A number of ransomware organizations utilize a fresh strategy sporadic encryption technique to speed up the encryption process. Also to decrease the chances of finding and stopping.
sporadic encryption technique, known as intermittent encryption, encrypts only a portion of the content of the targeted files. These render the data unrecoverable without the use of a working decryptor and key.
For instance, by skipping every other 16 bytes in a file, the encryption procedure nevertheless locks the contents permanently while taking up less time than it would for full encryption.
Furthermore, because the encryption is less strict, automated detection systems that depend on looking for warning indicators in the form of vigorous file IO activities are more likely to fail.
What did the cool kids use?
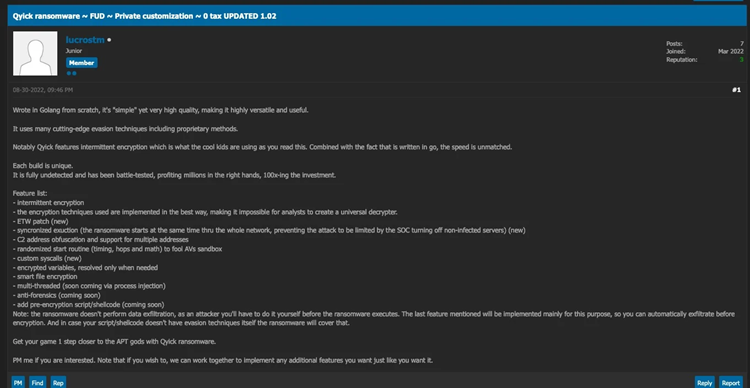
An analysis of a trend that was initiated by LockFile in the middle of 2021 and is now being used by companies including Black Basta, ALPHV (BlackCat), PLAY, Agenda, and Qyick has been published by SentinelLabs.
To persuade affiliates to join the RaaS business, these gangs extensively highlight the existence of sporadic encryption characteristics in their family of ransomware.
According to a Qyick advertisement on hacking forums, “Qyick has intermittent encryption, which is what the hip kids are utilizing as you read this. Coupled with the fact that is written in Go, the speed is unrivalled.”
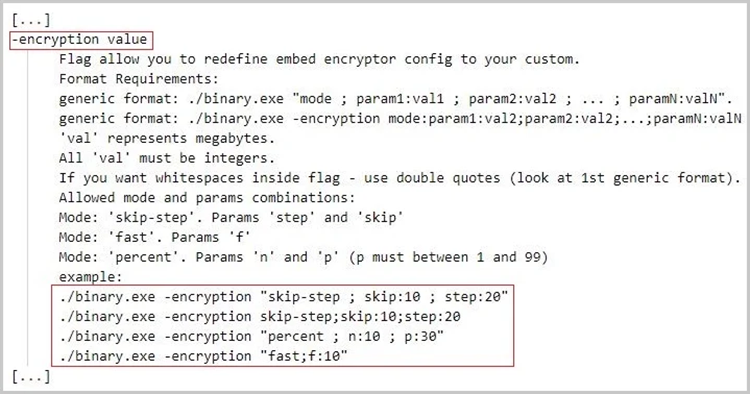
Intermittent encryption is an optional and customizable feature of Agenda ransomware. These are the three potential partial encryption modes:
- skip-step [skip: N, step: Y] – Encrypt every Y MB of the file, skipping N MB.
- fast [f: N] – Encrypt the first N MB of the file.
- percent [n: N; p:P] – Encrypt every N MB of the file, skipping P MB, where P equals P% of the total file size.
Operator configuration options are also provided by BlackCat’s intermittent encryption implementation in the form of several byte-skipping patterns.
Auto mode Malware
The malware, for instance, has an “auto” mode that combines other modes for a more complicated outcome. It can also encrypt only the first few bytes of a file, follow a dot pattern, a certain percentage of file blocks, etc.
The speed of intermittent encryption also supported the recent appearance of the PLAY ransomware via a well-publicized attack against Argentina’s Judiciary of Córdoba.
PLAY simply divides the file into 2, 3, or 5 chunks, and then encrypts each subsequent chunk, without configuration choices.
Last but not least, Black Basta, is one of the most well-known brands in the industry right now. The Black Basta forbids users from selecting a mode because its strain determines what to do through file size.
It encrypts full content for little files with a size of fewer than 704 bytes. For files between 704 bytes and 4 KB, it encrypts 64 bytes and skips 192 bytes in between. For files larger than 4 KB, BlackBasta’s ransomware shrinks unencrypted sections to 128 bytes and leaves unencrypted at 64 bytes.
Intermittent encryption outlook
Security specialists believe more ransomware gangs will soon embrace intermittent encryption since it appears to offer many benefits without drawbacks.
Given that LockBit’s strain already has the fastest encryption speeds available. The gang’s attacks would last only a few minutes if they used the partial encryption method.
Naturally, intermittent encryption must be implemented properly in order to prevent easy data recovery by the victims. This is because encryption is a complicated topic.
The most advanced implementation at the moment is BlackCat’s, while Qyick’s is still unknown because malware specialists haven’t yet examined samples of the new RaaS.





