Windows, Linux, and ESXi systems can all be used to encrypt devices that are infected with the Luna ransomware family.
Luna ransomware was found by Kaspersky security researchers thanks to a dark web ransomware forum ad picked up by the company’s active monitoring system for that threat, Darknet Threat Intelligence. Luna ransomware appears to be specifically designed to be used only by Russian-speaking threat actors.
“According to the advertisement, Luna only collaborates with affiliates that speak Russian. Additionally, there are typos in the ransom letter that is hardcoded inside the malware. As an illustration, it states “a little team” rather than “a little team,” “said Kaspersky.
Due to this, we can say with a moderate degree of certainty that the actors portraying Luna are Russian speakers.
Luna, which means moon in Russian, is a very basic ransomware programme that is currently under development and has little functionality when compared to other ransomware programmes.
However, it makes use of an uncommon encryption technique that combines the Advanced Encryption Standard (AES) symmetric encryption method with the quick and secure X25519 elliptic curve Diffie-Hellman key exchange mechanism.
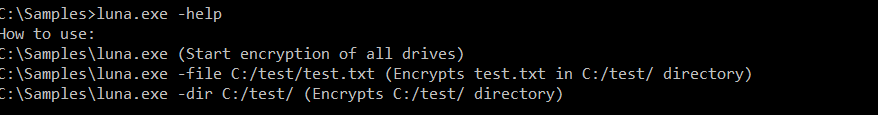
Rust-based cross-platform ransomware
Rust was used to create this new ransomware strain, and its platform independence allowed its creators to adapt it to other platforms with comparatively little source code modification.
The Luna ransomware is also able to avoid automated static code analysis attempts by utilising a cross-platform language.
“The source code used to compile the Windows version and the Linux and ESXi samples are identical. The remaining code is almost unchanged from the Windows version “the scientists added.
Luna further supports the current practise of cybercrime gangs in the development of cross-platform ransomware, which uses languages like Rust and Golang to produce malware capable of targeting several operating systems with minimal alterations.
Given that the gang has just recently been identified and its activity is still being watched, Kaspersky claims that there is very little information about what victims have had their data encrypted using Luna ransomware, if any.
Lilith, a C/C++ console-based ransomware family that targets 64-bit Windows devices, and 0mega, a new ransomware operation that targets businesses and has been active since May, are two more new ransomware families BleepingComputer revealed this month.
Before encrypting their computers to support double-extortion assaults, both are infamous for stealing data from victims’ networks.





