Businesses are aware that their client-side scripts must be protected. CSPs, or content security policies, are a terrific tool for achieving that. CSPs, however, are laborious. If you make a mistake, there could be a huge client-side security gap. Finding those gaps requires spending numerous, time-consuming hours (or days) manually reviewing the thousands of lines of script that make up your online apps. By first locating all first- and third-party scripts and the resources they access, automated content security policies can speed up the code review procedure. These policies are then generated to assist reduce the client-side attack surface.
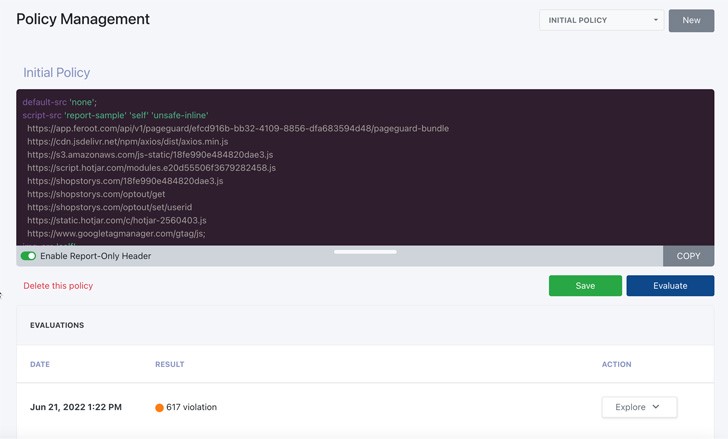
Few developers or AppSec experts assert that they prefer deploying CSPs. The CSP must initially work for a certain web application. The team must next ensure that it offers the proper level of protection. Additionally, no current widgets or plugins can clash with the CSP (or the decision must be made to not deploy the CSP or deactivate those plugins, which can cause problems in other areas, such as customer engagement, marketing, and sales).
And then, when a CSP fails, there is the dreaded audit to determine the why and where.
The problem of CSP audit avoidance, often known as death by a thousand scripts or avoiding manual code reviews, is pretty typical. Thousands of scripts are now included in client-side web applications, which are put together from various open-source libraries or other third- and fourth-party sources. A thorough record of all the scripts used in web application assembly, including their functionality, sources, and whether they have been updated or patched to address any known security problems, is rarely kept by development or security teams.
Even when teams do locate every source of a third-party script, there is no assurance that the scripts are secure. There are still problems with package managers that contain malicious, obfuscated JavaScript that harvests sensitive data from websites and web applications. In a recent instance, researchers found that unwary engineers had downloaded malicious packages 27,000 times.
Sadly, the issue of CSP audit avoidance widens a major client-side attack surface.
CSP issues are unrelated to how valuable they are. CSPs excel at delivering policy optimization and violation reporting, as well as spotting scripts that are susceptible to skimming, XSS, and JavaScript injection attacks (such as Magecart). Developers may ignore essential CSP procedures because managing manual content security controls is tedious, which raises the security risk.
Automated content security policies reduce the risk associated with human CSP monitoring and help manage CSPs to effectively secure the client-side attack surface. Businesses may accelerate the construction and administration of CSPs and enhance client-side security by identifying all first- and third-party scripts, digital assets, and the data these assets access. The domain level is where automated CSPs are maintained in order to improve reporting and version control.
To evaluate how scripts function on a web application and what kinds of data they might be accessing, automated CSPs browse a website or web application and launch synthetic users. The CSP is afterwards generated by the system in order to meet the security requirements of the website or online application. As opposed to continuously deploying CSPs in a development environment, automated CSPs operate in the actual production environment, replicate policies for quick testing, and concentrate on reducing policy violations to as little as feasible.
Incorporating log data into SIEM and other log-based data collection systems for integration into current security practises and workflows is another feature of an automated CSP. New policies can also be created after a violation is discovered to enable quick updates and address current security threats.
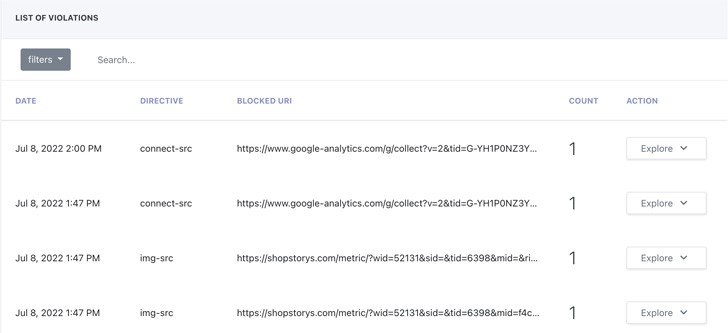
An automated CSP solution enhances existing security processes and workflows by fully integrating violation reporting. Additionally, it offers crucial assistance for legal and compliance requirements like PCI DSS 4.0, HIPAA, and others.
Securelayer7 provides DomainGuard, a specifically designed, automated CSP that reduces the complexity of managing content security policies and aids enterprises in controlling their client-side attack surface. In order to supplement current security workflows and processes and to drastically shorten the time required to develop and manage CSPs across teams, websites, and online apps, DomainGuard combines violation reporting with existing security solutions.
Reference: https://thehackernews.com/2022/07/avoiding-death-by-thousand-scripts.html





