Phishing actors are successfully rerouting targeted users to phishing pages that collect payment information by leveraging LinkedIn’s Smart Link function to get beyond email security measures.
Users of LinkedIn Sales Navigator and Enterprise are entitled to the Smart Link function, which enables them to deliver a group of up to 15 documents via a single trackable link.
In addition to being flexible, Smart Link offers data to marketing professionals, including reports on who watched the shared content and how long they viewed it.
Therefore, phishing scammers aren’t simply using Smart Link to get beyond email security measures; they can also learn how effective their campaigns are and use that information to improve their lures.
Threat experts at Cofense have noticed campaigns luring Slovakian users with phoney postal service lures, which has led them to notice the new trend of Smart Link abuse for email phishing scams.
(In)Secure redirection
The phishing email advising the receiver of the need to pay fees for a parcel that is on the way out purports to be from Slovenská pota, the state-owned postal service operator in Slovakia.
The sender’s address is made to look real to the receiver via email header deception, but upon closer inspection, it is discovered that the sender is actually “[email protected],” a company that has no connection to the postal service.
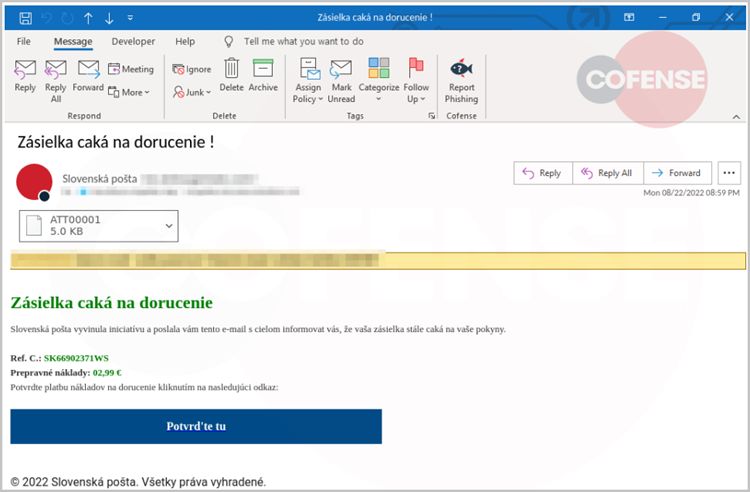
A LinkedIn Smart Link URL is inserted in the confirm button. Additionally alphanumeric variables are appended at the end of the URL to route the user to a phishing page. (“linkedin[.]com/slink?code=g4zmg2B6”).
Threat actors take advantage of the redirection capability in Smart Links. Smart Links usually promote marketing pages, adverts, etc., to circumvent security checks.
The landing page’s shipping cost is realistically set at €2.99; nevertheless, the phishing actors’. Their real objective is to obtain the target’s credit card information, including the number, holder’s name, expiration date, and CVV.
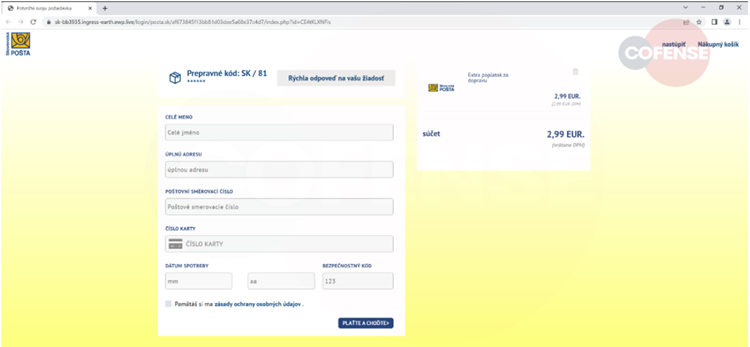
The primary function of the final SMS code confirmation page is to sprinkle authenticity throughout the procedure. Visitors who enter the information and click “Submit”. The fake notifies the users of a successful payment and is eventually redirected.
While this current campaign still focuses on Slovakians. They might not be long until phishing actors with wider reach abuse LinkedIn Smart Link.
Mitigation
LinkedIn said that their internal teams work to take action against those who attempt to harm LinkedIn members through email phishing scams. We encourage members to report suspicious messages. We will help them learn more about what they can do to protect themselves, including turning on two-step verification. To learn more about how members can identify phishing messages, see our Help Center.





