Multiple UWB RTLS (real-time locating systems) vulnerabilities have been found by security researchers, giving threat actors the ability to conduct man-in-the-middle attacks and modify tag geo-location data.
RTLS technology is widely employed in industrial settings, public transportation, healthcare, and applications for smart cities. Using tracking tags, signal reception anchors, and a central processing system, it serves as a safety aid by constructing geofencing zones.
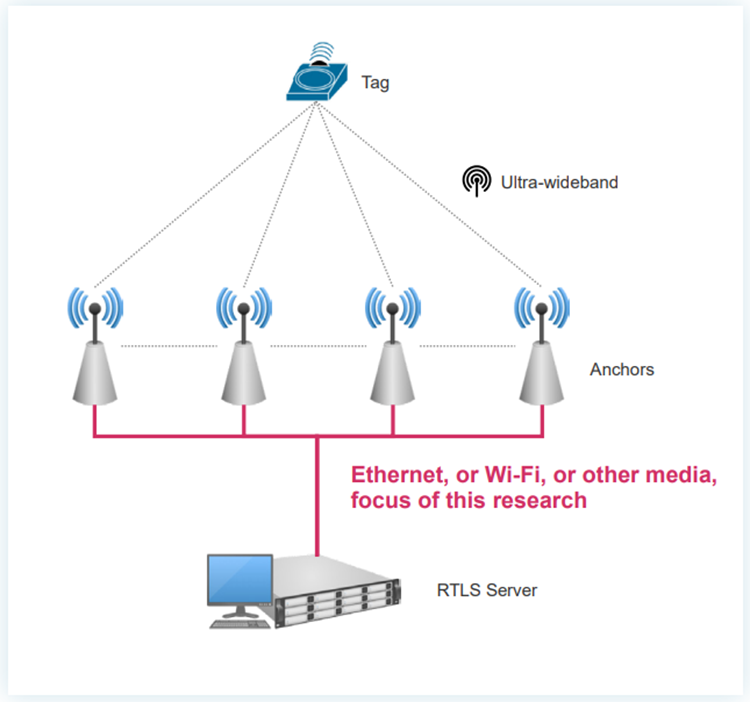
Dangerous repercussions for people’s health and safety can result from tampering with the boundaries of hazard zones or their positioning in these surroundings.
The previously unknown security weaknesses were discovered by Nozomi Networks researchers during Black Hat 2022, and the complete technical information was released in a white paper yesterday.
Non-encrypted communications
The Sewio Indoor Tracking RTLS UWB Wi-Fi kit and the Avalue Renity Artemis Enterprise kit, two popular RTLS products that enable the aforementioned safety capabilities, were the attention of Nozomi analysts.
UWB signals are used by the tracking tags to interact with the anchor, whereas Ethernet or Wi-Fi is used by the anchors to send and receive data from the main computer.
Both devices communicate via a unique binary network protocol if Wi-Fi is used. Reverse engineering is nevertheless made possible by Wireshark captures of the network packets because the data is not encrypted.
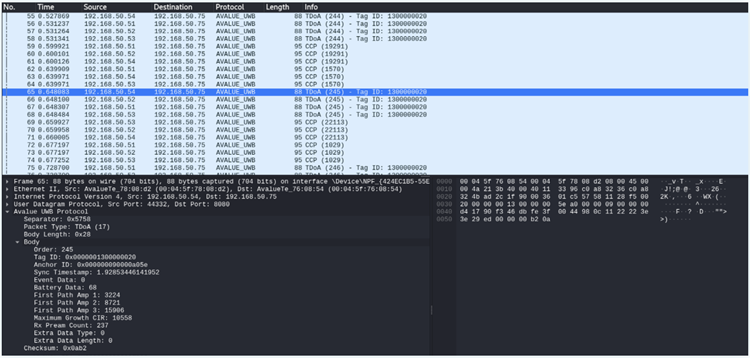
It is necessary to gain access to the WPA2-PSK-protected Wi-Fi network in order to collect those packets. Even yet, many deployments are vulnerable since both manufacturers utilize a weak default password that might not be changed after installation.
A remote attacker would be able to send any value to the central computer by faking sync and positioning packets if they were successful in computing the location of the anchors to determine the relative position of the tracking tags.
According to Nozomi, the transmitted power levels and timestamps, which represent tag distances from the anchor sites, can be used to infer essential information about anchor positioning. Access to the target region physically, though, would make this process simpler.
An attacker may use eavesdropping in addition to data manipulation to follow assets and people’s locations, either for stalking and reconnaissance or to find a valuable object.
During attacks, movement patterns can be recorded and played back to simulate genuine tag movement, such as that of a guard on patrol, for instance.
Tampering with geofencing
If an attacker gains access to the RTLS system, they can move tags around to create false alarms, impede production, or grant entry to a prohibited region.
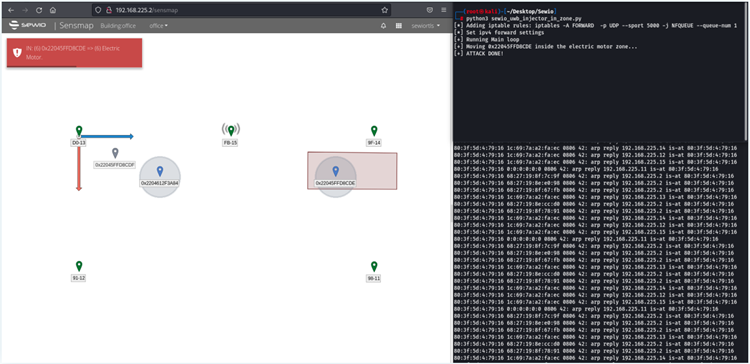
Making workers appear outside of machine safety zones, where the machines would continue to run as if no one was there, might also put them in danger of bodily harm.
Threat actors could modify a valuable object’s position to make it appear stable inside a protected zone while physically removing it from the monitored region without setting off any alerts if they want to steal it.
Nozomi advises RTLS system administrators to utilize firewalls to control access, install intrusion detection systems on the network, and encrypt data using SSH tunneling and packet synchronization counter-values.





