
The US Cybersecurity and Infrastructure Security Agency (CISA) has included seven new vulnerabilities to its list of actively exploited security concerns, including Microsoft, Linux, and Jenkins vulnerabilities. The ‘Known Exploited Vulnerabilities Catalog’ is a list of vulnerabilities that have been actively exploited in cyberattacks and that Federal Civilian Executive Branch (FCEB) entities are obligated to patch.
“The Known Exploited Vulnerabilities Catalog was established as a living list of known CVEs that entail considerable risk to the federal organization under Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities,” informs CISA. “To safeguard FCEB networks from active threats, BOD 22-01 mandates FCEB agencies to remediate discovered vulnerabilities before the deadline.
“Threat actors can use the vulnerabilities described in the catalogue to carry out a number of attacks, such as stealing passwords, gaining network access, remotely executing commands, downloading and executing malware, or collecting data from devices.”
With the addition of these seven vulnerabilities, the catalogue now has 654 vulnerabilities, as well as the deadlines for federal agencies to implement the patches and security updates. The seven new vulnerabilities discovered this week are mentioned below, and all must be patched by May 16th, 2022, according to CISA.
| CVE Number | Vulnerability Title | Due Date |
| CVE-2022-29464 | WSO2 Multiple Products Unrestrictive Upload of File Vulnerability | 2022-05-16 |
| CVE-2022-26904 | Microsoft Windows User Profile Service Privilege Escalation Vulnerability | 2022-05-16 |
| CVE-2022-21919 | Microsoft Windows User Profile Service Privilege Escalation Vulnerability | 2022-05-16 |
| CVE-2022-0847 | Linux Kernel Privilege Escalation Vulnerability | 2022-05-16 |
| CVE-2021-41357 | Microsoft Win32k Privilege Escalation Vulnerability | 2022-05-16 |
| CVE-2021-40450 | Microsoft Win32k Privilege Escalation Vulnerability | 2022-05-16 |
| CVE-2019-1003029 | Jenkins Script Security Plugin Sandbox Bypass Vulnerability | 2022-05-16 |
What are the ways in which these flaws are employed in attacks?
While knowing that a defect has been exploited is useful, understanding how it is being actively used in attacks is even more so. On April 18th, 2022, the CVE-2022-29464 WSO2 vulnerability was revealed, and a public exploit was released a few days later. The public PoC was quickly leveraged in assaults to deploy web shells and coinminers, according to Rapid7 researchers.
Abdelhamid Naceri identified the CVE-2022-21919 and CVE-2022-26904 Windows ‘User Profile Service Privilege Escalation’ vulnerabilities, which are both bypasses of the original CVE-2021-34484 issue resolved in August 2021. All of these flaws have been publicly exploited, and BleepingComputer has learned that ransomware gangs utilise them to spread laterally throughout a Windows domain.
The CVE-2022-0847 Linux privilege escalation vulnerability known as ‘DirtyPipe’ was first reported in March 2022. Several proof-of-concept exploits were disclosed shortly after its publication, allowing users to achieve root privileges quickly, as seen below.
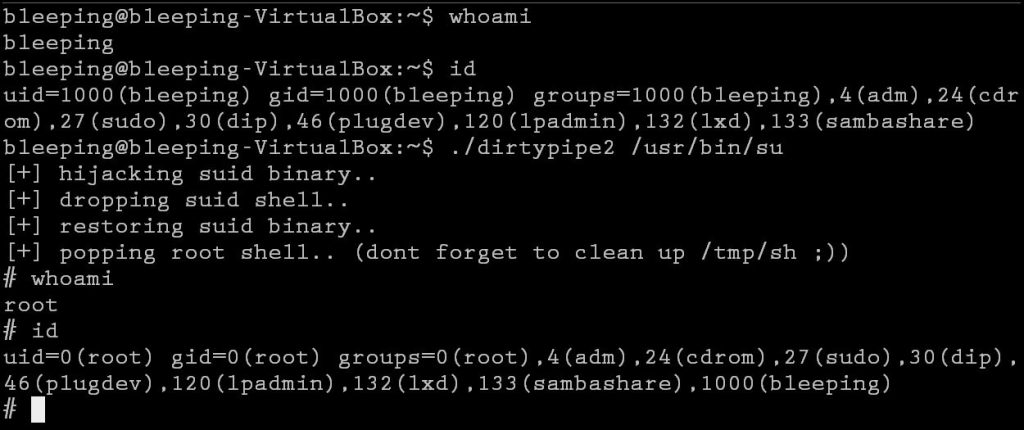
Demonstration of the CVE-2022-0847 Dirty Pipe vulnerability Source: BleepingComputer
The ‘Microsoft Win32k Privilege Escalation’ vulnerabilities, CVE-2021-40450 and CVE-2021-41357, were patched in October 2021 and are an interesting addition to the list, given there has been no public mention of them being exploited in the wild.
Finally, the ‘Jenkins Script Security Plugin Sandbox Bypass’ bug, which has been utilised in the past by the Capoae Malware to deploy XMRig cryptominers, has been tagged as CVE-2019-1003029.
All security professionals and administrators should evaluate the Known Exploited Vulnerabilities Catalog and fix any vulnerabilities they find in their environment.





