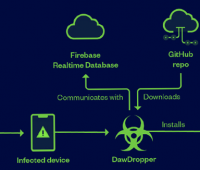
A malicious effort used Android dropper apps that appeared to be innocuous from the Google Play Store to infect consumers’ smartphones with banking malware.…
General
Framing without iframes
Recently, Portswigger researchers discovered new techniques for framing a website without using the iframe element when researching XSS vectors. To include these, PortSwigger has…
Untangling KNOTWEED: A private European Offensive Actor Employing 0-Day Exploits
A private-sector offensive actor (PSOA) was discovered by the Microsoft Threat Intelligence Center (MSTIC) and the Microsoft Security Response Center (MSRC) using a number…
The CISA Director Warns That Ransomware Hackers Will Continue To Target Smaller Critical Infrastructure
Brandon Wales, the executive director of CISA, spoke on how ransomware perpetrators target businesses of all sizes and how CISA wants firms to stop…
4 Steps the Financial Industry Can Take to Cope with Their Growing Attack Surface
The financial services sector has long been at the forefront of technology adoption, but the 2020 pandemic has hastened the adoption of chat-based customer…
Experts Discover Similarities Between BlackMatter Ransomware and New LockBit 3.0
The most recent version of the LockBit ransomware shares characteristics with BlackMatter, a renamed form of the DarkSide ransomware strain that went out of…
Grails Have A Serious Security Flaw That Could Allow Remote Code Execution
The open-source web app framework’s maintainers advise patching all versions, even those that are not thought to be susceptible. A significant security flaw has…
How Cybercriminals Install Malware Programmes via Chat Apps
Automation tools are popular among users on messaging services like Telegram and Discord. Users that engage in cybercrime are among them. Message-sending programmes have…
IT Systems Were Compromised, According To Policybazaar, But No Critical Consumer Data Was Disclosed
The company stated in a notification to exchanges that the detected vulnerabilities in Policybazaar’s IT systems have been resolved and a thorough examination of…
Business Networks Were Vulnerable To Misuse Because Of Zyxel Firewall Flaws
The severity of the code execution bug was reduced by the prior patch’s “high uptake.” Following the identification of two security flaws that exposed…