Chile’s national computer security and incident response team (CSIRT) has announced that a ransomware attack has impacted the country’s government agency’s operations and online services.
The ransomware attack began on Thursday, August 25, and targeted the agency’s Microsoft and VMware ESXi servers.
The hackers shut down all running virtual machines and encrypted their files, appending the “. crypt” filename extension to the filenames.
“Among other things, the ransomware would use the NTRUEncrypt public key encryption algorithm to target log files (.log), executable files (.exe), dynamic library files (.dll), swap files (.vswp), virtual discs (.vmdk), snapshot (.vmsn) files, and virtual machine memory (.vmem) files.” CSIRT Chile
The malware used in this attack also had functions for stealing credentials from web browsers, listing removable devices for encryption, and evading antivirus detection via execution timeouts.
In a typical double-extortion fashion, the intruders offered the Chilean CSIRT a communication channel. Through this, they could negotiate the payment of a ransom that prevents files from leaking and unlocking the encrypted data.
The attacker set a three-day deadline and threatened to sell the stolen data on the dark web to other cybercriminals.
Attribution unclear
Chile’s CSIRT announcement does not name the ransomware group responsible for the attack. Also, does it provide information to identify the malware.
Because it has been used by multiple threat actors, the extension appended to the encrypted files provides no clue.
While the little information provided by Chile’s CSIRT on the malware’s behavior points to ‘RedAlert’ ransomware (aka “N13V”). The RedAlert is an operation launched in July 2022, technical details indicate otherwise.
RedAlert ransomware attacks used the “.crypt” extension, targeted both Windows servers and Linux VMWare ESXi machines. It has the ability to force-stop all running VMs prior to encryption, and employs the NTRUEncrypt public-key encryption algorithm.
The indicators of compromise (IoCs) in Chile’s CSIRT announcement, on the other hand, are either associated with Conti or produce an inconclusive result when fed into automated analysis systems.
Conti has previously been linked to attacks on entire nations, such as the July 2022 attack on Costa Rica, which took five days from initial access to stealing and encrypting the systems.
According to threat analyst Germán Fernández, the strain appears to be entirely new, and the researchers he spoke with were unable to associate the malware with known families.
Fernandez also stated that the ransom note was not generated during the infection, which we can confirm. According to the researcher, the note was delivered prior to the deployment of the file-locking malware.
“One interesting fact is that the threat actors distributed the ransom note prior to deploying the ransomware as the final payload. To avoid evasion issues or to avoid having their contact information leaked when sharing the final sample.” Fernández, Germán.
BleepingComputer was able to analyze multiple samples of the malware used in the attack and recovered a ransom note known as readme for unlock.txt,’ which is shown below:
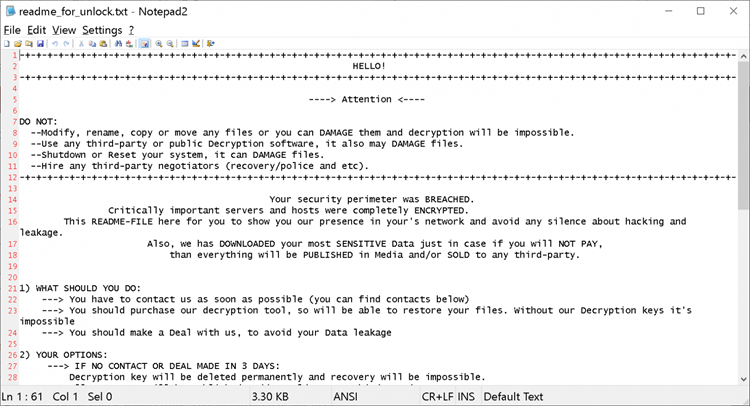
When analyzing this ransomware strain, they discovered a link to a unique website in the Tor network, and a password to log in.
As far as we know, there is no data leak site for this ransomware. The Tor site displays a message box through which victims can contact hackers.
How to Mitigate
Chile’s cybersecurity organization advises all state entities and large private organizations in the country to implement the following safeguards:
- Make use of a properly configured firewall and antivirus software.
- VMware and Microsoft assets should be updated.
- Maintain backups of your most important data.
- Check anti-spam filter configuration and train employees to recognize malicious email.
- Use network segmentation and the principle of least privilege.
- Keep up to date on new vulnerabilities that require immediate patching or mitigation.
Chile’s CSIRT has provided a set of compromise indicators for files used in the attack that defenders can use to protect their organizations.




