A new, widespread phishing campaign has been seen that circumvents security measures and compromises workplace email accounts by leveraging adversary-in-the-middle (AitM) tactics.
It employs an adversary-in-the-middle (AitM) attack method that can get through multi-factor authentication, according to a paper published on Tuesday by Zscaler researchers Sudeep Singh and Jagadeeswar Ramanukolanu. The campaign is specifically meant to get the attention of end users in businesses that utilize Microsoft’s email services.
Fintech, lending, insurance, energy, manufacturing, and federal credit union verticals with locations in the United States, United Kingdom, New Zealand, and Australia are prominent targets.
This is not the first time a phishing assault of this nature has been discovered. Microsoft said last month that since September 2021, around 10,000 companies have been targeted by AitM methods in an effort to access accounts protected by multi-factor authentication (MFA).
Beginning in June 2022, the ongoing effort involves sending targets an email with an attachment that has an invoice theme and contains an HTML file with a phishing URL integrated in it.
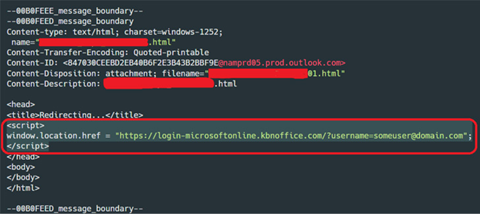
The email recipient is redirected to the phishing website that seems to be a Microsoft Office login page when they open the attachment in a web browser, but not before the compromised system is fingerprinted to see if the victim is truly the intended target.
In situations when MFA is enabled, a security measure that stops the attacker from logging into the account with just the stolen credentials, AitM phishing assaults go beyond the usual phishing tactics aimed to steal credentials from unknowing users.
To get around this, a phishing kit-created fake landing page acts as a proxy, intercepting and relaying all communication between the client (i.e., victim), and the email server.
The researchers explained that the kits “intercept the HTML material received from the Microsoft servers and, before passing it back to the victim, the kit variously manipulates the content as needed, to make sure the phishing operation works.”
To ensure that the back-and-forth with the fake website continues during the session, this also requires replacing all of the links to the Microsoft domains with comparable ones to the phishing domain.
Eight minutes after stealing the credentials, according to Zscaler, the attacker was seen manually going into the account, reading emails, and looking up user profiles.
Additionally, the compromised email accounts may occasionally be used to send additional phishing emails as part of the same campaign to commit business email compromise (BEC) schemes.
The researchers stated that although security measures like multi-factor authentication (MFA) give an additional layer of security, they shouldn’t be viewed as a foolproof defense against phishing attempts.
Threat actors can get beyond both conventional and cutting-edge security measures by using advanced phishing kits (AiTM) and cunning evasion strategies.





