Researchers from ESET have discovered a malware operation that preys on Chinese speakers in Southeast and East Asia, paying for deceptive ads appearing in Google search results and directing users to download trojanized installers. The unidentified attackers made phoney websites that resemble the accurate versions of well-known programmes like Firefox, WhatsApp, or Telegram. These websites also distribute FatalRAT, a remote access trojan that gives the attacker access to the affected machine.
Users in Taiwan, China, and Hong Kong are the nations where attacks between August 2022 and January 2023 were discovered.
Attack overview
The figure depicts a streamlined overview of the attack. The FatalRAT malware, first revealed by AT&T researchers (@attcyber) in August 2021, is installed by various components.
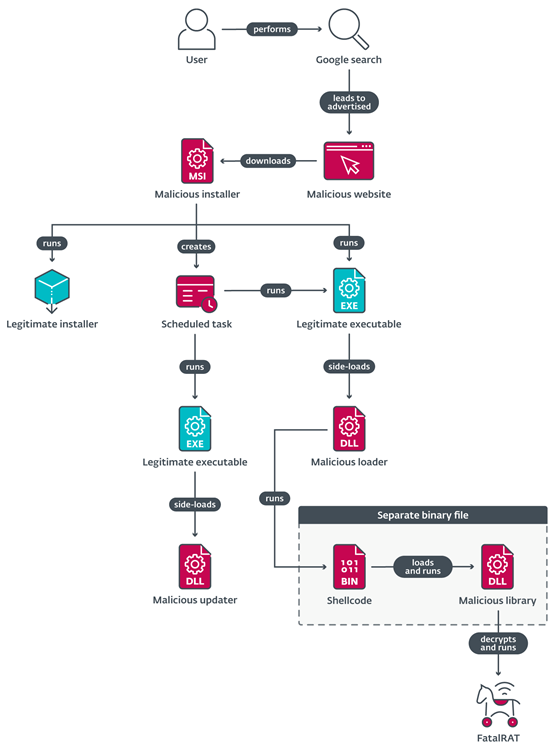
The attackers created several domain names pointing to the same server, home to numerous websites that distributed trojanized software. Some websites have the same visual appearance as their legitimate equivalents but send malicious installers instead. As indicated in Figure 2, the other websites, which the attackers may have translated, provide Mandarin language versions of software unavailable in China, such as Telegram.
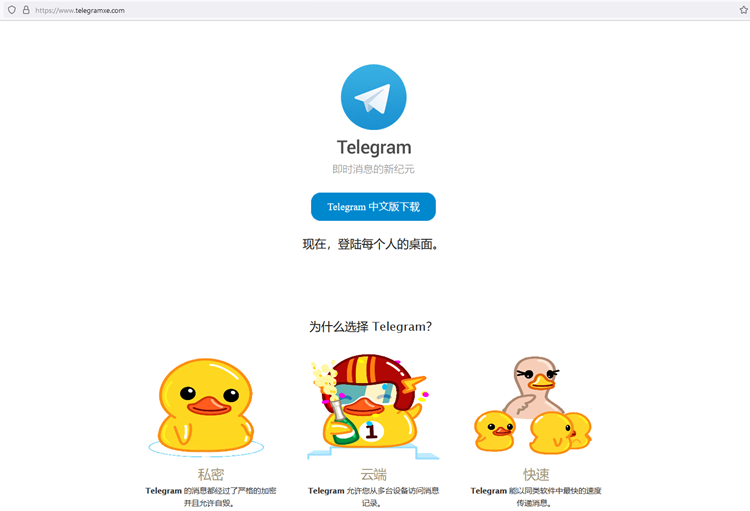
Chrome, Firefox, Telegram, WhatsApp, Line, Signal, Skype, Electrum Bitcoin wallet, Sogou Pinyin Method, a Chinese Pinyin input method editor, Youdao, a dictionary and translation tool, and WPS Office, a free office suite are among the malicious websites and installers for these programmes.
Also, read Tibetans are the target of Chinese espionage hackers using the new LOWZERO backdoor.
Although there are theoretically numerous methods to lead potential victims to these malicious websites, one news site said that when looking for the Firefox browser in Google, they were presented with an advertisement that led to one of these websites. Although we could not duplicate these search results, we think that only users in the specified area received the advertising. Figure 3 displays a case. Also, Google was informed about the websites and the ads.
Installers
The installers downloaded from the bogus websites are stored in the Alibaba Cloud Object Storage Service rather than on the same server as the web pages. Advanced Installer-made MSI files have been digitally signed (see the Certifications section). The malicious installers that the attackers uploaded to the cloud storage on January 6, 2023, are seen in Figure 3.
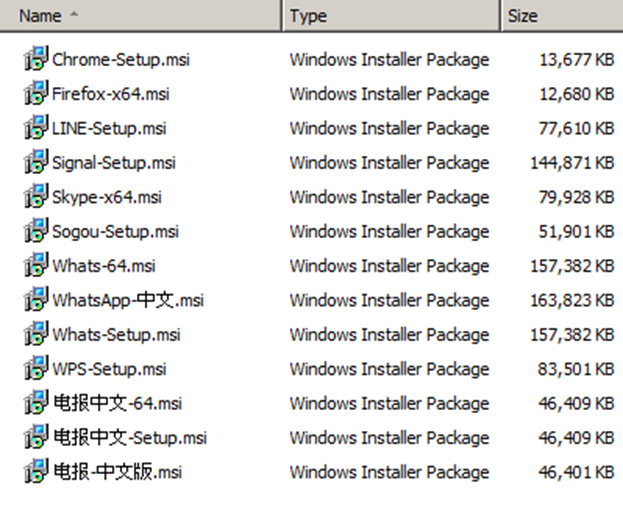
When these installers are executed, they usually:
- Drop and launch the FatalRAT malware’s malicious loader and associated files in the %PROGRAMDATA%Progtmy directory.
- Delete the malware updater and any associated files, then drop them in the %PROGRAMDATA%Progtmy0 directory.
- Insert the ossutilconfig file into the %USERPROFILE% directory. The updater will use these credentials to connect to a distant bucket in the Alibaba Cloud.
- Create an empty directory called %PROGRAMDATA%Progptp (although, in some cases, the FatalRAT malware was installed in this directory instead).
- Put the genuine installer into C: Program FilesCommon Files and run it there (see CommonFiles64Folder).
- To perform the loader and updater components, create scheduled tasks.
Loaders
The loader, libpng13.dll, is a fundamental component that opens and runs the image Micr.jpg, which can be found in the same directory as the DLL in memory. The attackers have obscured the loader through numerous calls to a method that outputs some hardcoded data. This practice might have been employed to prevent detection by security programmes or make DLL analysis more challenging.
Indeed, Micr.jpg is a shellcode with an integrated DLL. By invoking the DLL’s SignalChromeElf export function, this shellcode aims to load and run the embedded DLL in memory. Before this export function is executed, the shellcode rebuilds the DLL’s imports table and calls the DllEntryPoint, which merely calls the Windows API function DisableThreadLibraryCalls to make the DLL more stealthy.
In essence, the embedded DLL’s SignalChromeElf will decode, load, and execute an encrypted payload. Following its decryption, the DLL will locate the location of an export function named SVP7, which includes the malware’s entry point, and call it while passing the encrypted configuration of the FatalRAT malware as an argument. This encrypted payload is the FatalRAT malware.
Conclusion
Most of the time, phoney websites are exact replicas of the real ones. The trojanized installers, on the other hand, installed the genuine application that the user was interested in, averting concerns that the victim’s computer may have been compromised. We can see how crucial it is to carefully examine the URL we visit before downloading software because of all these factors. After confirming that it is the vendor site, enter it into your browser’s address bar.
Anyone could be impacted because the malware employed in this campaign, FatalRAT, provides several instructions intended to alter data from different browsers. The victimology is not targeted at any particular user type. The attackers are likely interested in stealing data, such as web credentials, and reselling them on darknet markets or utilizing them for another kind of crimeware campaign. Still, for the time being, it is impossible to attribute this campaign specifically to a known or new threat actor.




