In recent months, Chaos, a new, multi-functional Go-based virus, has seen a sharp increase in volume to capture a variety of Windows, Linux, SOHO routers, and enterprise servers into its botnet.
According to experts at Lumen’s Black Lotus Labs, “Chaos capability includes the ability to enumerate the host environment. Also conducts remote shell commands, and loads additional modules. They automatically propagate through stealing and brute-forcing SSH private keys, as well as launch DDoS attacks.”
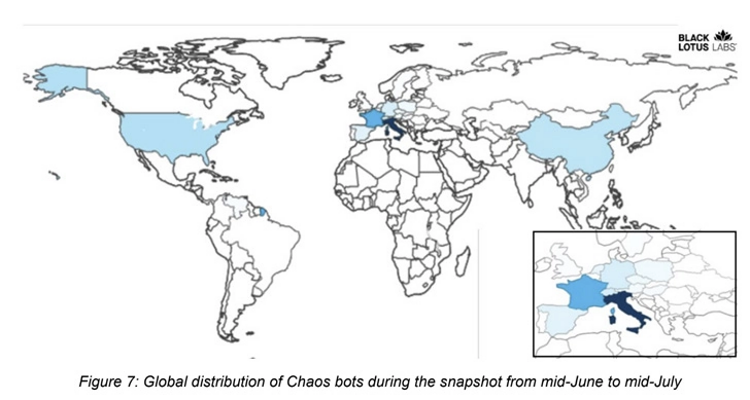
The majority of the bots collectively constitute “hundreds of unique IP addresses” over a one-month period from mid-June through mid-July 2022. These are concentrated in Europe, particularly Italy, with additional infections recorded in China and the U.S.
The botnet joins a lengthy list of malware that establishes persistence for long periods of time. Likely to misuse the foothold for evil objectives, such as DDoS assaults and cryptocurrency mining. It is written in Chinese and uses China-based infrastructure for command and control.
If anything, the trend also suggests a sharp increase in threat actors using programming languages. These languages include like Go to avoid detection, make reverse engineering challenging, and target several platforms simultaneously.
Chaos (not to be confused with the creator of the same name ransomware) lives up to its name by initially gaining access by abusing known security flaws. Then leveraging it to conduct reconnaissance and launch lateral movement around the infiltrated network.
Further Malware
Additionally, the malware is more versatile than comparable malware since it can run on a variety of instruction set architectures, including ARM, Intel (i386), MIPS, and PowerPC. This feature effectively enables the threat actor to widen the spectrum of its targets and quickly increase in volume.
Additionally, Chaos has the capacity to carry out up to 70 different commands provided by the C2 server. C2 server instructs the exploitation of vulnerabilities that have been publicly reported (CVE-2017-17215 and CVE-2022-30525).
Another Go-based DDoS malware called Kaiji, which previously targeted improperly configured Docker instances, is thought to have evolved into Chaos. According to Black Lotus Labs, the correlations result from overlapping codes and functions based on an examination of more than 100 samples.
A European GitLab server was one of the Chaos botnet’s victims in the first few weeks of September. It also discovered a number of DDoS attacks on companies in the gaming, financial services, technology, media and entertainment, and hosting sectors. A cryptocurrency mining exchange was also targeted.
The information was discovered precisely three months after the cybersecurity firm revealed a fresh remote access trojan known as ZuoRAT. ZuoRAT specifically targets SOHO routers as part of a sophisticated operation against European and North American networks.
According to Mark Dehus, head of threat intelligence for Lumen Black Lotus Labs, “we are seeing a complex malware that has quadrupled in size in only two months. And it is well-positioned to continue advancing.” “A variety of consumer and business gadgets and hosts are threatened by chaos.”