A threat actor is using password “cracking” software for programmable logic controllers to infect industrial control systems (ICS) and turn them into a botnet (PLCs).
The PLC and HMI (human-machine interface) terminals from Automation Direct, Omron, Siemens, Fuji Electric, Mitsubishi, LG, Vigor, Pro-Face, Allen Bradley, Weintek, ABB, and Panasonic are advertised with password recovery solutions on numerous social media sites.
In one incident involving DirectLogic PLCs from Automation Direct, security researchers at industrial cybersecurity firm Dragos found that the “cracking” programme was utilising a known vulnerability in the device to extract the password.
However, Sality, a piece of malware that builds a peer-to-peer botnet for various activities that need the power of distributed computing to complete more quickly, was also dumped by the tool in the background (e.g. password cracking, cryptocurrency mining).
Researchers from Dragos discovered that the malicious malware could only use serial-only connections with the exploit it was using. The seriousness of the situation is increased by the fact that they were able to duplicate it across Ethernet.
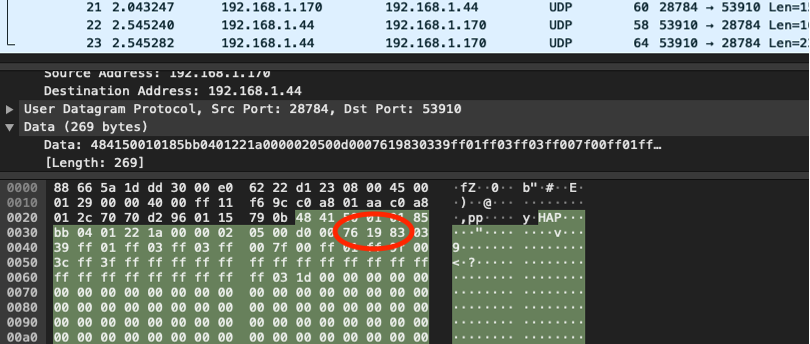
Dragos discovered the vulnerability after reviewing the Sality-laced software, and the seller promptly made the necessary countermeasures available.
Administrators of PLC from other vendors should be mindful of the risk of utilising password cracking tools in ICS setups, though, as the threat actor’s campaign is still active.
Operational technology engineers should steer clear of password cracking tools, regardless of how justified their use may be—especially if their origin is unknown.
Dragos advises contacting them or the device manufacturer for advice and guidance in situations where you need to recover a password (because you lost it or the person who had it is no longer a colleague).
Sality P2P botnet
Sality is a venerable piece of malware that has evolved over the years to include capabilities that enable it to kill processes, establish connections to external websites, download extra payloads, or steal data from the host.
The malware can also exploit the Windows autorun capability to replicate itself onto network shares, external discs, and removable storage devices, which could spread it to other systems. It can even insert itself into active processes.
Dragos’ analysis of this particular sample suggests that it was designed to steal cryptocurrency. According to the researchers, the malware included a payload that redirected cryptocurrency transactions by stealing the contents of the clipboard.
However, a more skilled attacker may use this point of access to sabotage operations and cause more significant damage.
In this specific instance, the victim became suspicious after using the malicious programme since Windows Defender sent numerous threat alerts and the CPU use level increased to 100%.





