New connections between PrivateLoader, a popular pay-per-click (PPI) malware firm, and ruzki Pay-Per-Install Services provider. They have been discovered by cybersecurity researchers.
According to SEKOIA, “the threat actor ruzki (aka les0k, zhigalsz) advertises their PPI service on unofficial Russian-language message boards and their Telegram channels. They were under the moniker ruzki or zhigalsz from at least May well 2021.”
The cybersecurity firm claimed that after looking at the two solutions, it came to the conclusion that PrivateLoader is the exclusive loader used by the ruzki Pay-Per-Install Services malware support.
As its name suggests, PrivateLoader works as a C++-dependent loader to download and install additional malicious payloads on infected Windows systems. It is mainly distributed through Seo-optimized websites that claim to offer cracked software.
Although Intel471 announced it for the first time in February. It is also said to have been in use as early as May 2021.
The ransomware strains Djvu and End, as well as the commodities malware families. These include Redline Stealer, Socelars, Raccoon Stealer, Vidar, Tofsee, Amadey, and DanaBot. These are some of the most well-known groups spread by PrivateLoader.
The Malware
The malware-distributing NetDooka framework was discovered via a Pattern Micro evaluation from May 2022. As of July 2022, India and Brazil are expected to have serious bacterial infections, according to follow-up research from BitSight late last month.
A recent shift noticed by SEKOIA is the use of the VK.com paperwork service rather than Discord to house the damaging payloads. This change is likely the result of increased monitoring of the platform’s material delivery network.
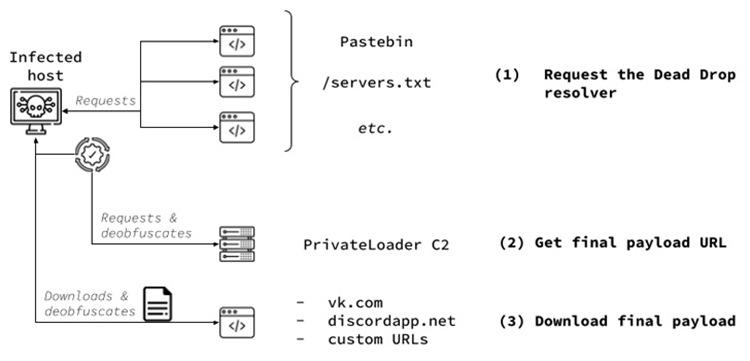
Additionally set up for exfiltrating data, PrivateLoader can connect to command-and-control (C2) servers to get data. There are four active C2 servers as of mid-September, two of which are located in Russia and one each in Czechia and Germany.
The PPI assistance operating PrivateLoader is very sought-after and well-known to attackers on dark web markets, according to the researchers. They noted that the malware’s wide spectrum of families suggests a wide range of threat actors or intrusion teams that employ it.
SEKOIA further stated that it has discovered connections between PrivateLoader and ruzki. It is a dangerous actor that charges $70 for bundles of 1,000 installations on infected programmes worldwide, or more specifically in Europe ($300) or the United States ($1,000).
These ads, which are posted on the Lolz Guru cybercrime discussion board, target risk actors (also known as potential customers). They want to deliver their payloads via the PPI firm.
The affiliation is mostly based on the observations listed below.
There is an overlap between the PrivateLoader C2 servers and the URLs that are made available to subscribers by ruzki. So that they can view installation statistics linked to their strategies.
Ruzki references can be found in PrivateLoader botnet sample names that were used to distribute the Redline Stealer. For example, ruzki9 and 3108 RUZKI, and in the Redline Stealer itself.
The fact that PrivateLoader and ruzki both launched in May 2021 and that the ruzki operator refers to their service as “our loader” in Russian on its Telegram channel.
The researchers noted that “Spend-for-every-Put in providers frequently played a crucial role in the dissemination of commodity malware.”
“It is quite likely that more PrivacyLoader-related activity will be seen in the short term”. As “yet another turnkey solution cutting the cost of entry into the cybercriminal market. And a company contributing to a continual professionalization of the cybercriminal ecosystem.”
Did you find this article to be interesting? Follow THN on Facebook, Twitter, and LinkedIn to see more original content that we post.



