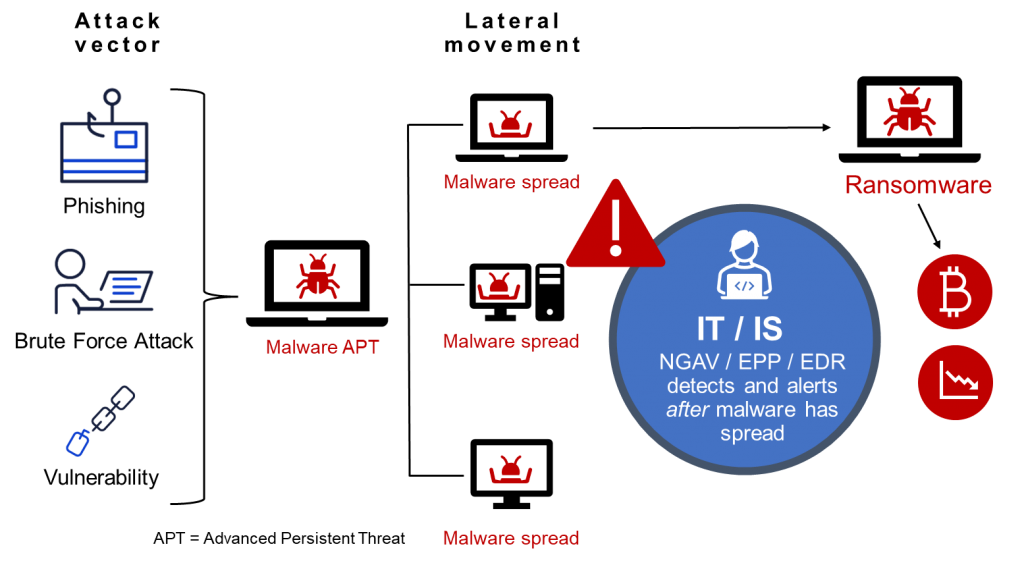
Security professionals often rely on threat intelligence feeds to correlate and analyse information, evaluate security defences, and prioritise activities to decrease risk when defending against ransomware.
Sadly, there is a significant disconnect between the surroundings that threat intelligence feeds watch and the locations where assaults take occur. Because of these feeds’ static indications of compromise (IOC), security teams frequently lag behind their attackers. This is due to the fact that scanning solutions frequently concentrate on static files and network activity. Which indicates that a crucial threat vector—device memory at runtime—is being largely ignored by enterprises.
For good reason, most cybersecurity solutions fail to close this hole: doing runtime memory and process scans causes everything to sluggishly. Continuously scanning a device’s memory is rarely practical for servers and other real-world hardware. Most security systems simply scan devices when activities begin and stop in order to lessen this problem. They rely on threats leaving behind observable signatures that they can identify. However, contemporary ransomware employs in-memory attack chains that cunningly exploit the flaw in this approach.
Exploring the In-Memory Attack Chain
An in-memory attack often starts with the download of a dropper onto the victim’s device. Any threat intelligence feeds relying on static IOCs are already obsolete at this point. For instance, highly obfuscated attacks won’t appear in a threat intelligence feed until the attack is recognised and categorised, whether the dropper is delivered through something like a malicious Excel macro or filelessly through remote code execution.
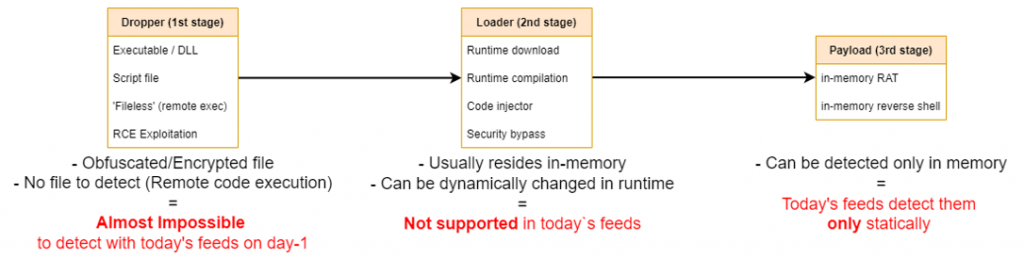
Ransomware attack chain
A threat enters the device runtime memory at the second stage of an assault, known as loader deployment, by a procedure such as runtime downloading or code injection. The attack is now totally undetectable.
The attack’s payload deployment, which could involve the use of a RAT or an in-memory reverse shell, likewise takes place in the device runtime memory. This indicates that the attack is once more undetectable and can only be recognised statically after it has caused damage. Threats can launch ransomware from this point, turn off controls, and move laterally across networks. It’s already too late to stop a ransomware attack by the time a defender notices it.
No level of NGAV or best-of-breed EDR can consistently detect and block these threats since they are extremely evasive and mostly reside in device memory. The cybersecurity community must update threat intelligence feeds to concentrate on memory detection in order to counteract these kinds of attacks.





