According to one security expert, e-commerce websites generally struggle to keep their sites secure and frequently include weak code from supply-chain partners or third parties that is simple for hackers to infiltrate and may have unintended consequences.
Kim DeCarlis, chief marketing officer at cybersecurity firm PerimeterX, wrote in an email to Threatpost, “This is another example of the web attack lifecycle—the cyclical and continuous nature of cyberattacks—where a data breach on one site, perhaps as a result of a Magecart attack, fuels carding, credential stuffing, or account takeover attacks on another site.”
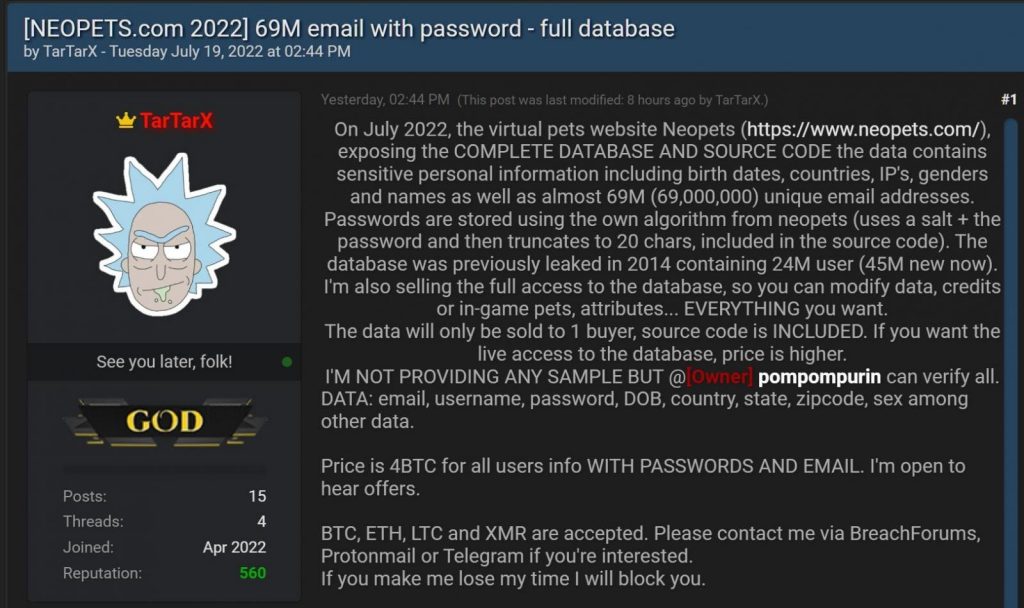
TarTarX claims that they obtained the database and about 460MB (compressed) of source code for the neopets.com website in a conversation with BleepingComputer.
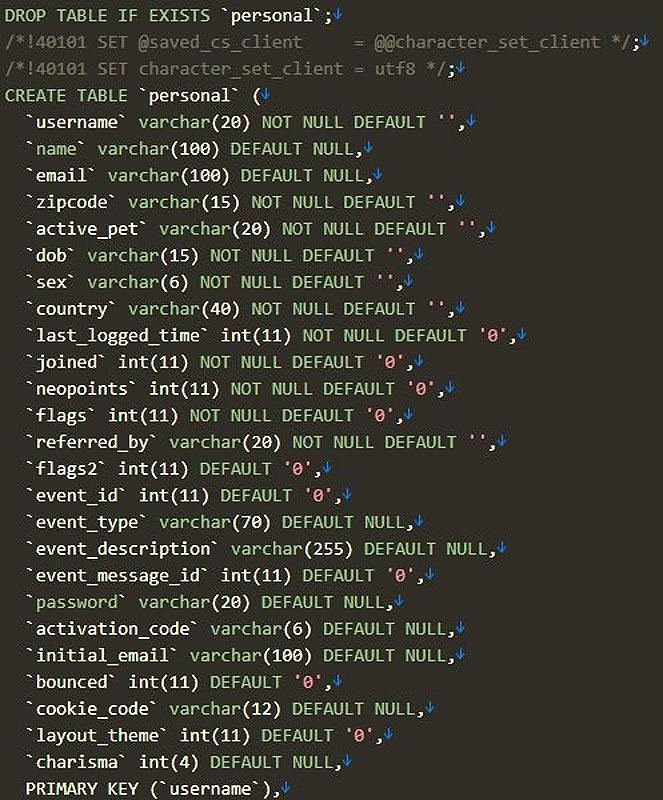
In a screenshot provided to BleepingComputer, you can see that the data includes members’ usernames, names, email addresses, zip codes, dates of birth, gender, countries, an initial registration email, and other site/game-related information. The seller claims that this database contains the account information of over 69 million users.
The hacker told us that they did not demand money from Neopets’ owners, Jumpstart, in exchange for access to the website, but that they had heard from people interested in buying the data instead.
BleepingComputer has not yet been able to independently confirm the database’s legitimacy. The proprietor of the Breached.co hacking site, pompompurin, however, was able to confirm the hacker’s assertions by creating an account on Neopets.com and requesting a copy of their freshly created record from the database.
pompompurin wrote in the Breached.co forums, “Vouch, I established an account on the website and he sent the whole entry.
This verification also demonstrated that TarTarX had access to the neopets.com website even after they started selling the data.
Breach is confirmed
The Neopets team, known by the TNT acronym, stated on the unofficial Neopets Discord service that they are aware of the security incident and are trying to resolve it after word of the breach circulated online.
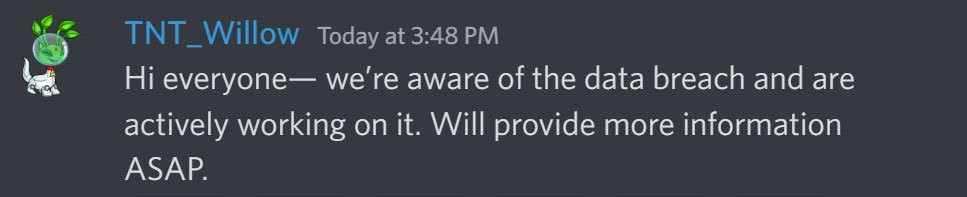
Changes to your Neopets account password may not help secure it if the attackers still have access to their servers, volunteer Discord moderators have warned.
An message on the Neopets Discord server states that “We should emphasise that the effectiveness of changing your Neopets password is currently dubious as long as hackers have live access to the database, as they can simply verify what your new password is.”
We are unable to provide you with a strict recommendation for the best course of action in the circumstances. However, it is strongly encouraged that you change your password on such websites to something different if you use the same Neopets password on other websites.
Neopet users should follow a subject on the Neopets Help Site Jelleyneo or the Jelleyneo Twitter account to receive the most recent updates on the data breach, which will be updated as they become available.
Neopets has already experienced a data breach, with member information from a breach that happened in 2012 making its way online in 2016.
Others already had access
Despite the fact that this breach seems to be brand-new, Neopets has a history of having systems improperly accessed.
Neo truths, a Reddit member, informed BleepingComputer that they have had “read” access to the database for at least a year as a result of discovering vulnerabilities in the website’s stolen source code.
Neo truths informed us that they make use of this access to research and discuss game mechanics on Reddit.
Neo Truths, however, claimed that they altered the game as an April Fool’s joke by injecting code into a PHP eval() function using someone else’s hack.
Unfortunately, according to neo truths, there are only a few developers to manage the enormous amount of code that is dispersed over numerous servers. In the past, this staff shortage has resulted in various breaches by numerous individuals, with one actively used exploit being reported to the developers who subsequently rectified it.
“Several persons have access for years and there are numerous breaches in Neo. The only difference is that they use it privately (primarily for off-site marketing and selling), and I try to address certain known flaws with actual data “neo truths says in a Reddit remark.
“I have already reported two exploits that gave unauthorised users access to databases (one of them for a difficult time determining how long). If I hadn’t had access to them, I might not have found them.
“I could always decide to divulge my own approach and therefore lose access, which would be the right thing to do, but that would also allow the others to operate freely. But I do recognise that from a user’s perspective, it’s really concerning that someone may access their data at any time.
Although neo truths has long had access to the Neopets database, they have assured BleepingComputer that they were not engaged in the most recent breach and that they think the threat actors entered the system through a weakness unrelated to Neopets programming.
According to neo truths, the exploit this time is just a common one that many websites use. It has nothing to do with Neo Code.





