Following Conti’s official retirement from the threat scene this year, ransomware-as-a-service (RaaS) organizations like Quantum and BlackCat Ransomware are now using the Emotet malware.
Emotet began as a banking trojan in 2014, with time, upgraded and transformed the virus into a highly dangerous threat. It can download additional payloads onto the victim’s computer, allowing the attacker to take remote control of it.
The Conti ransomware cartel is alleged to have played a key role in the invasive malware loader’s resurgence late last year. Despite the infrastructure connected to it having been shut down as part of an enforcement attempt in January 2021.
Emotet was a unique ransomware tool used only by Conti from November 2021 to the company’s liquidation in June 2022, according to an alert released last week by AdvIntel. However, the Emotet infection chain is presently attributed to Quantum and BlackCat ransomware.
In typical assault sequences, Cobalt Strike is dropped via Emotet (also known as SpmTools), which is subsequently utilized as a post-exploitation tool for ransomware operations.
The Ransome Gangs
Even though the infamous Conti ransomware gang has disbanded, some of its members are still engaged in criminal activity. They are either independent organizations or members of other ransomware crews like BlackCat and Hive.
In recent months, Quantum, a Conti spin-off organization, has turned to the call-back phishing tactic known as BazaCall. The BazaCall is also known as BazarCall in order to infiltrate targeted networks.
In a recent report, Recorded Future said that Conti affiliates deploy a range of initial access methods. They include phishing, compromising credentials, malware distribution, and exploiting vulnerabilities.
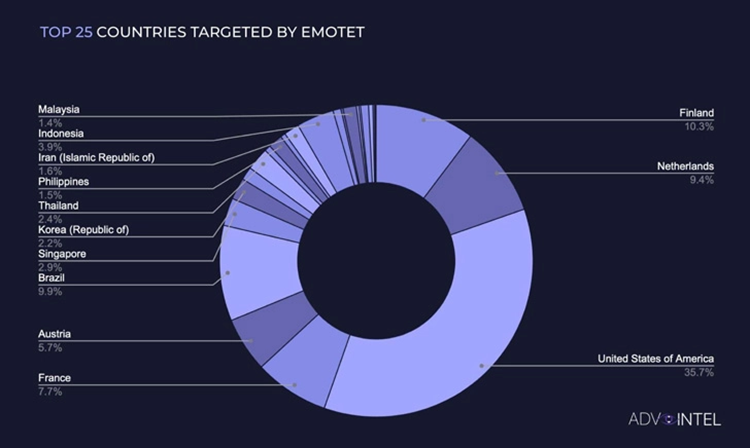
Since the beginning of the year, approximately 1,267,000 Emotet infections have been reported worldwide. According to AdvIntel, activity peaks in February and March that coincides with Russia’s invasion of Ukraine.
Due to Quantum and BlackCat ransomware organizations’ use between June and July, there was a second spike in infections. Emotet attacked the United States the most, followed by Finland, Brazil, the Netherlands, and France, according to a cybersecurity company.
The first four months of 2022 saw a 100-fold increase in Emotet detections compared to September to December 2021.
Emotet plummeted from first to fifth on the list of the most common malware for August 2022, according to the Israeli cybersecurity firm Check Point, trailing FormBook, Agent Tesla, XMRig, and GuLoader.




