Threat actors can easily launch attacks thanks to the “Caffeine” phishing-as-a-service (PhaaS) platform (Microsoft 365 Phishing Attacks), which has an open registration process that enables anybody to join and launch their own phishing campaigns.
Caffeine does not require invites, recommendations, or permission from a Telegram or hacking forum admin from would-be threat actors. As a result, it greatly reduces the friction that distinguishes practically all platforms of this type.
Another distinguishing feature of Caffeine is that, in contrast to most PhaaS platforms, it focuses on lures for Western services in its phishing templates, which target Russian and Chinese platforms.
Caffeine is a worryingly feature-rich PhaaS, according to Mandiant experts, who uncovered it and thoroughly examined it given its low entrance barrier.
After looking into a massive phishing operation that used the service to target one of Mandiant’s clients and obtain Microsoft 365 account credentials, the cybersecurity company discovered Caffeine for the first time.
Fueling phishing campaigns
Caffeine needs account creation before the operator can access the “Store,” which includes tools for creating phishing campaigns and an overview dashboard.
The operators must then buy a subscription licence, which, depending on the features, can cost $250 per month, $450 for three months, or $850 for six months.
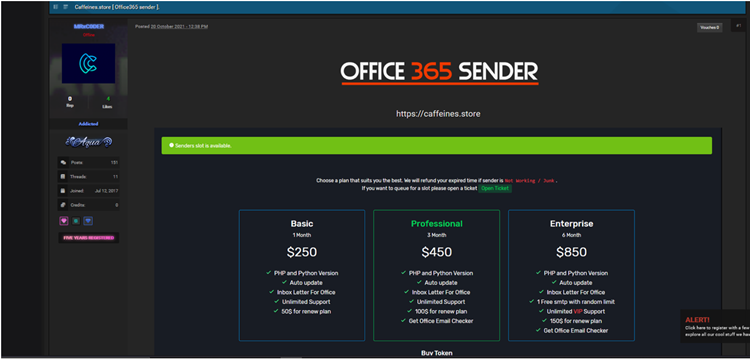
Caffeine makes an effort to make up for it by providing customer support services, anti-detection and anti-analysis technologies, and subscription costs that are roughly 3-5 times higher than the average PhaaS membership cost.
Some of the more sophisticated features the platform provides in terms of phishing options are:
- Mechanisms for customising dynamic URL schemas that help dynamically generate pages with victim-specific data already filled in.
- Ultimate luring pages and first-stage redirect pages for campaigns.
- Geo-blocking, CIDR range-based blocking, and other IP blocklisting options are available.
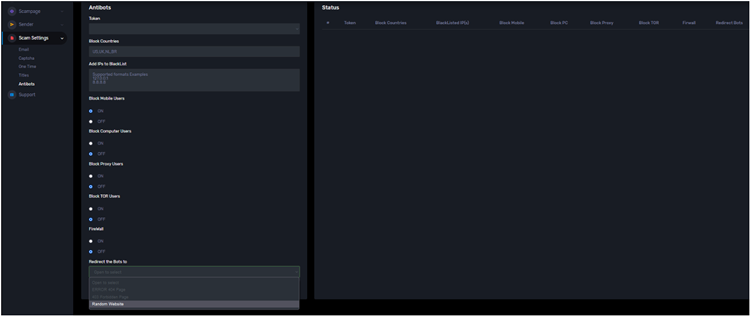
The operators will need to deploy the phishing kit, which is now restricted to a Microsoft 365 login page, after selecting the primary phishing campaign settings, and then choose a phishing template.
Mandiant provides detection advice for stopping Caffeine-backed phishing emails, but the researchers point out that the criminals might use new evasion strategies, making that report’s part obsolete.
Unfortunately, Caffeine has been added as yet another alternative for low-skill cybercriminals looking for automated platforms, and if more templates are added to its collection, the issue may only become worse.




