A US$1 million extortion demand has been made against the second-largest telecommunications provider in Australia in an effort to stop the sale of potentially 11.2 million sensitive client details, according to the attacker. The Australian Federal Police is looking into the Optus data breach, one of the biggest in the nation’s history. On September 14 Optus discovered a division of Singaporean telecoms giant Singtel Group.
On a well-known data leak site early on Saturday, a person going by the moniker “Optusdata” posted two samples of the allegedly stolen data. The hacker claims that if Optus pays $1 million in monero cryptocurrency, it would be able to stop the sale of the data to other online criminals.
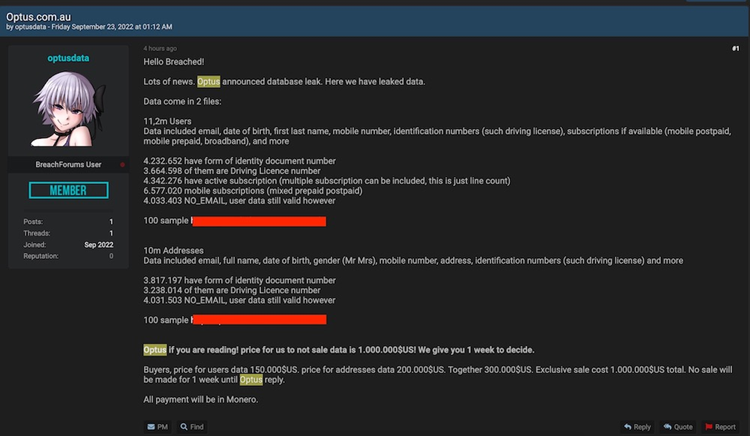
According to Optusdata, the company has one week to make a payment before the data can be purchased in packages.
The two sets of data samples that have been made public include about 100 records and data fields like name, email address, physical address, passport number, licence number, birth date, whether or not a person is a home owner, and more. Current and previous Optus subscribers are included in the data.
On Saturday, an Optus representative stated, “We are evaluating the authenticity of this” information.
Leaked Data Appears Legitimate
ISMG discovered compelling evidence that the data most likely came from Optus.
Entering the email addresses into Have I Been Pwned is one approach to determine whether a breach originated from the company it was said to have originated from. Data breach notification is provided by HIPB. People can sign up to receive notifications when a new breach involves their email address. To check if an email address has ever been compromised, type it into HIBP.
23 email addresses were examined by ISMG. Six hadn’t, although the majority had in earlier breaches. That suggests that the Optus sample data is authentic.
ISMG discovered compelling evidence that the data most likely came from Optus.
Entering the email addresses into Have I Been Pwned is one approach to determine whether a breach originated from the company it was said to have originated from. HIPB provides data breach notification. People can sign up for notifications when a new breach involves their email addresses. To check if an email address has ever been compromised, type it into HIBP.
23 email addresses were examined by ISMG. Six hadn’t, although the majority had in earlier breaches. That suggests that the Optus sample data is authentic.
Breach Source: Unauthenticated API
Australian broadcaster ABC on Friday disclosed the potential reason for the breach.
An API for an Optus customer identity database was made available to a test network that “happened to have internet connection,” according to a “senior source” inside Optus.
Software interfaces called APIs enable data flow between systems, but if they are accessible to the internet directly, they run the danger of exposing sensitive data to hackers. Optus refused to respond to the explanation and refuted the idea of “human error”.
On the forum where the data samples were made available, ISMG contacted Optusdata and inquired as to how the data was taken. The individual acknowledged that the data had been stolen from an untrusted API. Or to put it another way, anyone could use the API’s features without having to create an account.
In a notification, Optusdata stated: “Nothing to authenticate. That access control is subpar. Everyone is welcome to use the free internet.”
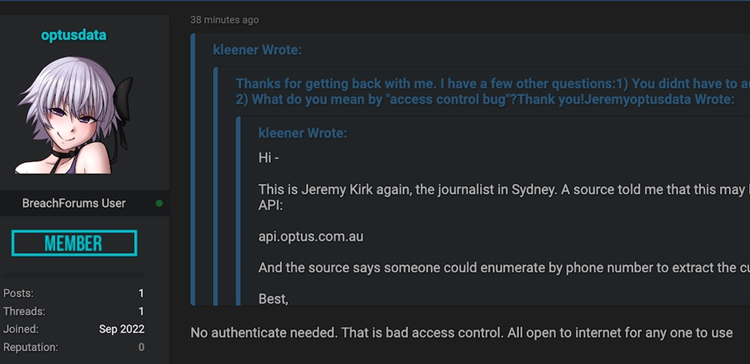
“api.www[dot]optus.com.au” was the API endpoint. Optusdata claims that despite the strange URL’s success in leaking the data, a DNS error would have otherwise happened. Since that API is no longer available, Optus is no longer at risk. Optus consumers had access to their own data in part thanks to the API.
The Sources
On Saturday, a different anonymous source provided ISMG with the identical API endpoint. That individual said Google Cloud/Apigee hosts it. Security alerts raised when Optusdata began often using that API. That API was sending a suspiciously large amount of data, which indicated nefarious activity to Optus.
Optusdata said that they enumerated the customer records using the contactid field seen in the exposed data samples. How Optus used the “contactid” is unknown. The hacker meant that they used the API to sequentially access and download the customer records when they said they were enumerating.
When informed of this information on Saturday night, an Optus spokesman stated the firm did not immediately have a comment.
Notifying Customers
Optus informs the affected parties now on the amount of data disclosed that did not apply to every impacted person. For individuals who are at a higher risk, Optus said on Friday that it will provide “professional third-party monitoring services.” Also cautioned customers on the lookout for phoney emails and text messages.
The Office of the Australian Information Commissioner, which is the nation’s data protection agency, is only one of the regulatory inquiries that Optus will have to respond to over its data handling procedures.
The Attorney General’s office in Australia is reportedly demanding an “urgent” meeting with Optus to see how the business intends to lessen the impact of the breach on affected people, according to The Guardian.
In a different piece, The Guardian stated that Optus opposed strengthening consumer rights to control their data at a federal review of the nation’s Privacy Act in 2020.
Optus disagreed with offering customers the option to delete their personal data, citing “major technical difficulties,” according to the article. According to the article, the company also opposes giving customers more legal leverage to sue businesses for data breaches.



