A new Go-based botnet has been discovered scanning and brute-forcing self-hosted internet sites powered by WordPress content management systems (CMS) in order to gain control of targeted systems. New GoTrim Botnet Attempts to Gain Access to WordPress Site Admin Accounts.
“This new brute forcer is part of a new campaign we’ve decided to name GoTrim because it is authored in Go and uses ‘:::trim:::’ to divide data. It divides conveyed to and from the C2 server. They explained Fortinet FortiGuard Labs scientists Eduardo Altares, Joie Salvio, and Roy Tay.
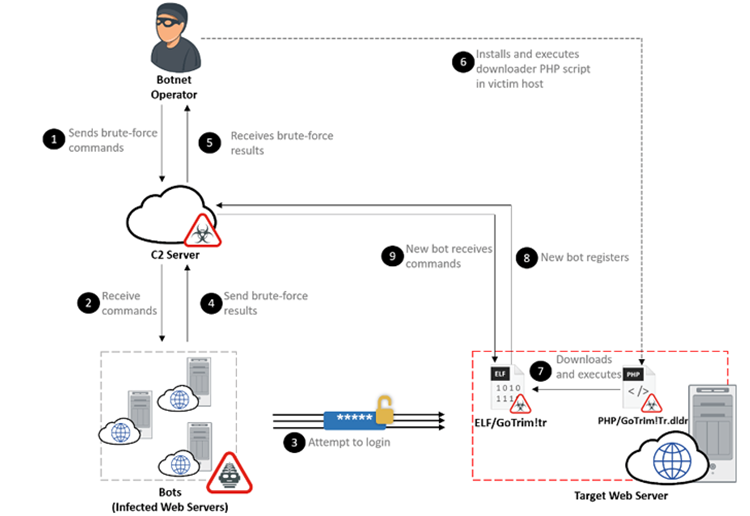
The active campaign observed since September 2022. It employs a bot network to launch dispersed brute-force threats in an attempt to obtain access to the targeted web server.
Following a successful break-in, the operator will install a downloader PHP script in the newly compromised system, which will then utilize the “bot client” from a hard-coded URL, probably adding the device to the network consisting.
GoTrim does not have self-propagation functionality in its current form, nor can it disseminate other ransomware or maintain perseverance in the compromised device.
The malware’s primary goal is to receive additional commands from an actor-controlled server, such as trying to conduct brute-force threats against WordPress and OpenCart to use a set of provided user login details.
The GoTrim Way
GoTrim can put another way function in a server mode where it begins a domain controller to listen for requests from the malicious attacker through the command-and-control (C2) server. This, however, happens only when the compromised system is directly hooked up to the internet.
Another distinguishing feature of the botnet ransomware is its ability to imitate user requests from the Firefox Browser 64-bit Windows. In order to circumvent anti-bot defenses, as well as solve CAPTCHA barriers present in WordPress sites.
Also, read Attackers Look For Weak Plugins on 1.6 Million WordPress Sites.
Although this malware is still in development. The fact that it contains a perfectly functioning WordPress brute forcer coupled with its anti-bot evasion techniques. It helps make it a threat to keep an eye on,” the researchers wrote.
“Brute-forcing campaigns are risky because they can result in server-negotiated settlement and malware deployment. To reduce this risk, website admins should make sure that user accounts (particularly administrator accounts) have strong passwords.”





