
Aethon Tug hospital robots have been patched for at least five security flaws that might allow remote attackers to take control of the devices and disrupt the timely distribution of medication and lab tests.
“Successful exploitation of these vulnerabilities could result in a denial-of-service event, full control of robot functions, or the disclosure of sensitive information,” according to a recent advisory from the US Cybersecurity and Infrastructure Security Agency (CISA).
Aethon TUG smart autonomous mobile robots are employed in hospitals all over the world to distribute medication, transfer clinical supplies, and carry out activities such as cleaning floors and collecting lunch plates.
The weaknesses in the TUG Homebase Server component, collectively termed “JekyllBot:5” by Cynerio, effectively allow attackers to obstruct drug distribution, surveil patients, personnel, and hospital interiors using its embedded camera, and get access to personal information.
Worse, an adversary may use the flaws to hijack legitimate administrative user sessions in the robots’ internet site and insert malware to spread further attacks at hospitals.
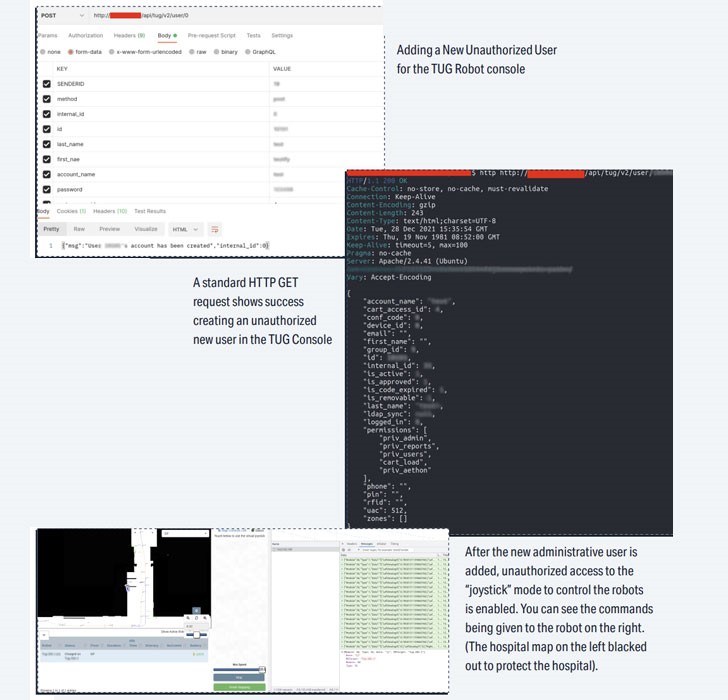
According to the healthcare IoT security business, exploiting the holes may have provided “attackers an access point to laterally travel through hospital networks, do reconnaissance, and eventually carry out ransomware attacks, breaches, and other threats.”
The following is a list of flaws uncovered late last year during an audit on behalf of a healthcare provider client:
- CVE-2022-1070 (CVSS score: 9.8) – To take control of TUG robots, an unauthenticated attacker can connect to the TUG Home Base Server WebSocket.
- CVE-2022-1066 (CVSS score: 8.2) – Unauthenticated attackers can add new users with administrative capabilities, as well as delete or change existing users.
- CVE-2022-26423 (CVSS score: 8.2) – Unauthenticated attackers have unrestricted access to user credentials that have been hashed.
- CVE-2022-27494 (CVSS score: 7.6) – When new reports are created or changed, the Fleet Management Console’s “Reports” tab is vulnerable to stored Cross-site Scripting (XSS) attacks.
- CVE-2022-1059 (CVSS score: 7.6) – The Fleet Management Console’s “Load” tab is vulnerable to reflected cross-site scripting attacks.
To be successfully exploited in an attack, these zero-day vulnerabilities required a very minimal skill level for exploitation, no special rights, and no user contact, Cynerio’s Asher Brass stated.
Hackers might have entirely taken over system control, obtained access to real-time camera feeds and device data, and used the robots to wreak havoc and mayhem at hospitals if they were able to exploit JekyllBot:5.
Source: https://thehackernews.com/2022/04/new-jekyllbot5-flaws-let-attackers-take.html?&web_view=true





