The threat actors responsible for the Windows financial services malware Casbaneiro have been linked to a new Android trojan known as BrasDex. BrasDex has been witnessed in targeting Brazilian consumers as a part of a multi-platform campaign.
According to ThreatFabric, BrasDex has a “complicated key logger system designed to misuse Accessibility Services to retrieve credentials, particularly from a set of Brazilian targeted apps. Also a “fully competent Automated Transfer System (ATS) engine.
According to the Dutch security firm, the command-and-control (C2) facilities being used in conjunction with BrasDex are also utilized to control Casbaneiro. Casbaneiro is known to attack banking institutions and crypto exchange services in Brazil and Mexico.
The combination of Android and Windows spyware campaigns is thought to have infected thousands of people so far.
BrasDex, which poses as a banking app for Banco Santander, is also representative of the latest craze that involves exploiting Android’s Accessibility APIs to log keyboard strokes inputted by victims instead of the traditional technique of using overlay threats to steal qualifications as well as other personal data.
It’s also designed to steal account balance information, which it then uses to take over affected systems and start fraudulent activity programmatically.
Another distinguishing feature of BrasDex is its sole focus on the PIX payroll process. This process allows Brazilian banking customers to send money using only their emails or telephone number.
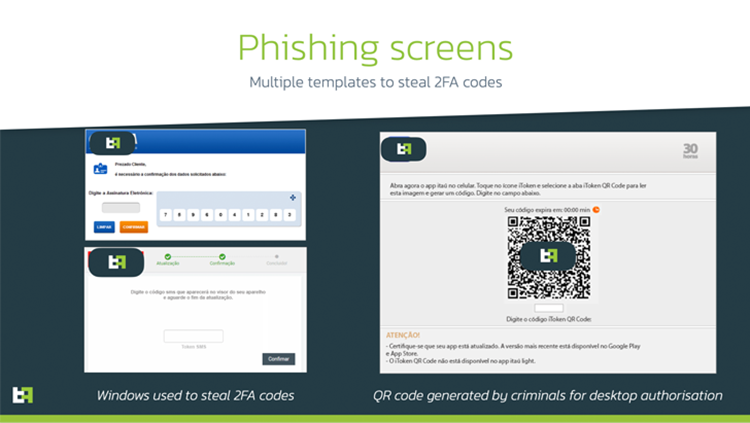
The ATS system in BrasDex is expressly designed to make fraudulent transfers using PIX technology.
Other attacks on Brazil Bank Users
This is not the first time terrible actors have targeted the instant payment ecosystem. Check Point detailed two Android malware families named PixStealer and MalRhino in September 2021. These duped users into trying to transfer their entire account balances to an actor-controlled one.
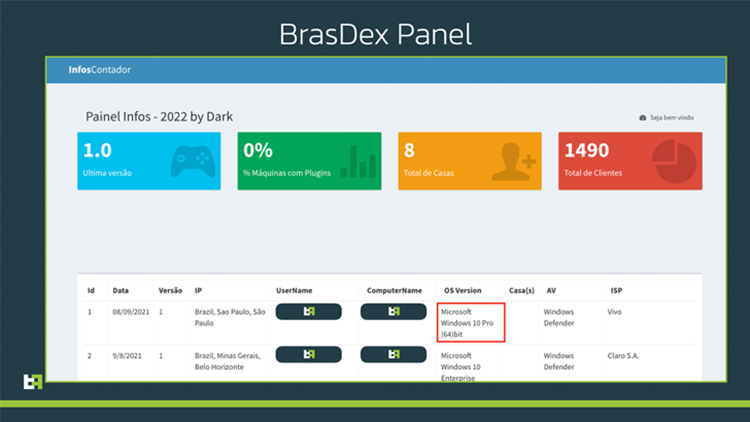
ThreatFabric’s investigation into BrasDex also provided it with access to the C2 panel. Criminal operators use C2 panels to track affected systems and collect data logs exfiltrated from Android smartphones.
As it happens, the C2 panel is also being used to monitor a malware campaign that compromises Windows machines to utilize Casbaneiro, a Delphi-based economic trojan.
This attack chain uses bundle-delivering phishing lures intending to be from Correios, a government postal service. This tricks recipients into running malware through a multi-staged process.
Casbaneiro’s capabilities include the ability to seize authority of banking accounts, take screen captures, undertake keylogging, hijack clipboard data, and even feature as clipper malware to steal crypto transactions.
“Being impartial and filled with malware family members, BrasDex and Casbaneiro form a very risky pair. This enables the actor behind it to target both Windows and Android consumers on a massive scale,” according to ThreatFabric.
“The BrasDex case demonstrates the importance of fraud detection and prevention mechanisms on customer devices. Fraudulent payments made instantly with the assistance of ATS engines look legitimate to financial institution backends. And scam scoring motors because they are created using the same device that customers normally use.”