LilithBot malware, has been connected to the threat actor responsible for the malware-as-a-service (MaaS) named Eternity.
Researchers Shatak Jain and Aditya Sharma from Zscaler ThreatLabz stated in a paper released on Wednesday that malware has a sophisticated ability to be employed as a miner, stealer, and clipper in addition to its persistence mechanisms.
The virus has been improved continually by the gang, who have included features like anti-debug and anti-VM checks.
Earlier this year, Eternity Project entered the market by promoting its software and product updates on a Telegram channel. A USB worm, miner, clipper, ransomware, and DDoS bot are among the services offered.
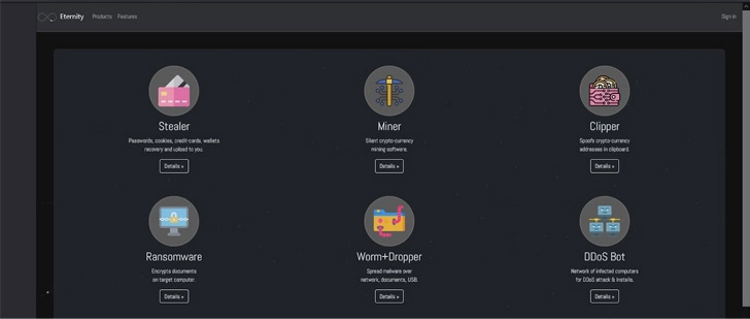
The most recent addition to this list is LilithBot malware. The multipurpose malware bot is offered on a subscription basis to other hackers in exchange for a cryptocurrency payment, just like its rivals.
After successful penetration, the information the bot collected (browser history, cookies, images, and screenshots) is exfiltrated to a remote server in a ZIP package named “report.zip”.
The change indicates that the Eternity Project is actively adding to its collection of malware and using cutting-edge strategies to avoid detection.





