Cisco Talos found a malicious campaign using a modularized attack method to distribute Cobalt Strike beacons on compromised endpoints.
The initial attack vector is a phishing email with a malicious Microsoft Word document attachment. Attachment tries to exploit the Microsoft Office remote code execution vulnerability CVE-2017-0199. When a victim accesses the malicious Word document template, it downloads from a Bitbucket repository under the attacker’s control.
Talos identified two attack strategies used by the attacker in this campaign: one in which the downloaded DOTM template executes an embedded malicious Visual Basic script that generates and runs other VB and PowerShell scripts.
A Cobalt Strike beacon leaked is the payload. The configuration of the beacon uses the redirection approach to disguise the beacon’s traffic and includes commands to perform targeted process injection of arbitrary programmes.
Despite the Cobalt Strike beacon being the payload found in this campaign, Talos also noticed the use of the Redline information-stealer and Amadey botnet executables.
This campaign is an illustration of how a threat actor would create and run malicious scripts in the victim’s system memory. To effectively defend against fileless threats, defenders need to include behavioral protection capabilities in the organization’s defense.
To counter the attacker’s attempts in the earlier stage of the attack’s infection chain, organizations should build layered security capabilities and maintain constant vigilance on the Cobalt Strike beacons.
Initial vector
The initial infection email is designed to persuade the recipient to read the Word document that is attached and to divulge some of their personal data.
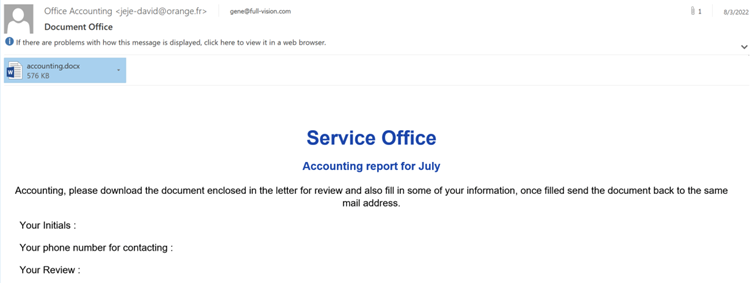
The lures used by the maldocs contain text pertaining to the gathering of personally identifiable information (PII), which is used to assess a job applicant’s suitability for employment with U.S. federal government contractors and their purported enrollment status in the government’s life insurance programme.
The text in the maldoc is similar to what would be found on an American declaration form. The Office of Personnel Management (OPM) is the federal government of the United States principal human resources organization and personnel policy manager.

Attack methodologies
The initial infection vector, use of the remote template injection mechanism, and the final payload were all the same across the two attack tactics Talos discovered for this campaign.
Method 1
The following is a modularized approach for implanting a Cobalt Strike beacon with a number of infection chain stages:
1. maldoc: DOTM template
2. VBA dropper
3. VB script
4. PowerShell script
5. PowerShell downloader
Method 2
This campaign’s second attack strategy uses less complex Visual Basic and PowerShell scripts, but it is still modular. We discovered that the actor used a 64-bit Windows executable downloader to carry out the PowerShell commands necessary to download and run the Cobalt Strike payload during the assault chain. The method follows similar methods stated in method 1.
Payload
Talos found that the Cobalt Strike beacon is the campaign’s ultimate payload. Cobalt Strike is a modularized and adaptable attack architecture. Threat actors have the ability to add or delete features in accordance with their nefarious purposes. The use of Cobalt Strike beacons in the attack’s infection chain enables the attackers to conceal their malicious traffic from network detections by mixing it with legitimate traffic. The attacker can also carry out a number of malicious actions, such as injecting additional malicious binary into the running processes of the infected machines.
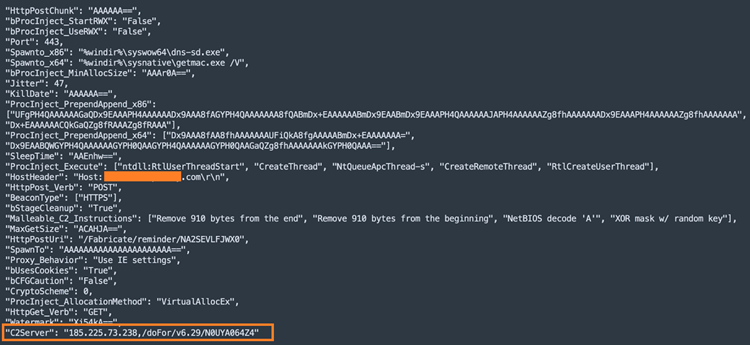
The Cobalt Strike beacon configurations from this campaign revealed a number of the beacon binary’s properties, including:
- C2 server.
- Communication protocols.
- Process injection techniques.
- Malleable C2 Instructions.
- Target process to spawn for x86 and x64 processes.
- Watermark : “Xi54kA==”.
Malicious repository
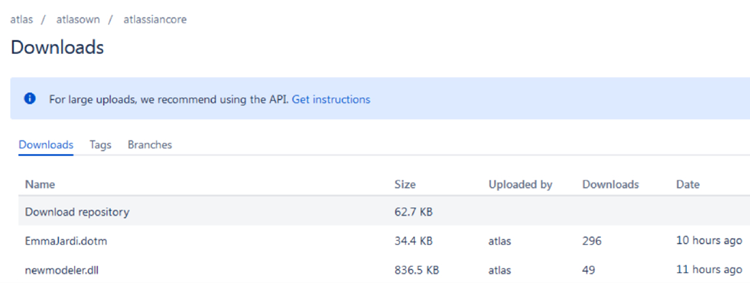
Cobalt Strike DLLs and malicious DOTM templates were hosted on Bitbucket by the campaign’s attacker using various identities. The following Bitbucket address the associated with this campaign: https[://]bitbucket[.]org/atlasover/atlassiancore/downloads and https[://]bitbucket[.]org/clouchfair/oneproject/downloads. These addresses are under the control of two attackers.
The account “atlasover” was active during the time of our study and provided us with hosting details for some of the malicious files used in this campaign.
Command and control
Talos found the Ubuntu Linux version 18.04-powered C2 server used in this campaign. It is based in the Netherlands and a part of the Alibaba cloud infrastructure and has the IP address 185[.]225[.]73[.]238.
The C2 server has two self-signed SSL certificates with the serial numbers 6532815796879806872 and 1657766544761773100 that are valid from July 14, 2022 to July 14, 2023, according to the findings of a Shodan search.
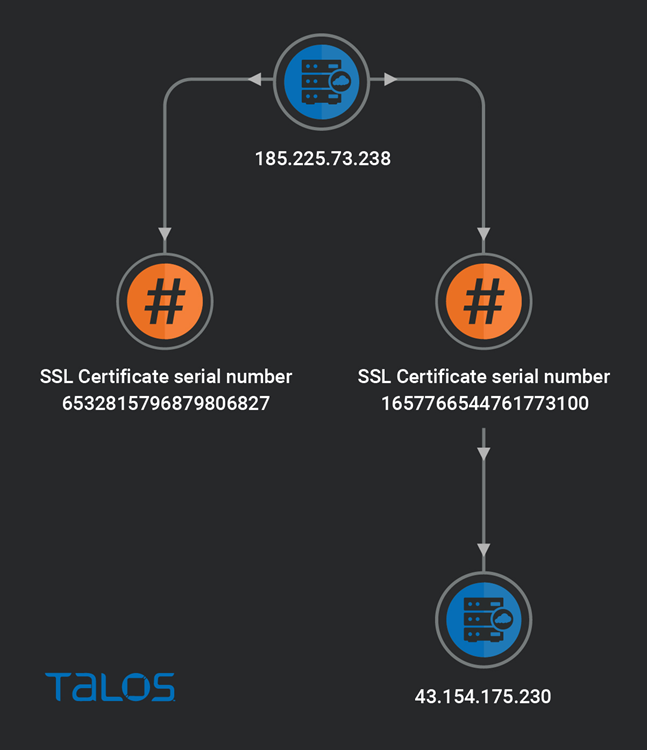
By focusing on SSL certificates found a second Cobalt Strike C2 server with the IP address 43.154.175.220 running Ubuntu Linux version 18.04 in Hong Kong. This server is also a part of Alibaba’s cloud infrastructure. The same actor involved in the attack runs the campaign.





