Developers may be exposed to supply chain risks as a result of novel timing attacks uncovered against the registry API of the npm package manager.
Threat actors can identify businesses’ scoped private packages by compiling a list of potential package names. That they can then use to mask public packages and fool users and workers to download them. According to Yakir Kadkoda, an Aqua Security researcher.
The Scoped Confusion attack relies on comparing the response time for a non-existent module to the time it takes the npm API (registry.npmjs[.]org). It produces an HTTP 404 error message when requesting a private package.
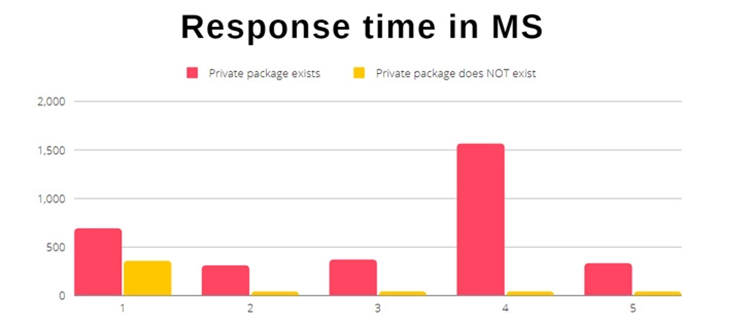
According to Kadkoda, a private package that doesn’t exist generally responds in less time to respond than a private package.
The ultimate goal is to discover corporate internal software packages that threat actors could utilize to produce public copies of the same packages in an effort to contaminate the software supply chain.
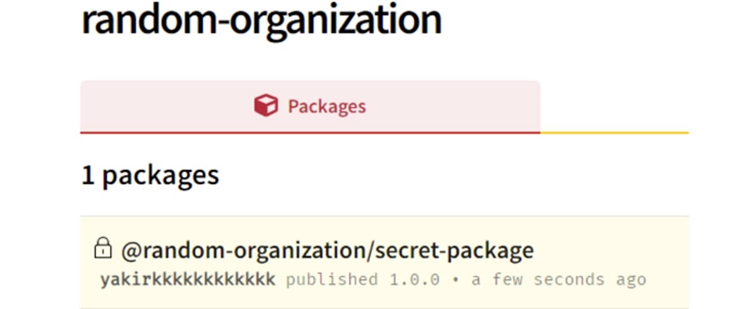
The most recent discoveries differ from dependency confusion attacks in that they call for the adversary to first estimate the private packages that an organization uses before publishing counterfeit packages with identical names within the public scope.
Contrarily, dependency confusion (also known as namespace confusion) depends on the fact that package managers search public code repositories before private ones. As a result, a malicious higher version package is retrieved from the public repository.
Also read German companies are being targeted with malicious NPM packages
Conclusion
The timing attack will not be addressed owing to architectural constraints, according to a statement from Microsoft-owned company GitHub. GitHub has informed about the bug by Aqua Security on March 8, 2022.
Organizations are advised to routinely check npm and other package management platforms for lookalike or faked packages. These pose as their internal counterparts as a precautionary step.
If you can’t locate any public packages that are comparable to your internal packages. Kadkoda advised, “try generating public packages as stand-ins to thwart such attacks.