Aethon Tug hospital robots have been patched for at least five security flaws that might allow remote attackers to take control of the devices and disrupt the timely distribution of medication and lab tests. “Successful exploitation of these vulnerabilities could…
Latest posts - Page 64
McDonald’s Warns Customers of the Data Breach in Costa Rica
McDonald’s customers in Costa Rica have been notified of a data breach in which their personal information was obtained. Client names, marital status, address, email, document identity number, and phone number have been left exposed, according to the advisory sent…
Elementor, a WordPress website builder plugin, plagued with a vulnerability
Elementor, a WordPress website builder plugin that has more than five million active installations, has a vulnerability that can lead to authenticated remote code execution. The vulnerability can be exploited to seize control over affected websites. Plugin Vulnerabilities revealed the…
VMware vulnerability allows attackers to take control of the Cloud infrastructure
On Thursday, VMWare, a cloud computing and virtualisation technology firm, pushed an update to fix a critical vulnerability in its Cloud Director product. The vulnerability could be exploited to execute codes remotely. The vulnerability labelled CVE-2022-22966 scores 9.1 out of…
LFI Vulnerability of Critical Importance was reported in Hashnode Blogging Platform
Hashnode, a developer-oriented blogging platform, has a previously undiscovered local file inclusion (LFI) vulnerability that might be exploited to gain access to sensitive data such as SSH keys, the server’s IP address, and other network information. The LFI is based…
The Qbot malware has switched to a new infection vector: Windows Installer
Phishing emails with password-protected ZIP archive attachments containing malicious MSI Windows Installer packages are now being used by the Qbot botnet to spread malware payloads. This is the first time the Qbot operators have used this strategy, which differs from…
APT Hackers Targeting ICS/SCADA Systems with Specialized Malware, the US Warns
Nation-state actors are using specialised malware to maintain access to industrial control systems (ICS) and supervisory control and data acquisition (SCADA) equipment, according to the US government. In an alert, numerous US agencies stated that “APT actors have created custom-made…
Fakecalls: A Novel Approach to Banking Customer Service Frauds
Fakecalls is a financial malware that targets Android users, hijacking their calls to a bank’s customer service number and connecting them directly with hackers. About Fakecalls scam The spyware, according to Kaspersky, masquerades as a mobile app from well-known banks…
Operation TOURNIQUET shuts down RaidForum, an illegal dark web marketplace
RaidForums, an illegal dark web marketplace, has been closed, and its infrastructure seized in an international law enforcement Operation TOURNIQUET. Europol’s European Cybercrime Center has coordinated the operation. The Department of Justice, in a press release, announced the taking down…
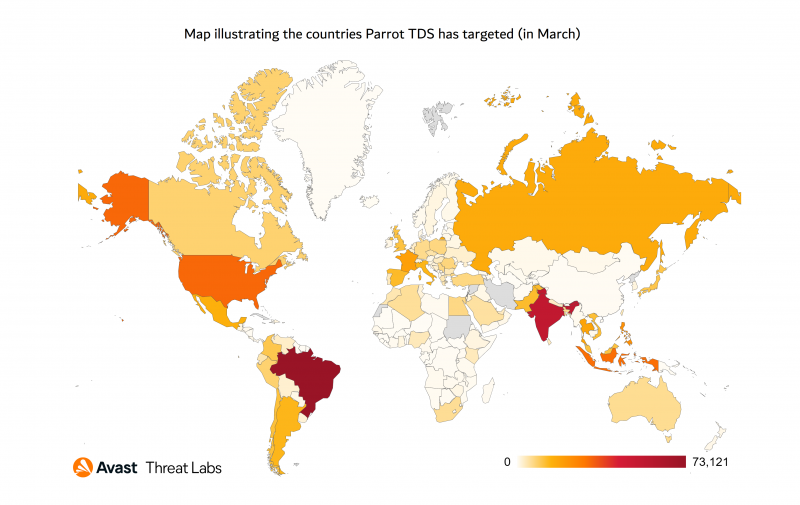
Parrot Traffic Direction System (TDS) is a new web redirection service by Parrot
In harmful campaigns, a Traffic Direction System (TDS) is used to lead individuals who fit a specific profile to phishing sites. The FakeUpdate campaign Avast researchers found Parrot TDS and revealed that it’s presently being utilised in the FakeUpdate (aka…