After hackers gained access to an internal customer assistance and account administration tool. The email marketing company MailChimp had another breach that gave threat actors access to the information of 133 customers.
According to MailChimp, the attackers used social engineering to trick contractors and workers of the company into giving them access to employee login information.
The hack was initially discovered on January 11th, when MailChimp discovered an unauthorized user using their support resources.
According to a statement on the security incident, “After we uncovered evidence of an unauthorized actor, we temporarily banned access permission for Mailchimp accounts where we observed suspicious behavior to protect our users’ data.”
Less than 24 hours following the initial discovery, on January 12th, we alerted the principal contacts for all impacted accounts.
MailChimp sent the following statement in response to our inquiries on the compromise.
MailChimp informed that no credit card or login data was stolen due to the incident, even though disclosing client information is not a regular practice.
“We are investigating the issue, and part of it entails figuring out how to make our platform even more secure. We do not comment publicly about our activities due to operational security concerns. – MailChimp
One of the victims of this hack is the viral WooCommerce eCommerce WordPress plugin, as TechCrunch reported.
Customers have received emails from WooCommerce. They were informed that their identities, store URLs, addresses, and email accounts were exposed due to the MailChimp breach.
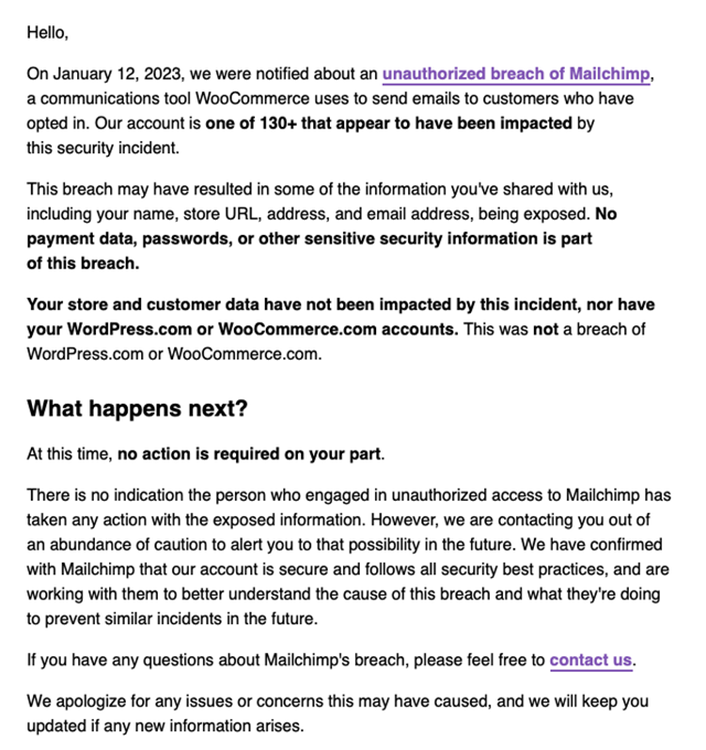
Even though threat actors frequently exploit this kind of information for focused phishing scams to steal passwords or install malware, WooCommerce claims that there is no evidence that the stolen data has been misused.
Later Findings
Owners of Trezor hardware wallets started getting phony data breach warnings in April 2022, which prompted users to download a bogus version of the Trezor Suites program that’d steal their recovery seeds.
The email list utilized here was a Trezor listserv obtained in a MailChimp breach, Trezor claimed on Twitter.
Later, MailChimp acknowledged that the breach was more serious. As a result of staff falling for a social engineering trick, threat actors gained access to 319 MailChimp accounts and could export the data of 102 clients.
The marketing business acknowledged that this information was used in phishing emails. But would not provide further details on the attacks.
A second breach occurred in August 2022 due to staff members falling for the ‘0ktapus’ Okta phishing scam.
At the time, MailChimp informed that the malicious actors had gained access to 214 consumer profiles. And focusing on those interested in cryptocurrencies.
The August incident impacted customers like Edge Wallet, Cointelegraph, NFT developers, Ethereum FESP, Messari, and Decrypt.





