Worst-case possibilities included malicious construction and greater infrastructural compromise. Multiple workflows of the well-known continuous integration and development (CI/CD) service GitHub Actions have been found to be command execution susceptible by security researchers. An automation tool created by the Tinder…
Latest posts - Page 48
Malicious Npm Packages Target Discord Users Once More
A recent LofyLife campaign infects client files and obtains tokens to track user activity including logins, password changes, and payment methods. Researchers have discovered that threat actors are once more concealing malware that can steal Discord tokens in order to…
The US Government Alerts Citizens To The Rise in SMS Phishing Attempts
Americans have been alerted by the Federal Communications Commission (FCC) to an upsurge in SMS (Short Message Service) phishing attacks that aim to steal their money and personal information. Scammers behind such attacks, often known as smishing or robotexts (as…
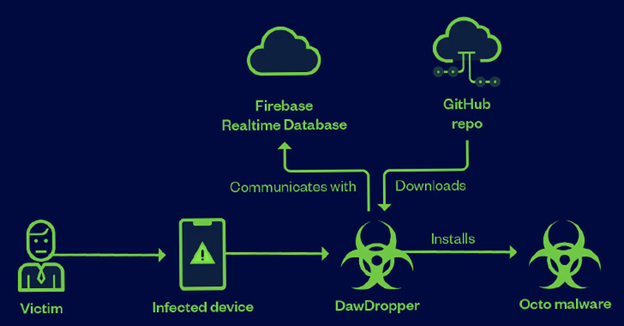
Numerous Android Apps On The Google Play Store Have Been Discovered To Drop Banking Malware
A malicious effort used Android dropper apps that appeared to be innocuous from the Google Play Store to infect consumers’ smartphones with banking malware. These 17 dropper apps, collectively referred to as DawDropper by Trend Micro, pretended to be productivity…
Framing without iframes
Recently, Portswigger researchers discovered new techniques for framing a website without using the iframe element when researching XSS vectors. To include these, PortSwigger has updated the XSS cheat sheet. Researchers at Portswigger found that Google Chrome permits changing the URL…
Untangling KNOTWEED: A private European Offensive Actor Employing 0-Day Exploits
A private-sector offensive actor (PSOA) was discovered by the Microsoft Threat Intelligence Center (MSTIC) and the Microsoft Security Response Center (MSRC) using a number of Windows and Adobe 0-day exploits, including one for the recently patched CVE-2022-22047, in limited and…
The CISA Director Warns That Ransomware Hackers Will Continue To Target Smaller Critical Infrastructure
Brandon Wales, the executive director of CISA, spoke on how ransomware perpetrators target businesses of all sizes and how CISA wants firms to stop zero-day incidents. Federal agencies have increased their efforts to thwart future assaults on the country’s vital…
4 Steps the Financial Industry Can Take to Cope with Their Growing Attack Surface
The financial services sector has long been at the forefront of technology adoption, but the 2020 pandemic has hastened the adoption of chat-based customer service, mobile banking apps, and other technological advancements. According to Adobe’s 2022 FIS Trends Report, the…
Experts Discover Similarities Between BlackMatter Ransomware and New LockBit 3.0
The most recent version of the LockBit ransomware shares characteristics with BlackMatter, a renamed form of the DarkSide ransomware strain that went out of business in November 2021, according to cybersecurity analysts. In addition to the first ransomware bug bounty…
Grails Have A Serious Security Flaw That Could Allow Remote Code Execution
The open-source web app framework’s maintainers advise patching all versions, even those that are not thought to be susceptible. A significant security flaw has been identified by AntGroup FG Security Lab researchers that enables remote code execution within Grail’s application…