An Internet Explorer zero-day flaw was actively exploited by a North Korean malicious attacker to target South Korean consumers by relying on the current Itaewon Halloween crowd crush to deceive victims into downloading malware.
The current round of attacks by ScarCruft, also known as APT37, InkySquid, Reaper, and Ricochet Chollima. It was discovered by Google Threat Analysis Group experts Benoît Sevens and Clément Lecigne.
In a Thursday analysis, TAG said that the group had “historically targeted South Korean users, North Korean defectors, policymakers, journalists, and human rights advocates.”
The latest discoveries show how the threat actor is still abusing Internet Explorer vulnerabilities like CVE-2020-1380 and CVE-2021-26411 to drop security holes like BLUELIGHT and Dolphin. The latter was exposed by the Slovak cybersecurity company ESET late last month.
RokRat is a Windows-based remote management trojan with a variety of features that let it take screenshots, and track keystrokes. And even gathering Bluetooth device data, is another important weapon in its armory.
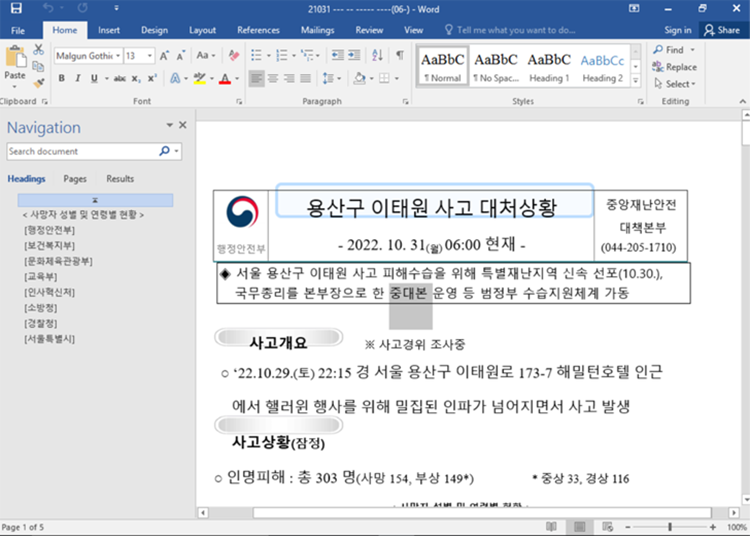
The malicious Word Documents file that was used in the assault chain that Google TAG saw was submitted to VirusTotal on October 31, 2022. It takes advantage of yet another CVE-2022-41128 Internet Explorer zero-day vulnerability inside the JScript9 JavaScript engine, which Microsoft patched last month.
The file mentions the October 29 incident that took occurred in the Itaewon neighborhood of Seoul. Seoul uses public interest in the tragedy to extract an attack for the vulnerability upon opening it. The attack is facilitated by the reality that Office produces HTML material using Internet Explorer.
Final Thoughts
The Shadow Chaser Group posted the exact same Word document on October 31, 2022. Referring to it as an “interesting DOCX insertion template sample” that came from Korea, as the MalwareHunterTeam notes.
Following successful exploitation, a shellcode is sent out that deletes all traces by wiping the Internet Explorer caches. And history and downloading the payload for the next stage.
Even though it’s assumed to have entailed the installation of RokRat, BLUELIGHT, or Dolphin. Google TAG stated that it was unable to retrieve the follow-on malware employed in the campaign.





