A team of researchers has disclosed information on a fresh flaw in Intel CPUs that lets attackers steal encryption keys and other sensitive data from the processors.
The vulnerability, known as ” ÆPIC Leak,” is the first of its type to architecturally reveal private information in a way that resembles an “uninitialized memory read in the CPU itself.”
The academics stated that “PIC Leak is an architectural bug: the sensitive data gets directly released without relying on any (noisy) side channel, in contrast to transient execution assaults like Meltdown and Spectre.”
Researchers from Amazon Web Services, the Graz University of Technology, the Sapienza University of Rome, and the CISPA Helmholtz Center for Information Security carried out the study.
The Advanced Programmable Interrupt Controller (APIC), which offers a way to receive and route hardware interrupt signals in a scalable manner, is the source of the vulnerability (CVE-2022-21233, CVSS score: 6.0), which affects CPUs with the Sunny Cover microarchitecture.
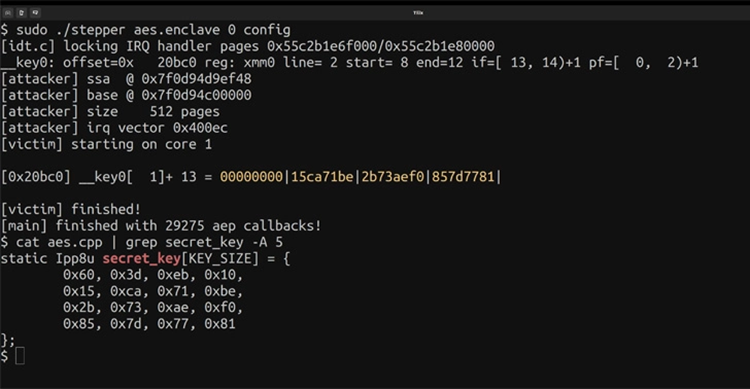
The memory-mapped registers of the local Advanced Programmable Interrupt Controller (APIC) were found to be improperly initialized by the scan of the I/O address space on Intel CPUs based on the Sunny Cove microarchitecture, the researchers reported.
“As a result, reading these registers architecturally produces outdated information from the microarchitecture. These registers enable reading of any data transported between the L2 and the last-level cache.”
AES and RSA keys from secure enclaves that execute on the same physical CPU core are leaked from systems using Intel’s trusted execution environment (TEE), also known as Software Guard eXtensions (SGX), with a success rate of 94% and 74%, respectively.
The security guarantees provided by SGX, according to Intel, are “by safeguarding selected code and data from alteration, developers can split their application into hardened enclaves or trusted execution modules to assist boost application security.”
Simply put, the flaw invalidates the aforementioned guarantees, making it possible for an attacker with the necessary rights to run privileged native code on a target machine in order to obtain the private keys and, even worse, to undermine attestation, a key component of the security primitives used in SGX to ensure the integrity of code and data.
Intel has responded to the discovery with firmware patches and has labeled the problem as a medium-severity vulnerability resulting from incorrect isolation of shared resources that allows information to be revealed through local access.
It’s also important to note that Intel has now discontinued support for SGX on its client CPUs, despite the fact that a slew of attack techniques, including SGX-ROP, MicroScope, Plundervolt, Load Value Injection, SGAxe, and VoltPillager, have afflicted the technology lately.
SQUIP Side Channel Attack Affects AMD CPUs
The development follows the discovery of the first-ever side channel attack (CVE-2021-46778) on AMD Zen 1, Zen 2, and Zen 3 microarchitecture scheduler queues, which might be exploited by an adversary to recover RSA keys.
Scheduler Queue Usage via Interference Probing, or SQUIP, is the abbreviation for the attack, which involves measuring the contention level on scheduler queues in an effort to potentially gather sensitive data.
However, the chipmaker has advised software developers to “use current best practices, including constant-time algorithms and avoiding secret-dependent control flows when applicable.” No security upgrades have been published to remedy the line of attack.





