In Q1 2022, Spring4Shell and Veeam RCE exploits were at the top of the list. Access control weaknesses are now connected to high-severity CVEs,…
Cybersecurity Threats
Supply Chain Cybersecurity: Everyone’s Responsibility
This week, I had a conversation with a new client who revealed that they are eager to solve various internal problems relating to their…
Convergence and Adoption of AI and ML Countering the Cyber Threat
During the last few years, we have witnessed an increase in advanced cyber attacks. Cybercriminals utilize the advanced technology to breach the digital boundary…
PrivateLoader Malware Distribution Service is Blossoming in PPI Mode
The Pay-Per-Install (PPI) malware service, PrivateLoader, has been acquiring popularity in delivering a motley of malware. Usually, malware operators pay such service owners to…
RedLine malware is used by Fake Windows 11 upgrade installers
Threat actors have started dispersing fake Windows 11 upgrade installers to users of Windows 10, tricking them into downloading and running RedLine stealer malware.…
Samba-Critical Vulnerability Let Attackers Gain Remote Code Execution
A Virtual File System of Samba was found to be vulnerable to Remote Code Execution. Versions before 4.13.17 were vulnerable to this vulnerability. Samba…
Zimbra issues hotfix for XSS vulnerability under active exploitation
Attackers have targeted mailboxes in multiple waves across two attack phases. Business email platform Zimbra has released a hotfix for a cross-site scripting (XSS)…
Android Users were Targeted by Dark Herring
A fraudulent subscription campaign called Dark Herring has targeted over 100 million Android users worldwide. The campaign has been operating for almost two years.…
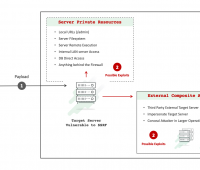
SSRF flaws created in multiple apps via Google Drive integration errors
Execution flaws in Google Drive integrations created server-side request forgery (SSRF) vulnerabilities in a mixture of applications, a security researcher has disclosed. This included…
Log4j vulnerability targets SolarWinds, ZyXEL devices
SolarWinds and ZyXEL devices are being attacked by cybercriminals who are searching for Log4jShell vulnerability aka log4j vulnerability. The devices are known to contain…