In harmful campaigns, a Traffic Direction System (TDS) is used to lead individuals who fit a specific profile to phishing sites.
The FakeUpdate campaign
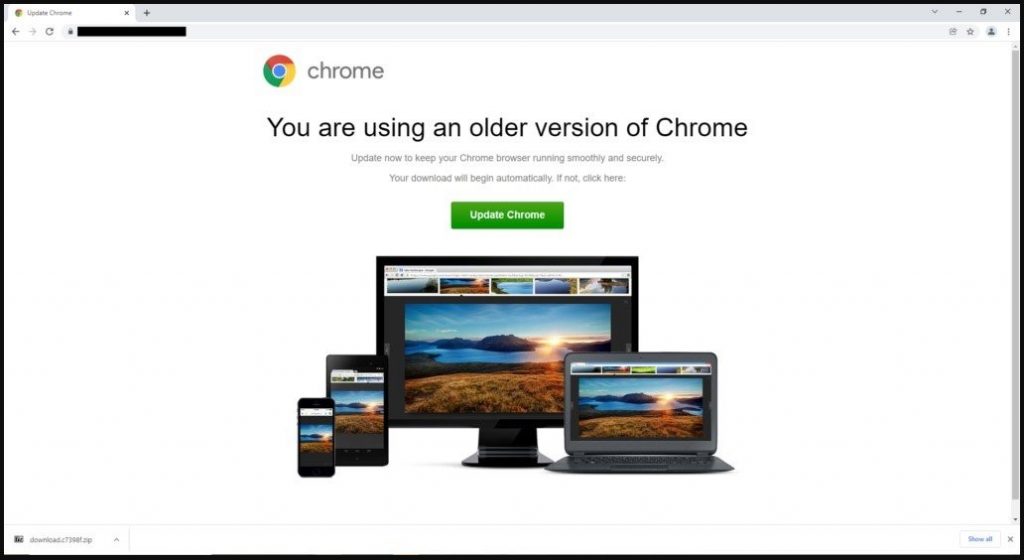
Avast researchers found Parrot TDS and revealed that it’s presently being utilised in the FakeUpdate (aka SocGholish) campaign, which spreads RATs via false browser update alerts. The campaign began in February, although the first signs of Parrot activity were discovered in October of last year.
From thousands of redirected individuals, the campaign’s user profile and filters are fine-tuned to target a specific sort of victim. On the basis of hardware, software, and network profiling, the attackers transmit distinct payload-dropping URLs to the victim. NetSupport Client RAT is the payload dumped, and it grants direct access to the compromised machines.
The Parrot TDS service
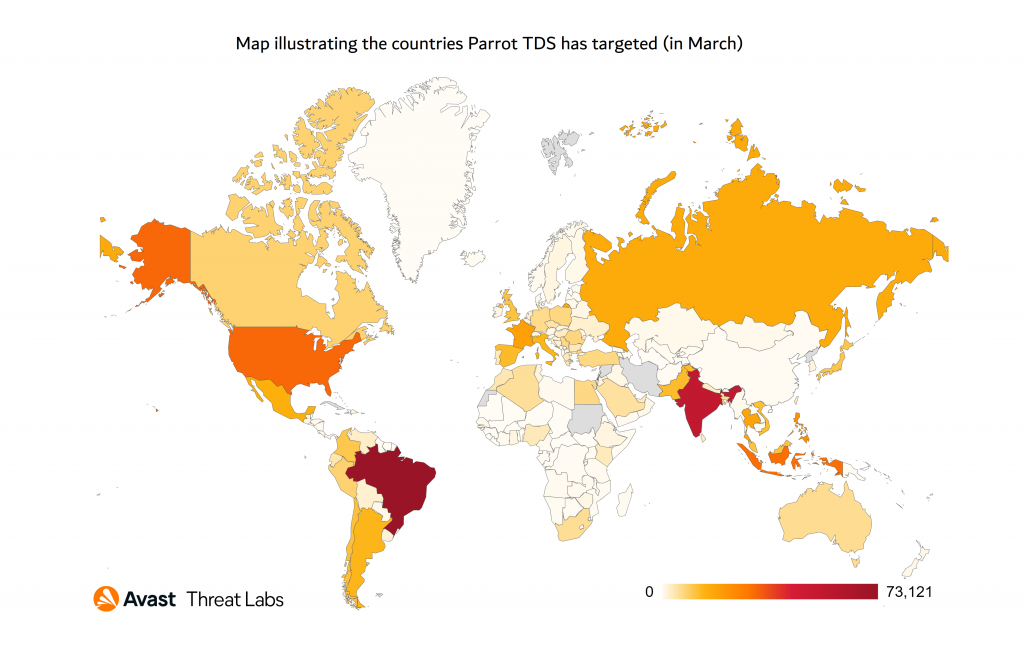
Parrot TDS relies on 16,500 websites for colleges, adult content platforms, municipal governments, and personal blogs on servers. On compromised servers, the attackers planted a malicious web shell and duplicated it to multiple locations under different names in a parroting pattern. In some cases, the attackers send requests straight to the Parrot infrastructure without using the PHP script.
Additionally, the attackers deployed a PHP backdoor software to harvest client data and send queries to the Parrot TDS C2 server. Researchers have also discovered a number of infected servers running phishing sites that seem like a legitimate Microsoft login page and encourage visitors to enter their account credentials.
What to do?
For enhanced protection, experts advocate adopting up-to-date internet security solutions while browsing the web. Furthermore, IT administrators should use an antivirus to scan all files on the webserver, replace JavaScript and PHP scripts on the webserver with originals, and utilise the most recent CMS and plugin versions.
Source: https://cyware.com/news/parrot-tds-a-new-web-redirect-service-63594607





