Even if a user has activated multifactor authentication, a large-scale phishing campaign using adversary-in-the-middle (AiTM) phishing sites managed to steal passwords, take over a user’s sign-in session, and bypass the authentication procedure (MFA). The attackers then carried out subsequent business email compromise (BEC) attacks against other targets using the compromised credentials and session cookies to obtain access to the impacted users’ mailboxes. According to our threat analytics, the AiTM phishing campaign has made over 10,000 attempts to target specific companies since September 2021.
Phishing is still one of the methods that attackers use the most frequently when trying to enter an organisation for the first time. Phishing is the most prevalent form of malicious email we have seen in our threat signals, and reports of phishing attacks more than doubled in 2020, according to the 2021 Microsoft Digital Defense Report. It is anticipated that more enterprises will adopt MFA, especially in nations and regions where even governments are requiring it. MFA adds an additional security layer against credential theft. Sadly, criminals are also developing new techniques for getting around this protection precaution.
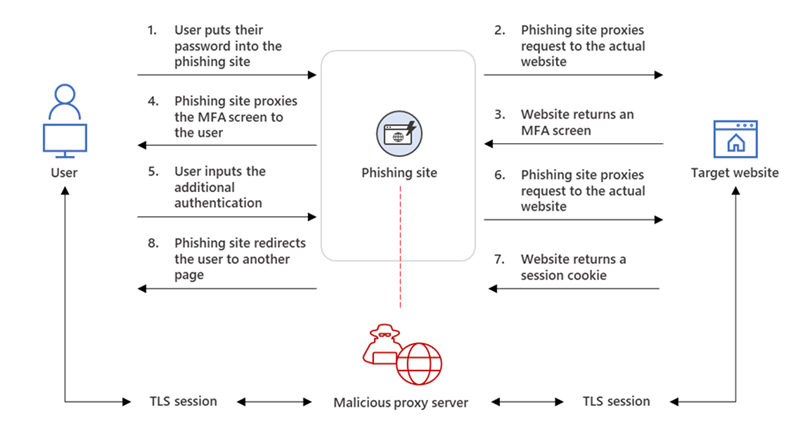
Attackers utilise a proxy server to stand between a target user and the website they want the user to visit in AITM phishing (that is, the site the attacker wishes to impersonate). An attacker might acquire and capture the target’s password as well as the session cookie, which serves as evidence of the user’s active, authenticated session with the website, with the help of such a setup. The attacker gains access to a session on behalf of the user regardless of the sign-in method the latter chooses because AiTM phishing steals the session cookie, hence it should be noted that this is not a weakness in MFA.
Here are the specifics of the Microsoft Security team’s study of the attackers’ successful effort at money fraud and phishing operation. Also gave advice on how to defend against this danger and how Microsoft security tools can find it for defenders.
How AiTM phishing works
After successful authentication, every modern web service establishes a session with the user so that they don’t need to re-authenticate each time they access a new page. After initial authentication, an authentication service provides a session cookie that is used to implement this session functionality. The session cookie serves as evidence to the web server that the user has successfully authenticated and is still actively using the website. In AiTM phishing, the attacker tries to get hold of the session cookie of the target user so they can bypass the entire authentication procedure and take action on the latter’s behalf.
To do this, the attacker sets up a web server that acts as a proxy, sending HTTP packets from users who visit the phishing site to the target server the attacker wants to impersonate and vice versa. As a result, the phishing website seems just like the legitimate one (as every HTTP is proxied to and from the original website). Additionally, unlike in traditional phishing efforts, the attacker is not required to create their own phishing website. The only obvious distinction between the legitimate website and the phishing site is the URL.
Tracking an AiTM phishing campaign
The team discovered numerous variants of an AiTM phishing effort that attempted to attack more than 10,000 companies since September 2021 using Microsoft 365 Defender threat data. These attacks impersonate the Office online authentication page to target Office 365 customers, and it appears that they are connected.
According to the study, the Evilginx2 phishing kit serves as the AiTM infrastructure for these campaign iterations. Additionally, we found patterns in their post-breach operations, such as payment frauds and the collection of private information from the target’s email.
The Process:
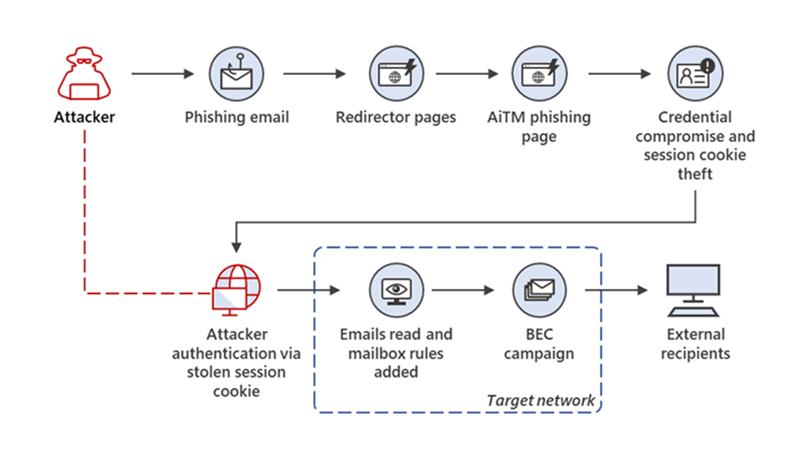
The attacker targeted numerous people in various businesses by sending emails with an HTML file attached. The email message alerted the intended recipients to a voicemail. A page telling the receiver that the voice message was being downloaded was displayed when the recipient viewed the associated HTML file in their browser. But take note that no MP3 file was fetched because the download progress bar was hardcoded in the HTML file. Instead, the page sends the user to a site that acts as a redirector. To make sure the intended user was coming from the original HTML attachment, this redirector served as a gatekeeper. To accomplish this, it first checked to see if the expected fragment value—in this example, the user’s email address encoded in Base64—was present in the URL. This page concatenated the value on the phishing site’s landing page, which was likewise encoded in Base64 and saved in the “link” variable if the specified value was present.
The next phishing landing page enhanced its social engineering lure by merging the two values, which immediately filled up the sign-in page with the user’s email address. Additionally, the effort attempted to block traditional anti-phishing software from directly visiting phishing URLs by using this strategy.
The phishing site proxied the organization’s Azure Active Directory (Azure AD) sign-in page, which is typically login.microsoftonline.com. If the organization had configured their Azure AD to include their branding, the phishing site’s landing page also contained the same branding elements.
Post-breach BEC
A payment fraud plan is one in which an attacker deceives a fraud target into sending money to accounts that belong to the attacker. It can be accomplished, among other things, by intercepting and responding to active email threads about finances in the mailbox of the stolen account and tricking the fraudulent target into sending money via phoney invoices.
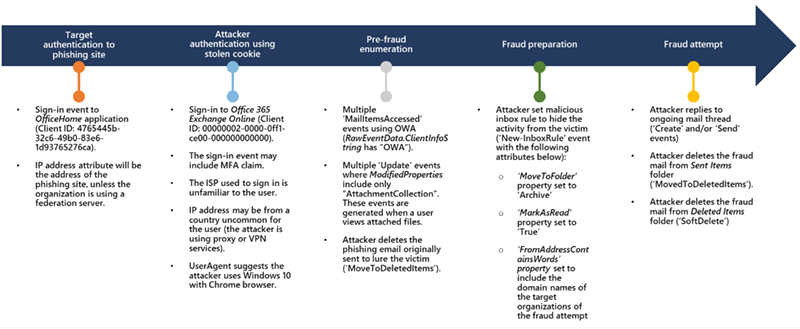
Based on the research of Microsoft 365 Defender threat data and the assessment of associated threat warnings from the clients it was found that an attacker may have started their follow-on payment fraud as soon as five minutes after stealing credentials and access to a session. According to the observations, the attacker used the stolen session cookie to sign in to Outlook online after a compromised account first entered the phishing website (outlook.office.com). Multiple times, the cookies contained an MFA claim, indicating that the attacker utilized the session cookie to access the system on behalf of the compromised account even though the business has an MFA policy in place.
Conducting payment fraud
The attacker started replying to active email threads about payments and bills between the target and employees of other firms as soon as the rule was set, as specified in the generated Inbox rule. Then, the attacker removed their responses from the Deleted Items and Sent Items folders of the hacked account.
After the initial scam attempt, the attacker periodically signed in to see if the victim of the fraud had responded to their emails. In several cases, the attacker and target had email correspondence for a short time. They replied to the target and then removed the replies from the Archive folder. Their emails were also removed from the Sent Items folder.
On one occasion, the attacker used the same hacked mailbox to carry out several simultaneous fraud attempts. The attacker updated the Inbox rule they developed to include the organisation domains of each new fraud victim they discovered.
Below is a summary of the campaign’s end-to-end attack chain based on threat data from Microsoft 365 Defender:
Defending against AiTM phishing and BEC
This AiTM phishing campaign is another another illustration of how threats change in reaction to the security measures and procedures put in place by enterprises to protect themselves from potential assaults. Furthermore, given that many of the most destructive attacks from last year made use of credential phishing, we anticipate that such efforts will increase in size and sophistication.
Despite the fact that AiTM phishing tries to go around MFA, it’s important to stress that MFA adoption is still a crucial pillar of identity security. MFA is still quite efficient at thwarting a wide range of threats, which is why AiTM phishing initially appeared. By implementing MFA with systems that enable Fast ID Online (FIDO) v2.0 and certificate-based authentication, businesses can make their implementation “phish-resistant.”





