
For first access to corporate networks, ransomware gangs are now targeting a newly patched and actively exploited remote code execution (RCE) vulnerability affecting Atlassian Confluence Server and Data Center instances.
This OGNL injection vulnerability (CVE-2022-26134) allows unauthenticated attackers to remotely take over unpatched servers by creating new admin accounts and executing arbitrary code if properly exploited.
Proof-of-concept exploits were also posted online shortly after active exploitation was revealed in the wild and Atlassian corrected the flaw, lowering the skill level required for exploitation even further.
Multiple botnets and threat actors are actively abusing this security weakness and the already accessible exploits in the wild to deploy cryptomining malware, demonstrating the severity of the flaw and the already available exploits.
Ransomware starts circling unpatched Confluence servers
AvosLocker ransomware affiliates have already hopped on the bandwagon, according to analysts at Swiss cyber threat intelligence firm Prodaft.
They are now systematically infecting several individuals on a large scale by targeting and hacking into Internet-exposed Confluence servers that have yet to be patched.
A picture of AvosLocker’s command and control server, where the threat actors have built a ‘confluence’ campaign, as shown below, demonstrates this targeting.
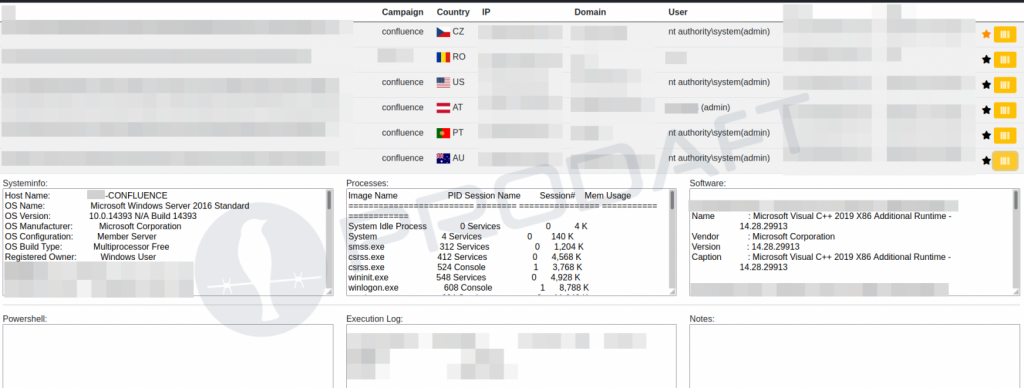
AvosLocker Confluence campaign (Prodaft)
“AvosLocker threat actors seek for susceptible PCs used to run Atlassian Confluence systems by running mass scans on various networks,” Prodaft told BleepingComputer. “AvosLocker has already infected a number of organisations from around the world, including but not limited to the United States, Europe, and Australia.”
Cerber2021 ransomware (also known as CerberImposter) is aggressively targeting and encrypting Confluence instances that aren’t patched against CVE-2022-26134, according to many victims.
Michael Gillespie, the developer of ID-Ransomware, told BleepingComputer that CerberImposter uploads include encrypted Confluence configuration files, indicating that Confluence instances are being encrypted in the wild. The release of CVE-2022-26134 proof-of-concept exploits coincides with an uptick in successful Cerber ransomware assaults.
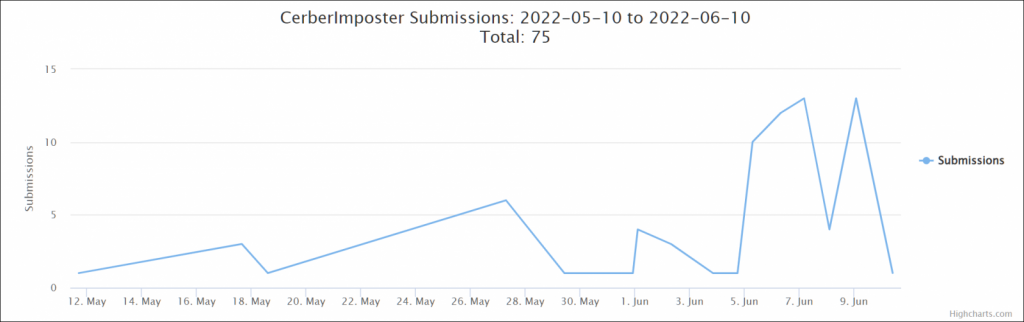
Cerber previously attacked Confluence servers around the world in December 2021, exploiting CVE-2021-26084 vulnerabilities that allow unauthenticated attackers to gain remote code execution on susceptible systems.
Widely exploited in the wild
CISA has instructed federal entities to mitigate the weakness by barring all internet communication to Confluence servers on their networks after cybersecurity firm Volexity published CVE-2022-26134 as an actively exploited zero-day bug last week. Several China-linked threat actors are likely utilising exploits to target weak servers and create web shells, according to Volexity.
Atlassian offered security fixes and recommended customers to patch their installations to prevent ongoing assaults one day after the information on this actively exploited bug was disclosed. “We strongly encourage upgrading to a fixed version of Confluence because the fixed versions of Confluence include multiple other security fixes,” Atlassian noted.
If you can’t upgrade your Confluence Server and Data Center instances right now, you can use a temporary workaround outlined here, which involves upgrading some JAR files on the Confluence server.




