The information-stealing malware known as ChromeLoader has undergone recent iterations, showing how quickly its feature set has changed.
ChromeLoader was discovered in January 2022 and has been disseminated as ISO or DMG file downloads promoted using QR codes on Twitter and free gaming websites. Its main uses are to hijack victims’ browser searches and display adverts.
The larger cybersecurity community has also referred to ChromeLoader as ChromeBack and Choziosi Loader in code. The fact that the spyware is designed as a browser extension rather than a Windows executable (.exe) or Dynamic Link Library makes it noteworthy (.dll).
Malvertising campaigns on pay-per-install websites and social media generally tempt unaware users into downloading movie torrents or cracked video games.
In addition to asking intrusive rights to access browser data and manipulate web requests, it is also intended to record users’ Google, Yahoo, and Bing search engine queries, allowing threat actors to efficiently harvest their online activity.
While the original ChromeLoader malware variant for Windows was discovered in January, a macOS variation of the virus first surfaced in March to spread the malicious disc image (DMG) files that contained the rogue Chrome extension (version 6.0).
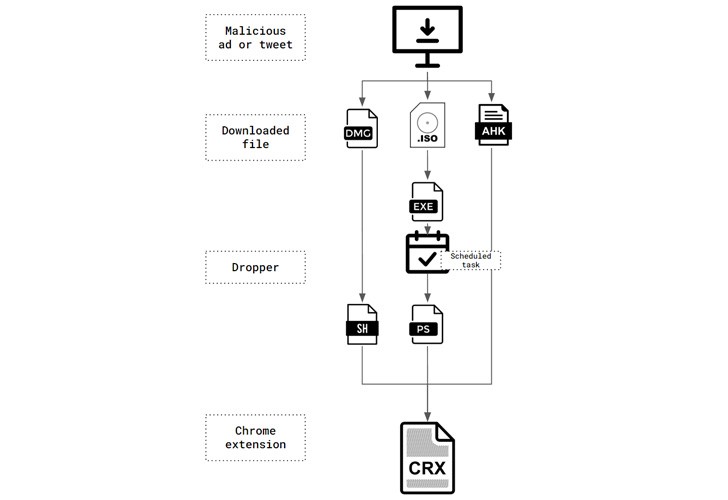
However, according to a recent investigation by Palo Alto Networks Unit 42, the malware was first used in an attack in December 2021, utilising an executable that had been AutoHotKey-compiled rather than the later-recognized ISO files.
Unit 42 researcher Nadav Barak claimed, “This malware was an executable file developed using AutoHotKey (AHK) — a framework used for scripting automation,” adding that it was used to distribute “version 1.0” of the browser add-on.
Additionally, it is said that the virus’s inital iteration lacks the ability to obfuscate, a characteristic that later versions of the malware have adopted to hide its destructive code and intended use.
A previously unreported campaign that uses the 6.0 version of the Chrome extension and relies on an ISO image that contains a seemingly innocent Windows shortcut but actually serves as a conduit to launch a hidden file in the mounted image that deploys the malware has also been noticed since March 2022.
The makers of ChromeLoader “used several programming frameworks, upgraded functionality, advanced obfuscators, addressed bugs, and even included cross-OS support targeting both Windows and macOS in a short period of time, demonstrating how determined cybercriminals and malware authors can be,” stated Barak.
Reference: https://thehackernews.com/2022/07/researchers-uncover-new-variants-of.html?&web_view=true




